Github OpenID Setup
Warning
Be mindful when configuring OpenID providers that are public. Any user that can successfully authenticate with the provider will have access to your deployment of Kasm Workspaces. While access to Kasm Workspace apps and desktops can be resitricted with Kasm group permissions, any user of the public authentication provider would still be able to login to your deployment of Kasm. It is recommended to use a private OpenID provider unless your intention is to allow authentictioned access to all users of the OpenID platform provider.
This guide walks through a basic setup allowing Github users to authenticate with your Kasm deployment
Note
Github OpenID does not support OIDC Single Logout.
Reference Docs:
Creating a Github OAuth App
Login to Github and select Settings from the profile dropdown: https://github.com/settings/profile
Select Developer Settings.
Select OAuth Apps, then click New OAuth App.
Give the application a name (e.g
Kasm), enter the URL of the deployment in the Homepage URL, and the Authorization callback to behttps://<deployment hostname>/api/oidc_callback.
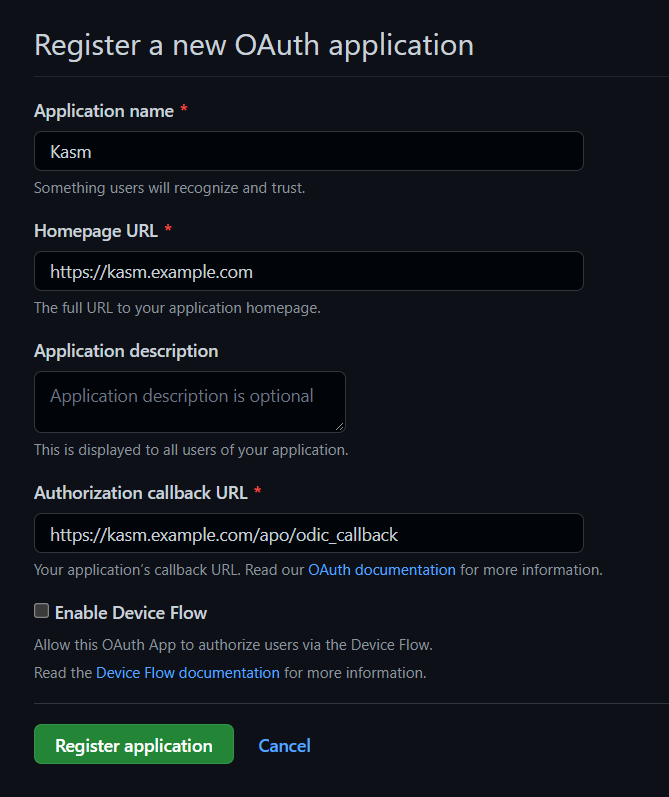
New OAuth Application
Select Register Application.
On the next page note the Client ID. It will be needed for upcoming configurations.
Click Generate a new client secret and note the value. It will be needed for upcoming configurations.
