VMware Workspace ONE SAML Setup
Create a new SAML configuration in Kasm
Log into the Kasm UI as an administrator.
Select Access Management -> Authentication -> SAML -> Add Configuration
The SAML 2.0 Configuration page will auto-generate the Entity ID, Single Sign On Service, Single Logout Server, and Relay State values.
Check Enable and enter a Display Name. e.g (Workspace One)
Update the following Settings
Setting |
Value |
Group Member Attribute |
groupNames |
NameID Attribute |
emailAddress |
Want Attribute Statement |
Unchecked |
Want Message Signed |
Checked |
Want Name ID |
Checked |
Leave this page open and continue to the next steps.
Add a new SaaS Application
Open the Workspace One Access Admin Console and select the Catalog tab, then select New.
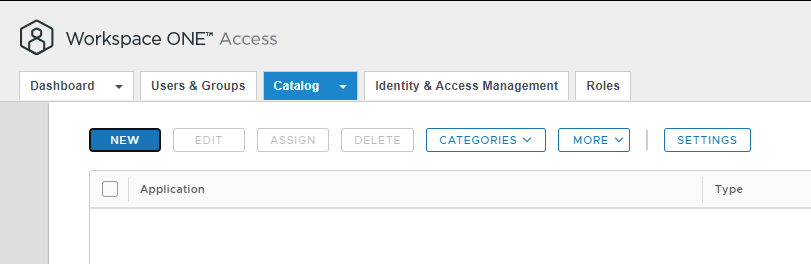
Workspace One Access Portal
In the New SaaS Application dialogue, enter a Name (e.g Kasm) and optionally a Description and Icon. Select Next.
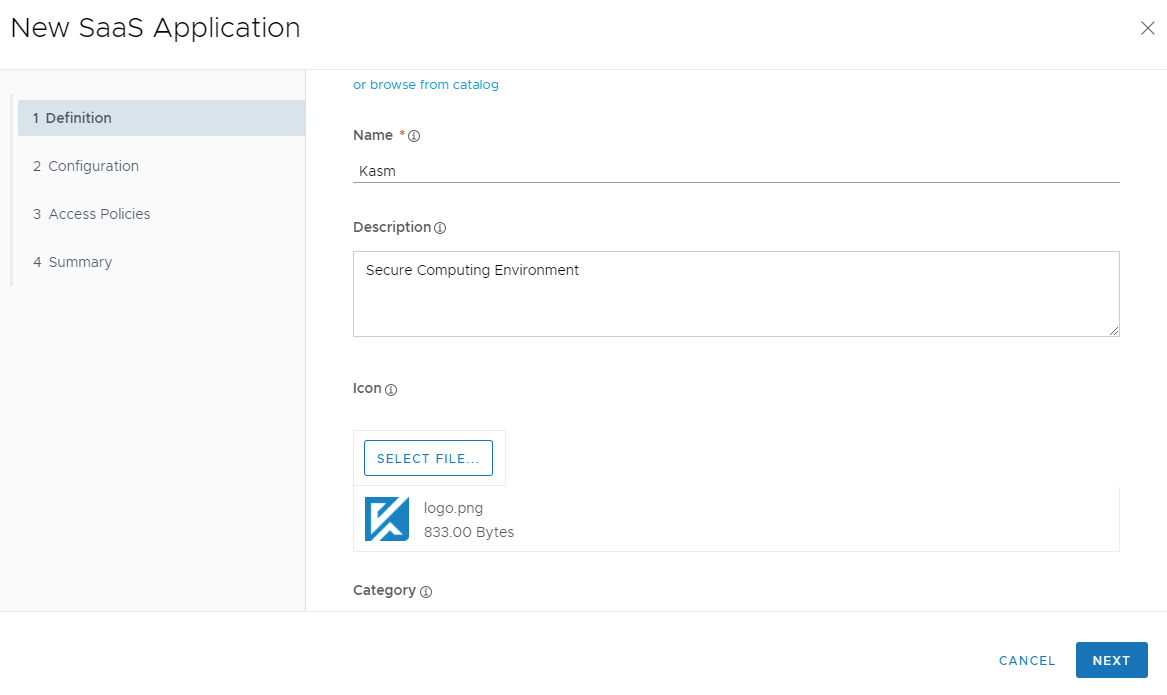
New SaaS Application Definition
Select SAML 2.0 as the Authentication Type and select Manual for the Configuration.
