Okta SAML Setup
Follow the steps in the Okta application setup.
Some of the Okta SAML settings fields displayed blow require information from the Kasm SAML configuration page.
Okta SAML Settings
Go To Kasm’s SAML configuration
Select Add Configuration
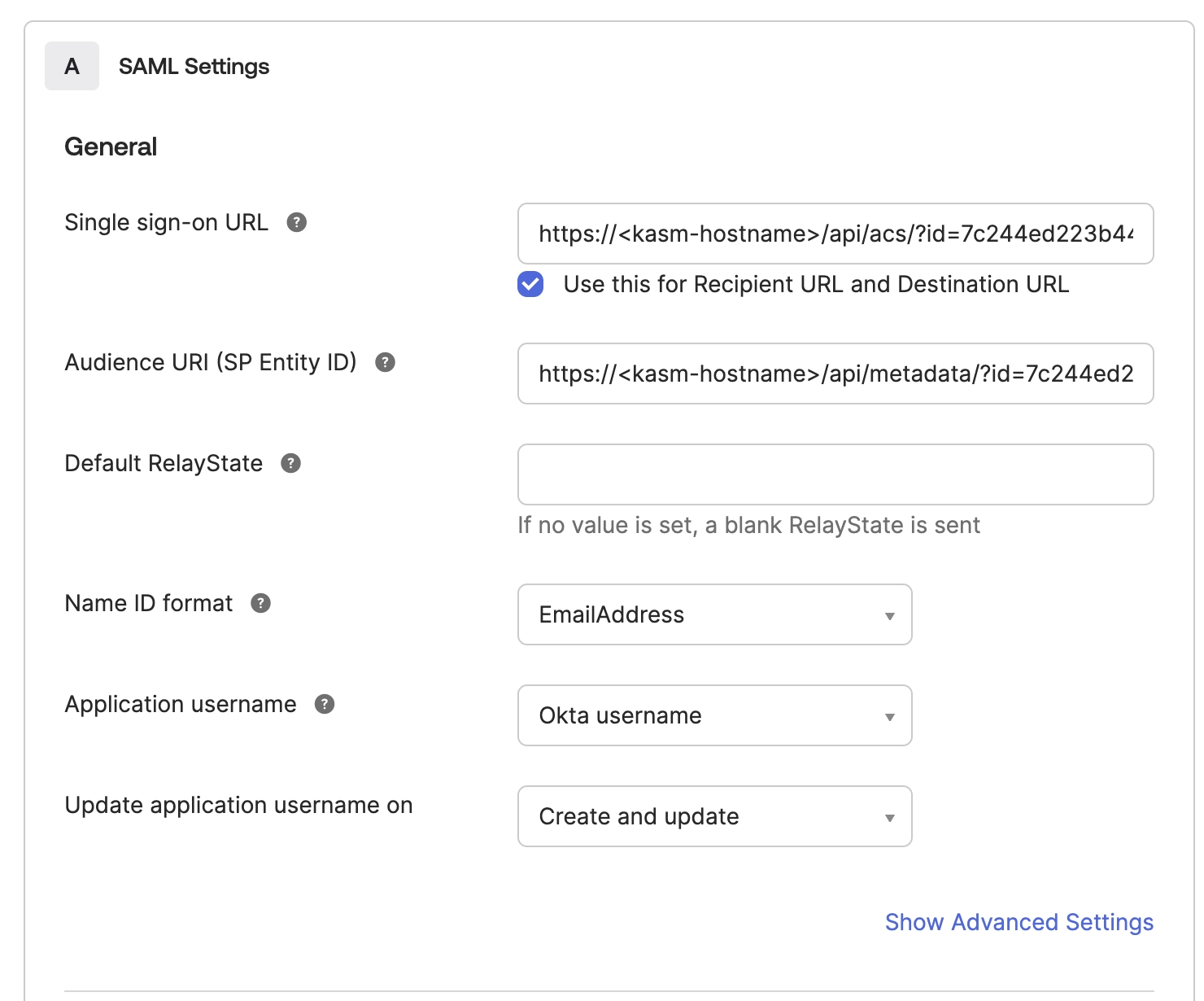
Fill out the Okta Configuration form from the Kasm Information:
Copy the “Single Sign on Service” from the Kasm configuration page to the “Single sign-on URL” field in Okta
Copy “Entity ID” from the Kasm configuration page to the “Audience URI (SP Entity ID)” field in Okta
Change Name ID format to EmailAddress
Optionally advanced settings can be set here and the Single Logout Service could be configured
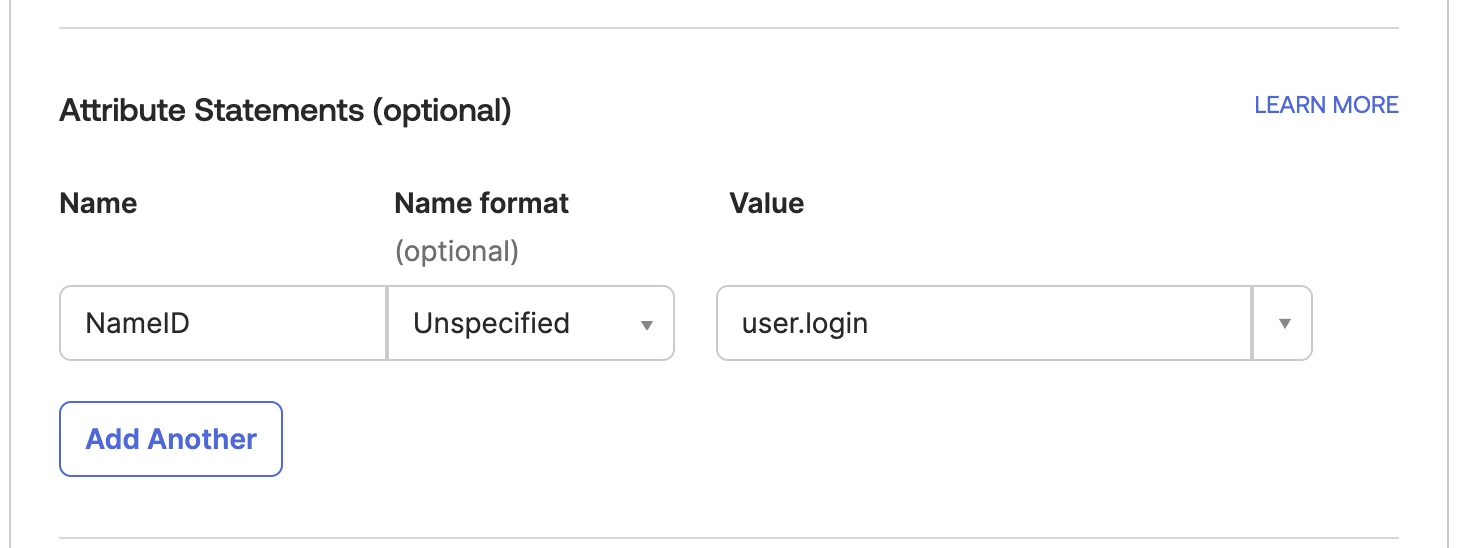
Kasm SAML currently requires attributes to be returned in the SAML response unless security option wantAttributeStatement is false
Add the setting below to ensure that Okta sends the username attribute in the SAML response.
Okta SAML Attributes
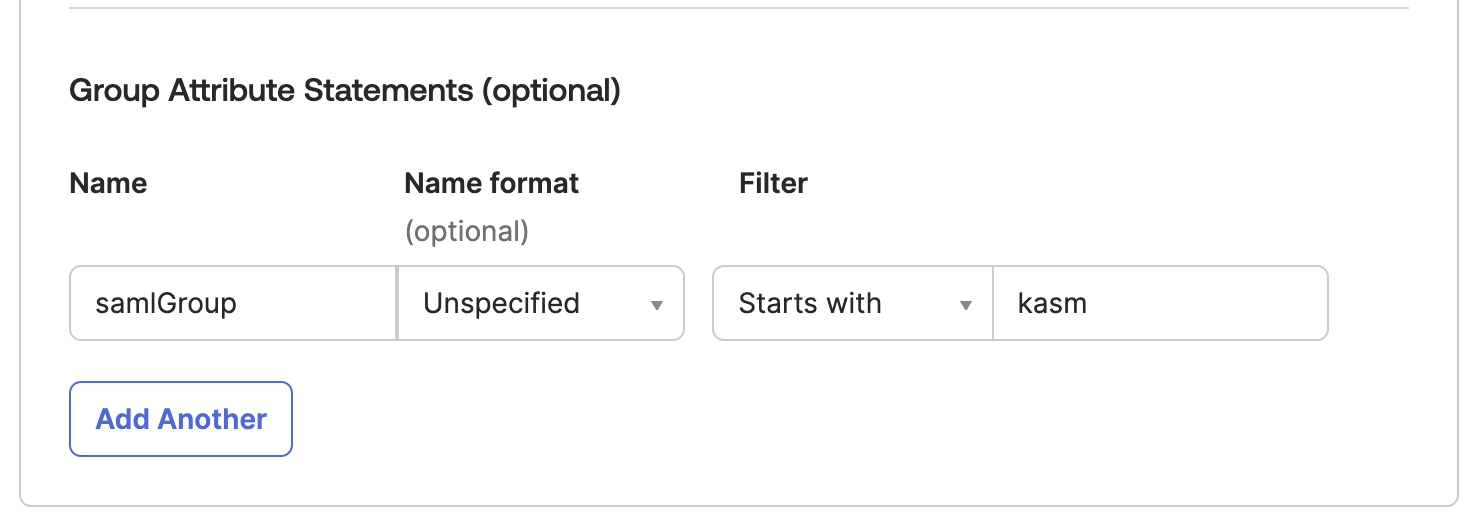
Okta can be configured to send over group membership information to Kasm in order for Kasm to assign groups based on Okta groups. In the example below Okta will send over all groups the user is a part of that start with “kasm” via the “samlGroup” attribute in the SAML Response. The Kasm “Group Member Attribute” setting must be configured to match this Okta setting.
Add the setting below if you wish Okta to send group information to Kasm
Okta Group Settings
Select next and add an internal app.
Once created navigate to the the Sign On configuration page in Okta and click on “View SAML Setup Instructions” on the right side of the page.
Copy the following fields from this Okta page into the corresponding fields of the Kasm Saml Configuration page.
Copy the “Identity Provider Single Sign-On URL” from Okta to the “Single Sign On Service/SAML 2.0 Endpoint” in the Kasm Identity Provider configuration
Copy the “Identity Provider Issuer” in Okta to the “Entity ID” in the Kasm Identity Provider configuration
Copy the “X.509 Certificate” in Okta to the “X509 Certificate” in the Kasm Identity Provider configuration
Then in Okta assign a user to the application in the Okta Configuration.
In Kasm Select the “Test SSO” button at the bottom of the configuration form to perform a test of the SSO configuration.
Users should now be able to select Okta as an authentication method in the sign-on page.