Groups
Groups are used to define roles for specific sets of users in Kasm Workspaces. By default there are two groups created by the system, the Administrators group and the All Users group, the All Users group is the default group for every user where statewide settings can be set.
Groups can be used to specify Kasm images and settings for different sets of users. For example, you may have a custom image for developers with pre-installed developer tools. You can tie that image to a group. You can define settings for that group, such as enabling bi-directional clipboard.
Create Group
Steps to create individual groups for sections of users.
Select Access Management > Groups tab from navigation menu
Select Add Group from the top right of the table
Specify Group properties listed below
Group Properties
Name |
Provides the name of the group |
Description |
Provides the description of the group |
Priority |
Sets the priority of the settings over other groups |
Is System |
System level group that cannot be deleted |
Note that group name and priority number must be unique. For help identifying what group priority numbers are available, use the Filters tool in the Group view to sort by Priority.
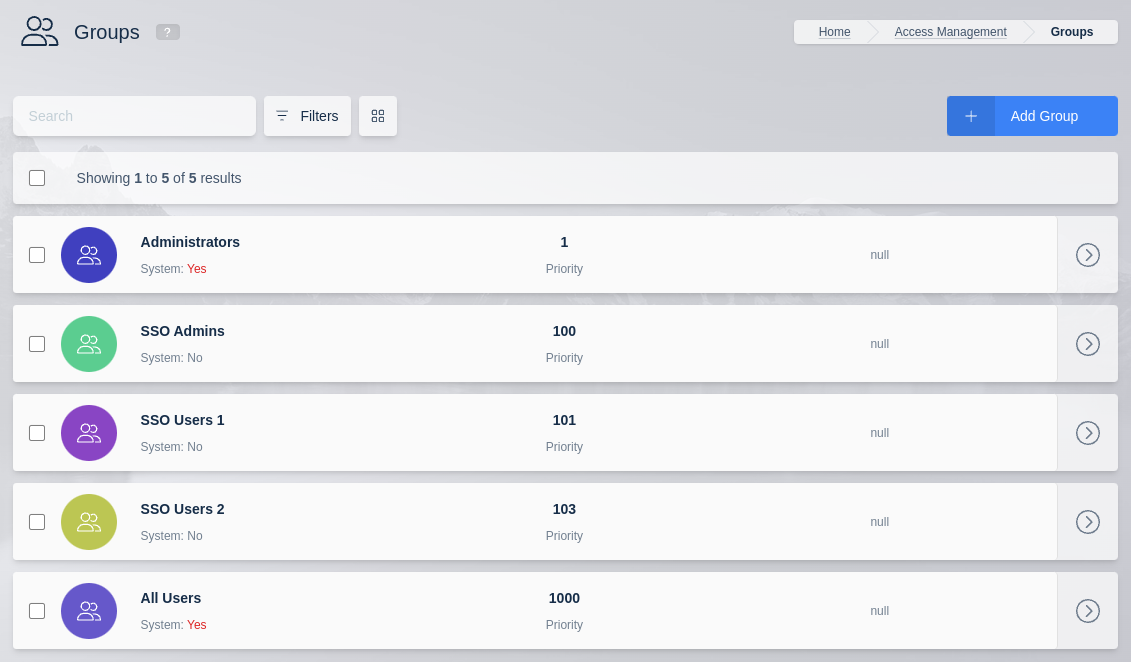
Sort by Priority
There is a Users tab in the edit group page that allows for the selection of its users.