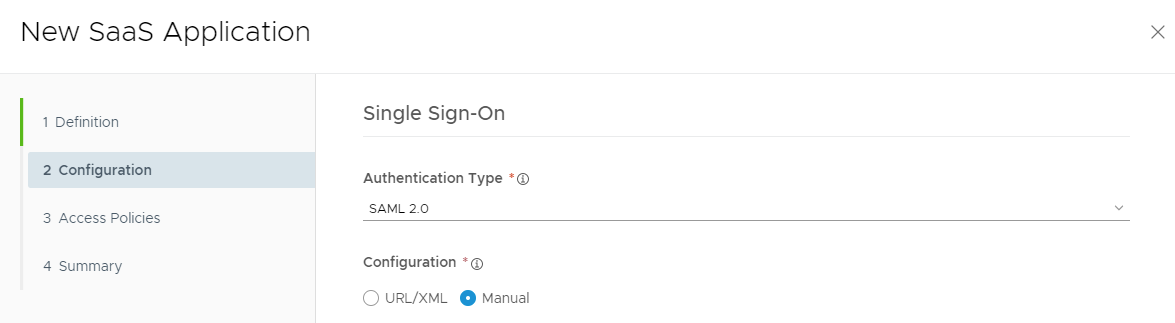
Authentication Type
Copy the following values from the Kasm SAML Configurations started in the previous section into the New SaaS Application form.
Workspace One Property Name |
Kasm Property Name |
Single Sign-On URL |
Single Sign On Service |
Recipient URL |
Single Sign On Service |
Application ID |
Entity ID |
Relay State URL |
Relay State |
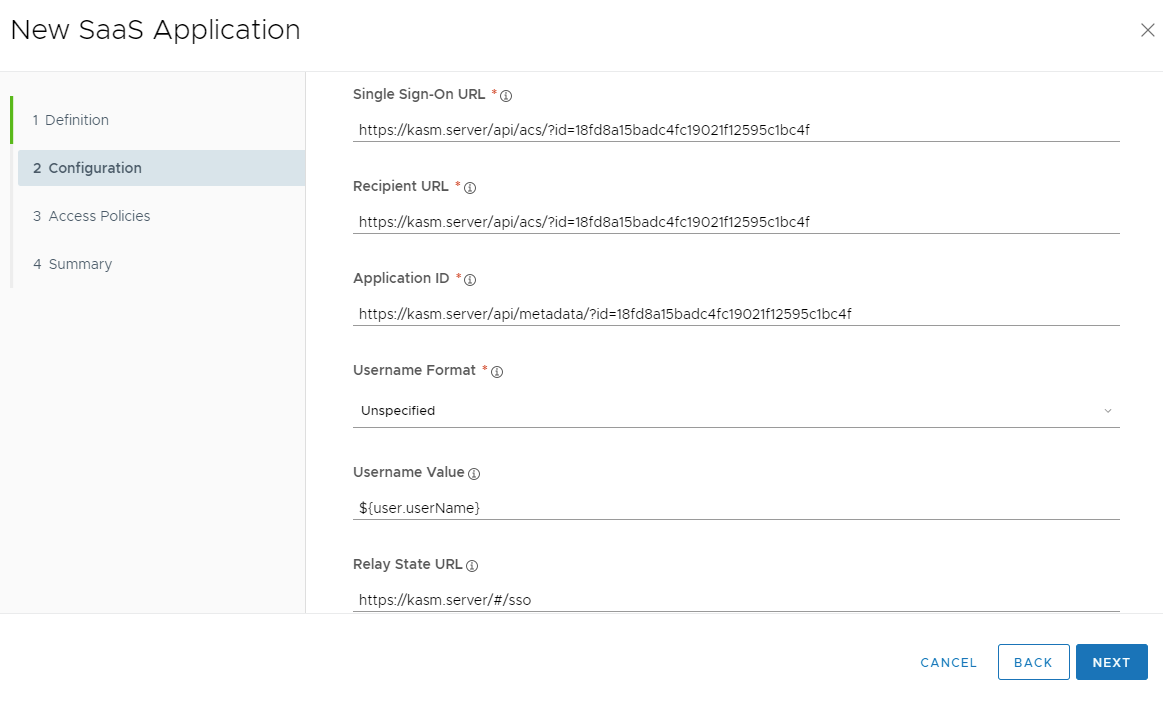
SAML URL Configuration
Select Email Address as the Username Format.