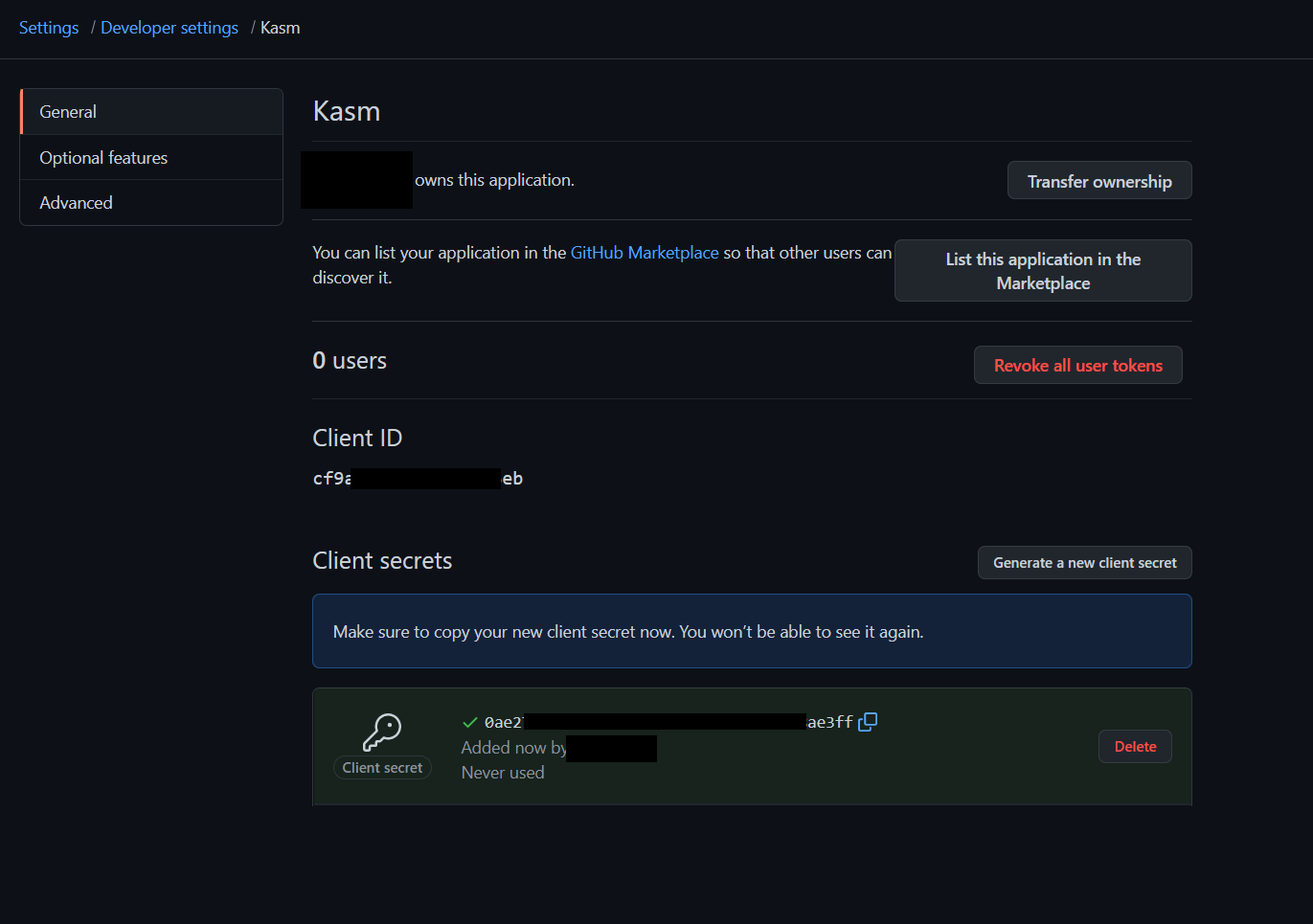
Client ID an Client Secret
Kasm OpenID Config
Log into the Kasm UI as an administrator.
Select Access Management -> Authentication -> OpenID -> Add Config.
Update the form with the following entries, using the Client ID and Client Secret gathered in the previous section.