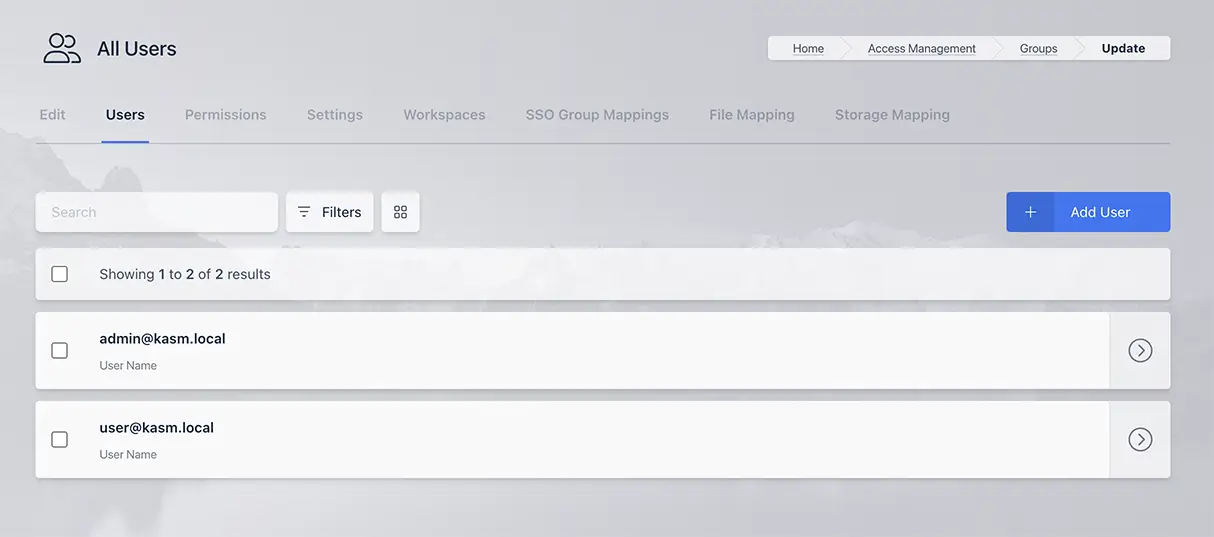
Users in Group
Group Settings
Group settings may be changed for the specific group by selecting the groups tab, clicking the edit icon on the desired group and the Add Settings button in the Group Settings card. There are delete setting and edit setting icons to the right of the Setting. If a user belongs to mulitple groups, the setting on the group with the lowest priority takes effect. For settings like volume_mapping, all settings are combined from all groups a user is a member of.
Here is a video that has an overview Groups and Group settings.
To configure group settings:
Log into the UI as an administrator.
Select Groups
Next to the desired group select View from the actions menu.
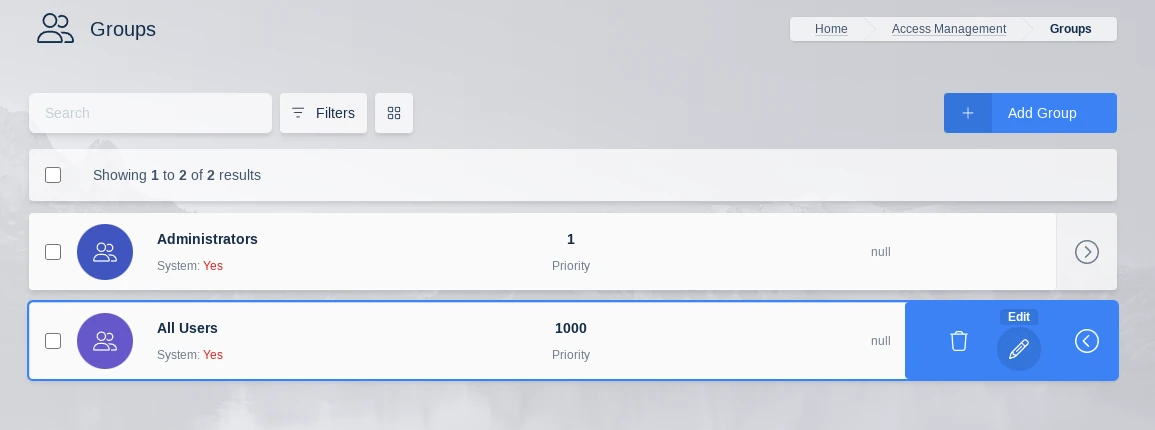
Edit Group
Scroll down to the Group Settings panel. Update settings as desired.