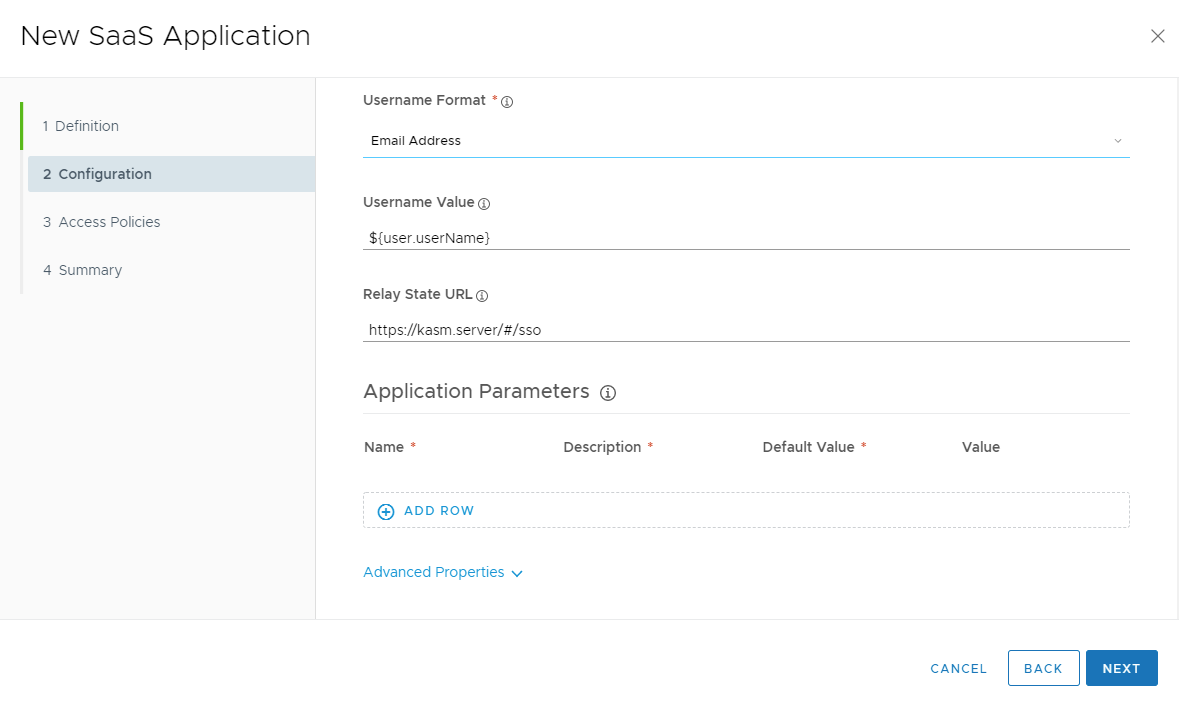
Username Format
Click Advanced Properties. Scroll down to the Custom Attribute Mapping section. Add an entry with the following information then click Next
Attribute |
Value |
Name |
groupNames |
Format |
Basic |
Namespace |
<blank> |
Value |
${groupNames} |
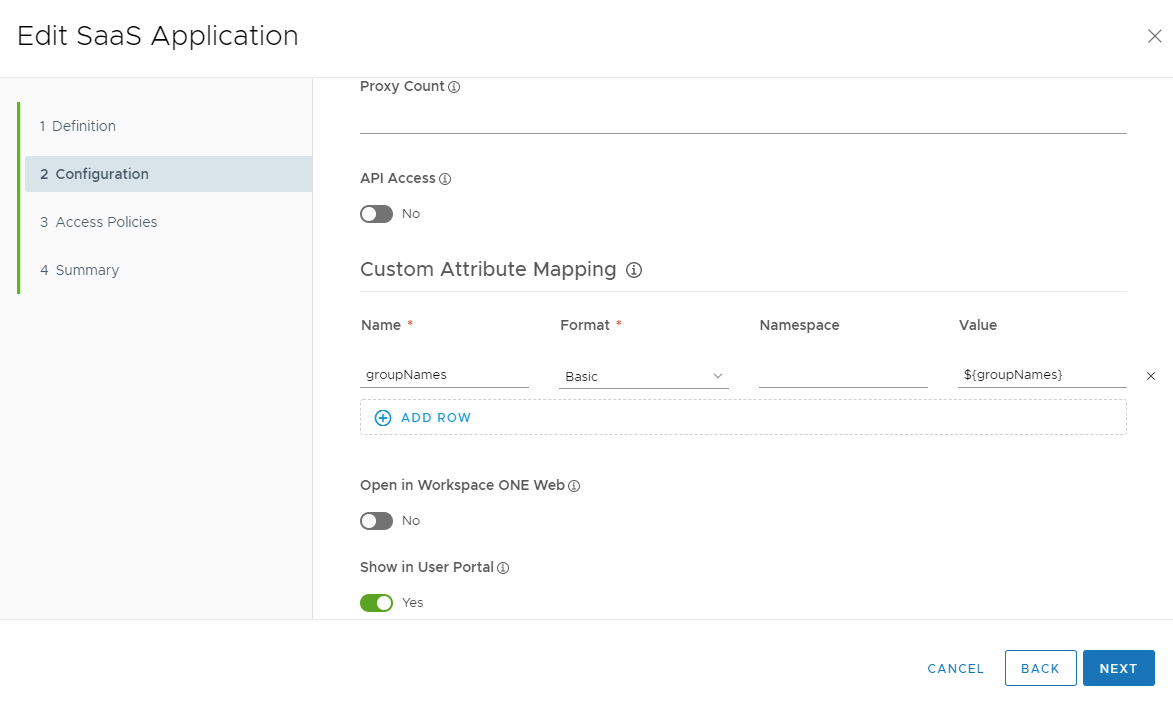
Group Names
Select a desired Access Policy. In this example we will use the default_access_policy_set. Select Next.