Property |
Value |
Enabled |
Checked |
Display Name |
Continue with Github |
Logo URL |
|
Auto Login |
Unchecked |
Hostname |
<Empty> |
Default |
Checked |
Client ID |
<Client ID From Github OAuth App> |
Client Secret |
<Client Secret from Github OAuth App> |
Authorization URL |
|
Token URL |
|
User Info URL |
|
Scope |
|
Username Attribute |
|
Groups Attribute |
<Empty> |
Debug |
Unchecked |
Redirect URL |
|
OpenID Connect Issuer |
Blank |
Logout with OIDC Provider |
Unchecked |
Enable OIDC SLO Frontchannel Endpoint |
Unchecked |
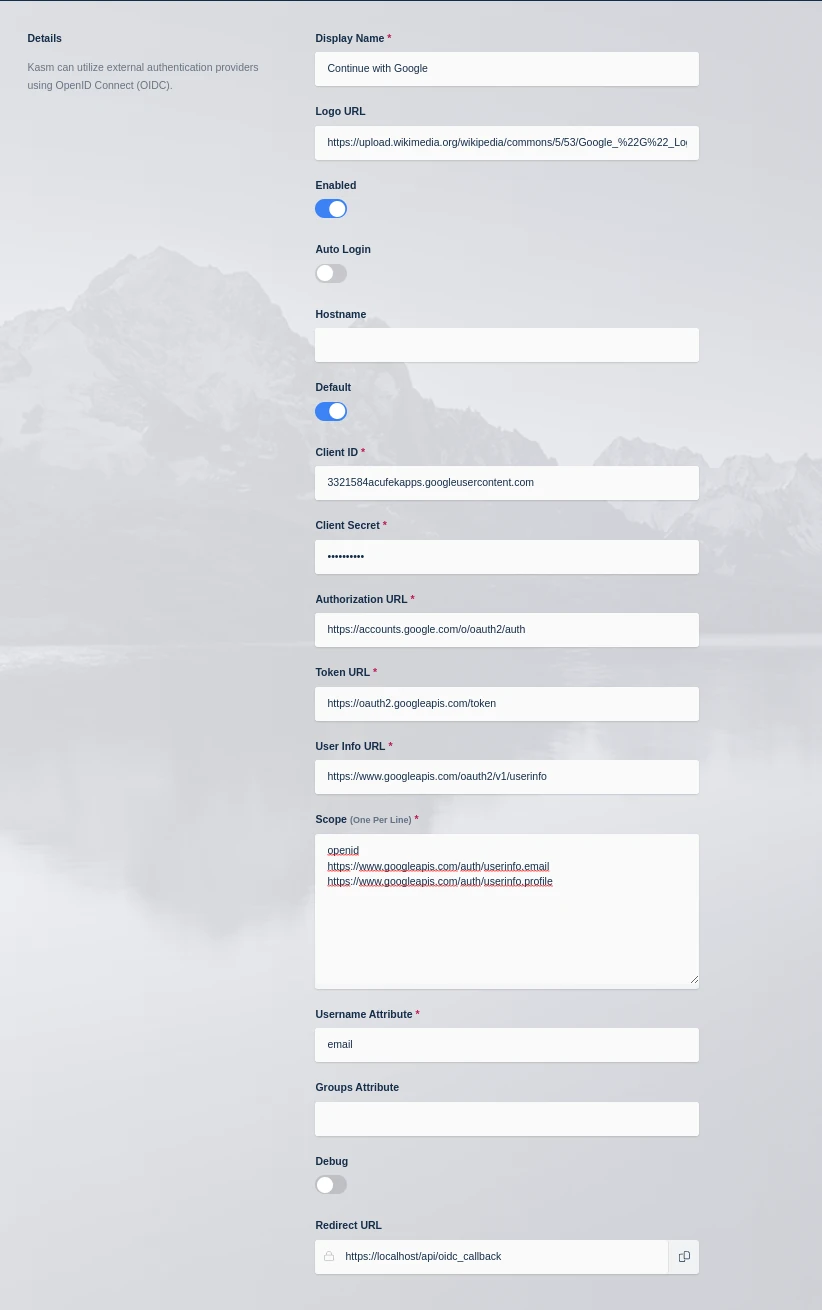
Kasm OIDC Configurations
Click Save to save the changes.
Github Login Test
Logout of the Kasm to display the login screen. The OpenID configuration should be shown.
Login Screen
Click Continue with Github.
The user is redirected to Github. Login if necessary. The first time the user utilizes the OpenID auth, they will be prompted to accept the access requested. Select Authorize
Github Auth
Upon compleation, the user is logged into the Kasm app.