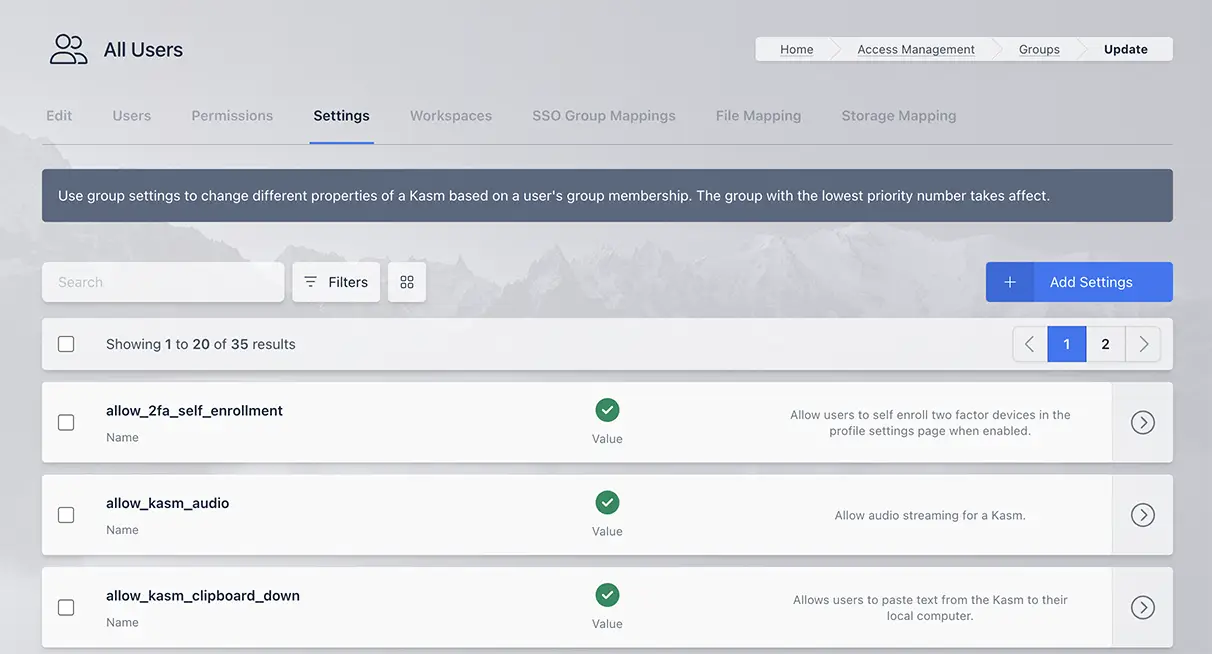
Group Settings
allow_2fa_self_enrollment |
Allow users to self enroll two factor devices in the profile settings page when enabled. |
allow_kasm_audio |
Allow audio streaming for a Kasm. |
allow_kasm_clipboard_down |
Allows users to paste text from the Kasm to their local computer. |
allow_kasm_clipboard_seamless |
Allows users to copy and paste text without using Kasm control panel. This feature is only available on Chrome and Chromium-based client browsers |
allow_kasm_clipboard_up |
Allow users to paste from their local computer to the Kasm. |
allow_kasm_delete |
If enabled, users are allowed to delete their running sessions. |
allow_kasm_downloads |
Allow users to download files from a Kasm. On RDP local client workspaces this has no effect see allow_kasm_rdp_client_file_transfer_clipboard. |
allow_kasm_gamepad |
Allow users to pass local gamepads into the Kasm session. See Gamepad Passthrough for more details. |
allow_kasm_microphone |
Allow microphone passthrough to a Kasm. When enabled, users can pass their local microphone through to the Kasm session. On RDP local client workspaces this only works with desktop editions of Windows. |
allow_kasm_rdp_client_file_transfer_clipboard |
This setting only applies to RDP client Kasm sessions. In RDP file transfers are part of the clipboard and independent directional control of file transfers is not possible. This setting will enable file transfer in the directions that text clipboard has been enabled via allow_kasm_clipboard_down and allow_kasm_clipboard_up. |
allow_kasm_rdp_map_local_drives |
Allow sessions using the RDP Gateway to map client local drives into the RDP target. This setting is an all or nothing setting. When enabled it will map all client drives into the rdp session. |
allow_kasm_rdp_smart_card_passthrough |
Allow sessions that use the RDP Gateway or web native client(on ChromeOS) to pass smart cards through to the RDP target. This setting is required for smart card auth to RDP sessions using Smart Card Passhtrough. |
allow_kasm_rdp_webauthn_passthrough |
Allow sessions using the RDP Gateway to pass webauthn requests from the RDP target to the client. This only works for Windows clients running the builtin mstsc.exe RDP client. |
allow_kasm_webcam |
Allow webcam passthrough to a Kasm. When enabled, users can pass their local webcam through to the Kasm session. On RDP local client workspaces this only works with desktop editions of Windows. |
allow_kasm_printing |
Allow printing of documents using local printers |
allow_kasm_pause |
If enabled, users are allowed to pause their running sessions. |
allow_kasm_sharing |
Allow the user to share access to their session with other users. See Session Sharing for more details. |
allow_kasm_stop |
If enabled, users are allowed to stop their running sessions. |
allow_kasm_uploads |
Allow users to upload files to a Kasm. On RDP local client workspaces this has no effect see allow_kasm_rdp_client_file_transfer_clipboard. |
allow_persistent_profile |
Allow the use of persistent profiles if configured on the Workspace. See Persistent Profiles for details |
allow_point_of_presence |
Allow the user to use point of presence features for certain Workspaces. |
allow_totp_2fa |
Allow for TOTP tokens (e.g.: Google Authenticator) to be used as a two factor authentication method for the group. |
allow_user_storage_mapping |