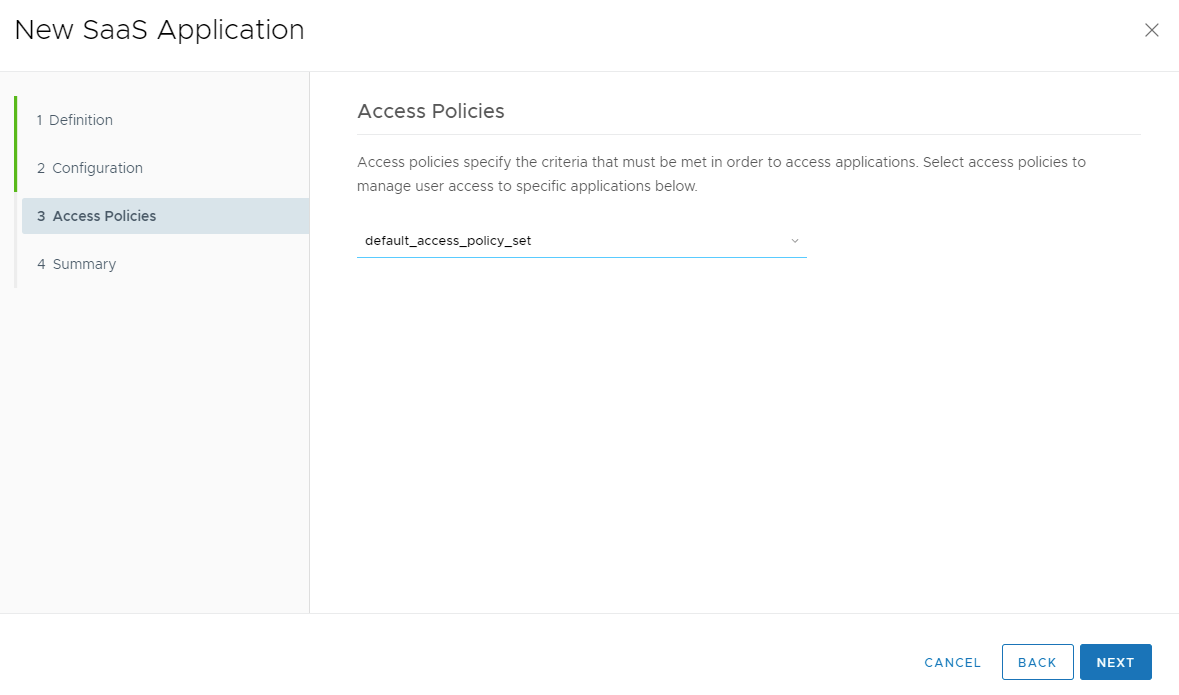
Access Policies
Review the configuration then select Save & Assign.
