JumpCloud
This example assumes the use of JumpCloud LDAP-as a Service with the following configurations.
A User Group named Kasm Users that is bound to LDAP. Only users that are members of this group should be allowed to authenticate to Kasm
Users named kasm-user-1 and kasm-admin-1 are a member of this group.
A User Group group named Kasm Admins that is bound to LDAP. Users that are a member of this group will be placed in Kasm’s Administrators group
A user named kasm-admin-1 is a member of this group.
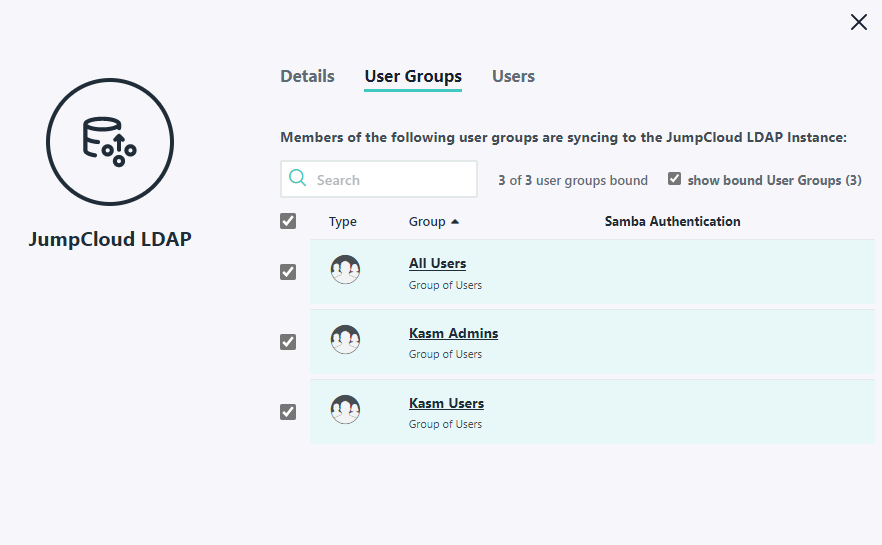
LDAP Groups
A user account named kasm-ldap-svc is configured as an LDAP Binding User
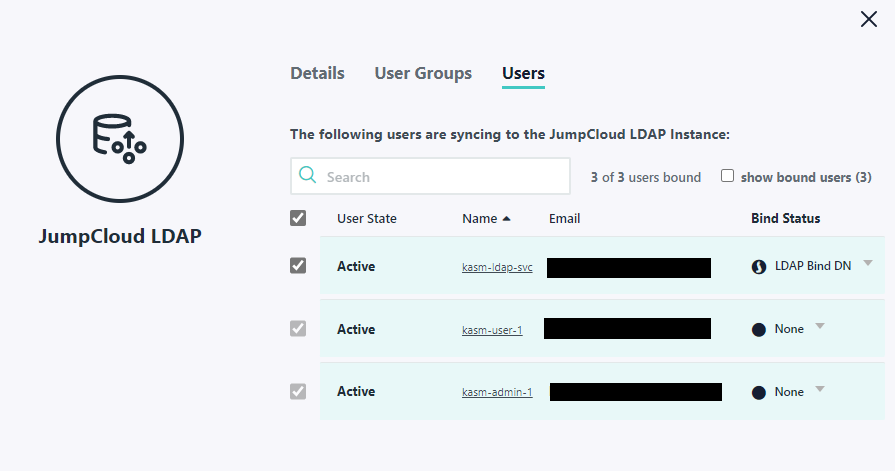
LDAP Users
Kasm LDAP Configuration
Log into the Kasm Web UI as an administrator
Click Access Management -> Authentication -> LDAP
Click on Add Configuration
Enter the following information , substituting the example Organization ID
633df00190c6d619236d3ae1with your own.
Property |
Value |
Name |
JumpCloud |
URL |
ldaps://ldap.jumpcloud.com:636 |
Search Base |
ou=Users,o=633df00190c6d619236d3ae1,dc=jumpcloud,dc=com |
Search Filter |
&(objectClass=inetOrgPerson)(uid={0})(memberOf=cn=Kasm Users,ou=Users,o=633df00190c6d619236d3ae1,dc=jumpcloud,dc=com) |
Group Membership Filter |
(&(objectClass=groupOfNames)(member={0})) |
Email Attribute |
|
Service Account DN |
uid=kasm-ldap-svc,ou=Users,o=633df00190c6d619236d3ae1,dc=jumpcloud,dc=com |
Service Account Password |
password |
Search Subtree |
Checked |
Auto Create App User |
Checked |
Enabled |
Checked |
LDAP Group Mapping
The following settings can be used to map the JumpCloud Kasm Admins group to the Kasm Workspaces build in Administrators Group.
See Create LDAP linked Group for more details.
Settings for the SSO Group Mapping screen
Property |
Description |
SSO Provider |
LDAP - Kasm Test LDAP Settings |
Assign All Users |
Unchecked |
Group Attributes |
cn=Kasm Admins,ou=Users,o=633df00190c6d619236d3ae1,dc=jumpcloud,dc=com |
Verifying Configurations
Verify you can log into the Workspaces UI with user. kasm-user-1@jumpcloud.com.
Verify you can log into the Workspaces UI with user. kasm-admin-1@jumpcloud.com. Once authenticated the user should now have access to administrative functions within the app.
Attempting to log into Workspaces as any other user that is NOT a member of the JumpCloud Kasm Users group should not succeed.
Helpful References
https://support.jumpcloud.com/support/s/article/using-jumpclouds-ldap-as-a-service1
https://support.jumpcloud.com/support/s/article/filtering-by-user-or-group-in-ldap-search-filters1
https://support.jumpcloud.com/support/s/article/using-ldapsearch-with-jumpcloud1
https://support.jumpcloud.com/support/s/article/user-attributes-2019-08-21-10-36-47