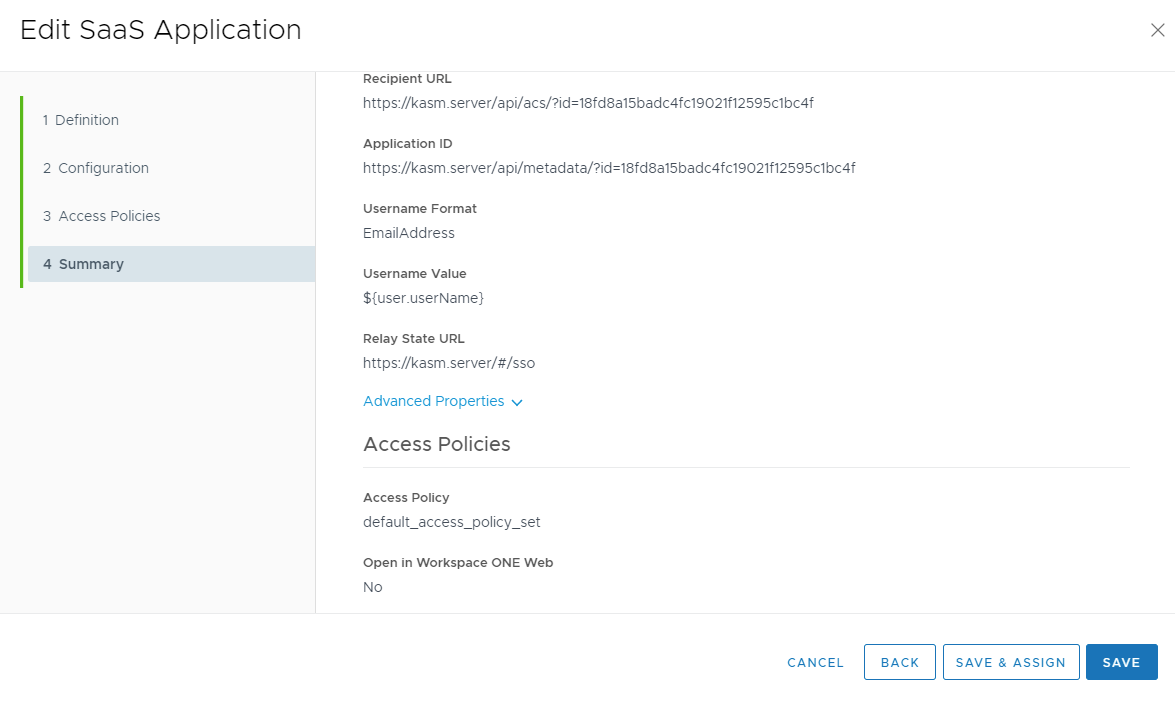
Review Configuration
In the Assign dialogue, type in the desired user or group. In this example the ALL USERS group is used. Select Save
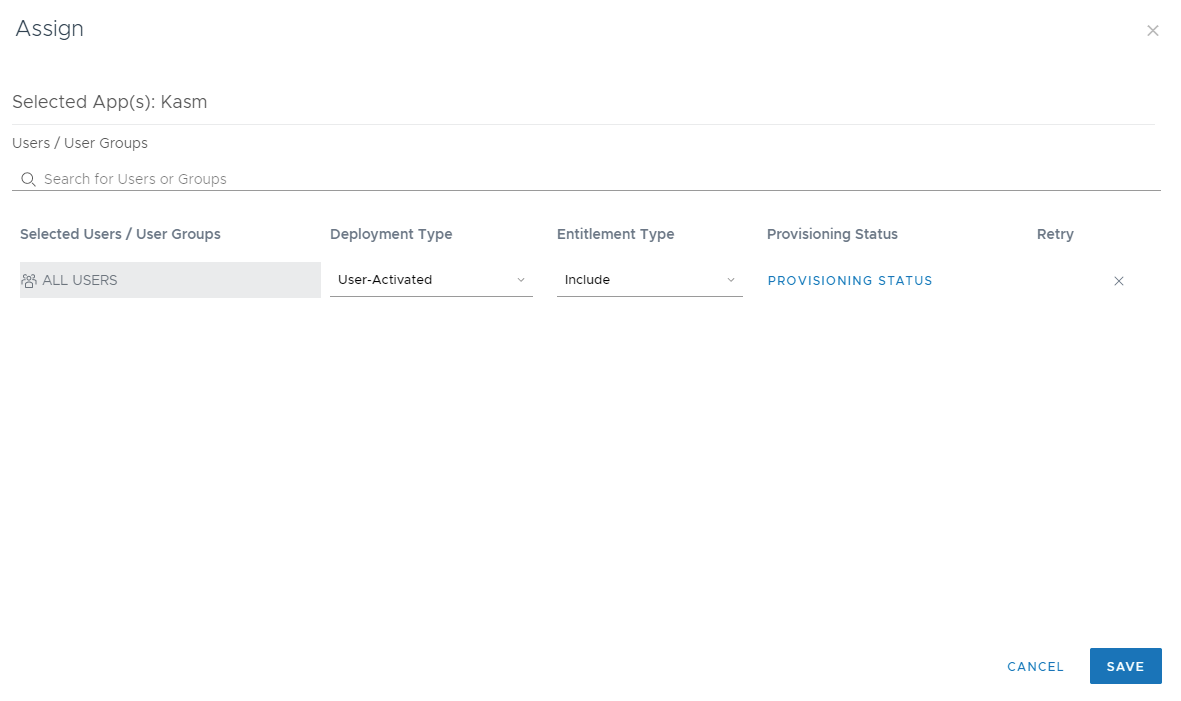
Assign Users/Groups
From the Catalog tab of the Workspace ONE Access panel, select Settings.
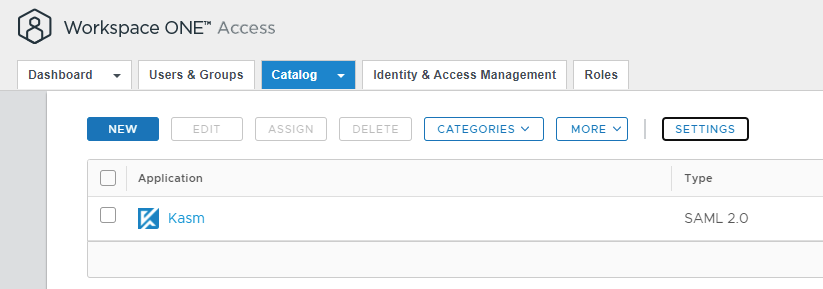
Settings
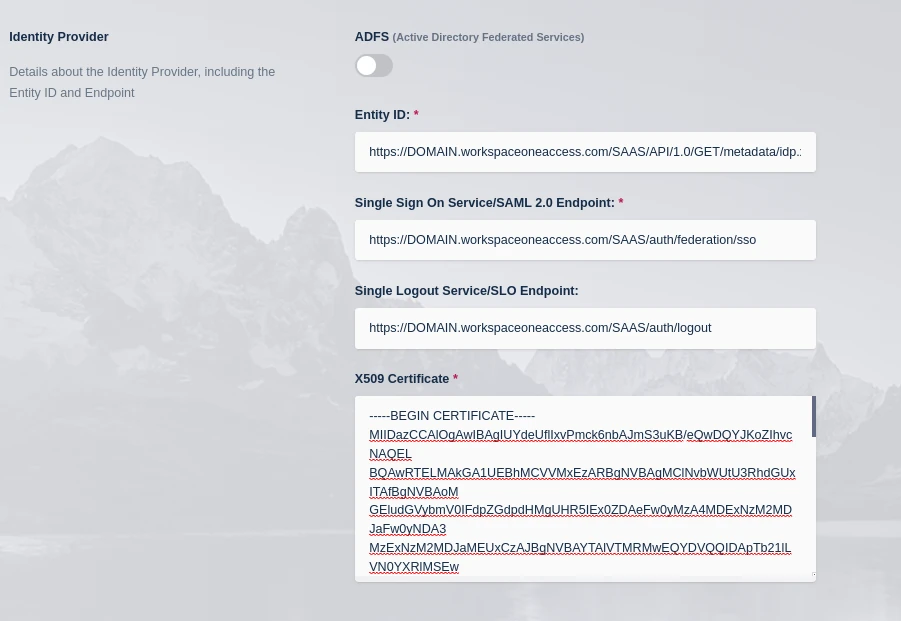
Select SAML Metadata. Copy the contents of the Signing Certificate into X509 Certificate field under Identity Provider in the Kasm SAML Configurations started in the prior section.
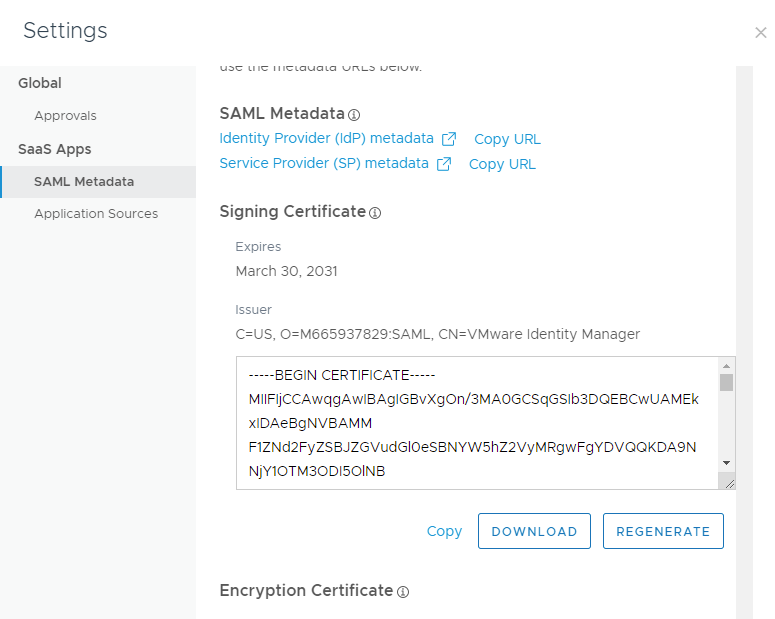
Signing Certificate
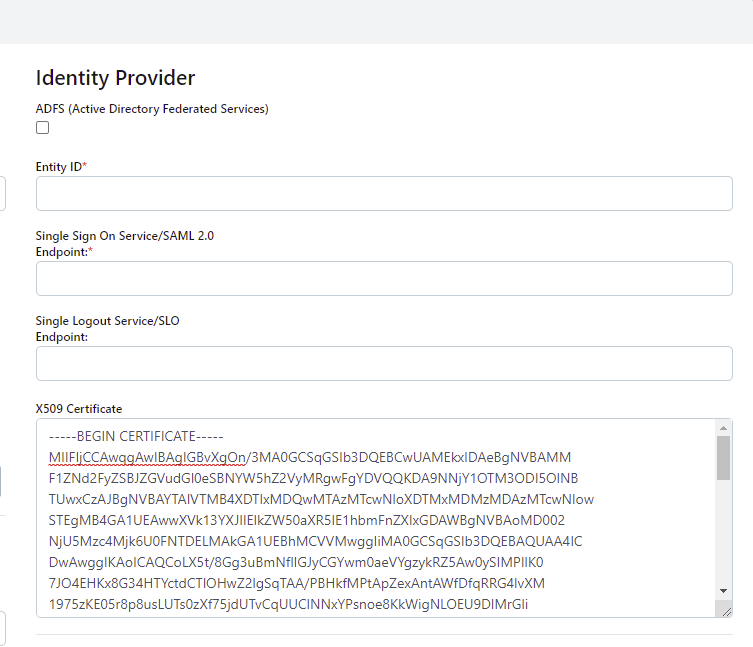
Configuring Signing Certificate
Back in the Settings dialogue, click Identity Provider (IdP) metatdata.

Certificate
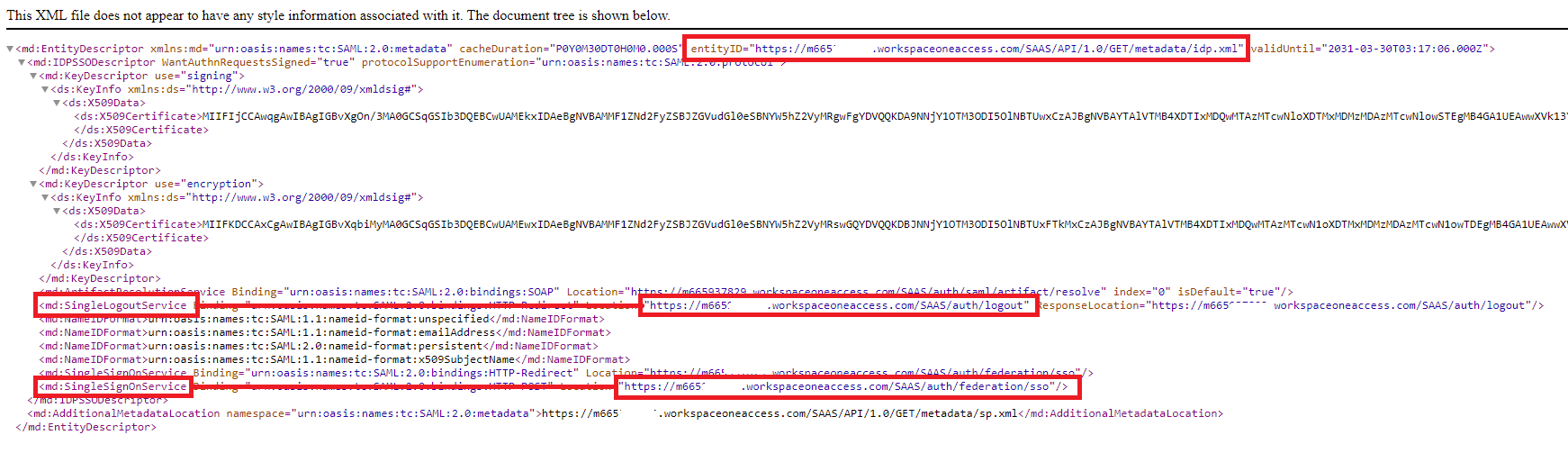
An XML metatdata file will be shown. Copy the highlighted sections into Identity Provider fields in the Kasm SAML Configurations started in the prior section. Once complete click Submit
Workspace One Property Name |
Kasm Property Name |
entityID |
Entity ID |
SingleSignOnService |
Single Sign On Service/SAML 2.0 Endpoint |
SingleLogoutService |
Single Logout Service/SLO Endpoint |
Metadata
SAML Configuration
Testing Access
Log out of the Kasm UI if already logged in.
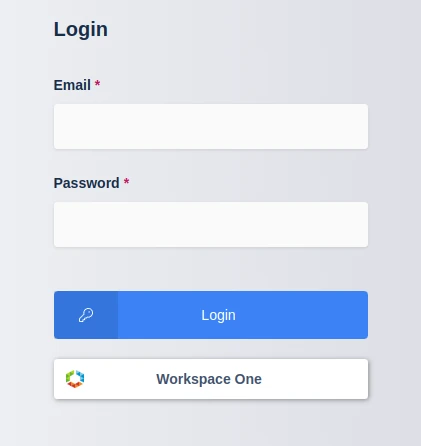
Navigate to the Kasm UI login page.
Kasm Login
Click Workspace One to initiate the SAML SSO process.
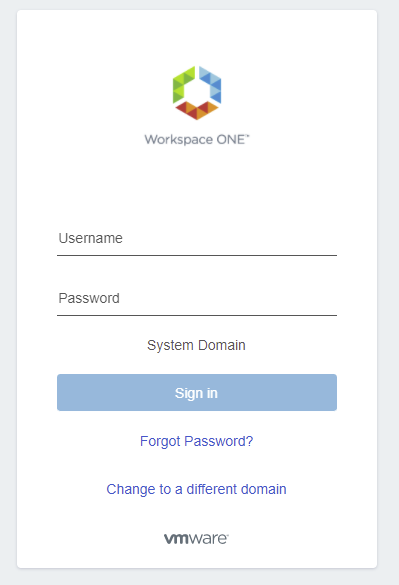
VMware Login
After logging in, you should be redirected to the Kasm UI Dashboard
From another browser, login to Workspace ONE Access. Kasm should be displayed as an App. You may click the link to automatically open and log in to Kasm
Workspace One Access
Group Mappings
In the prior steps, Workspace One was configured to pass along the group names the user is a member of in the SAML assertion. This can be used to automatically map users into Groups within the Kasm application.
The following assumes a group is created in Workspace named Accounting
Log into the Kasm UI as an administrator.
Select Access Management -> Groups, the select Create New Group
Give the Group a Name (Does not need to match the Workspace ONE Group Name) and Priority
Click Save to create the new group.
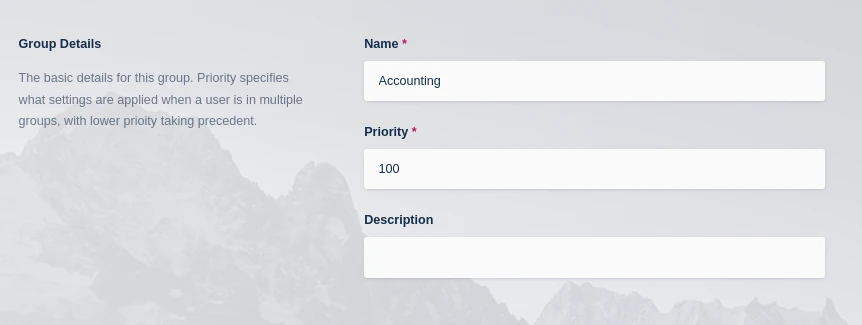
Create Group
Select Access Management -> Groups, then using the arrrow menu click Edit next to the group just created.
Navigate to the SSO Group Mapppings tab and select Add SSO Mapping.
Select the SAML IDP that was created above e.g. “SAML - Workspace One” for the SSO Provider.
Enter the Workspace ONE Group Name in the Group Attributes field. Click Submit
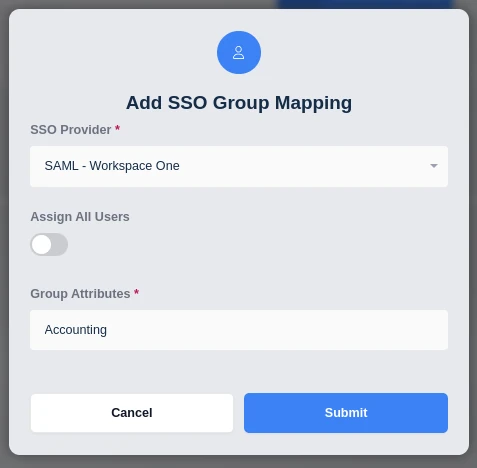
Add SSO Group Mapping
The next time a user of the Accounting group logs in they will automatically become a member of this Kasm Group.