When enabled the user is allowed to configure their own Storage Mappings via their profile. When disabled, new user configurations will not be allowed, nor will using any previously configured mappings be allowed when new sessions are created. |
allow_webauthn_2fa |
Allow for WebAuthn devices (e.g. YubiKeys) to be used as a two factor authentication method for the group. |
allow_zone_selection |
Allow the user to specify the deployment zone when creating a session. A dropdown will appear on the user dashboard with the available Zones. Auto represents the default behavior which is to provision in current Zone. If a Zone is specified, the request will not search alternate zones if no resources are available in the requested Zone. |
auto_add_local_user |
When enabled, local users will automatically be added to this group when created and upon each authentication. |
auto_login_to_kasm |
Sends users directly to kasm using default workspace after login |
chat_history_messages |
The number of chat history messages to show when a new user connects to a shared Kasm. Set this value to 0 to disable showing chat history. |
control_panel. advanced_settings. show_game_mode |
Whether the game mode option is present in the advanced menu on the Kasm Session control panel. |
control_panel. advanced_settings. show_ime_input_mode |
Whether the ime input mode option is present in the advanced menu on the Kasm Session control panel. |
control_panel. advanced_settings. show_keyboard_controls |
Whether the keyboard controls option is present in the advanced menu on the Kasm Session control panel. |
control_panel. advanced_settings. show_pointer_lock |
Whether the pointer lock option is present in the advanced menu on the Kasm Session control panel. |
control_panel. advanced_settings. show_prefer_local_cursor |
Whether the prefer local cursor option is present in the advanced menu on the Kasm Session control panel. |
control_panel.show_fullscreen |
Whether the fullscreen option is present on the Kasm Session control panel. |
control_panel. show_delete_session |
Whether the delete session option is present on the Kasm Session control panel. |
control_panel. show_display_manager |
Whether the display manager is present on the Kasm Session control panel. The display manager allows the user to add and remove additional displays. |
control_panel.show_logout |
Whether the logout option is present on the Kasm Session control panel. |
control_panel. show_return_to_workspaces |
Whether the return to workspaces option is present on the Kasm Session control panel. |
control_panel. show_streaming_quality |
Whether the show streaming quality workspaces option is present on the Kasm Session control panel. |
control_panel.pwa_install_option |
Whether the user must be presented with the option to install per-workspace PWAs. |
dashboard_redirect |
If configured, standard users will be redirected to the defined external website instead of being shown the main dashboard screen. |
default_image |
The default Workspace used when the /go url is called. This is also used for the auto_login_to_kasm setting. The system will create a Workspace if one does not exist. If the user already has a Workspace, the session is resumed |
default_ui_language |
The default UI language to set for the group. This is applied at next user login and is also overridden if the user sets the language in their profile. |
display_ui_errors |
If enabled, detailed information will be displayed on the client browser in the event of an error. |
enable_ui_server_logging |
If enabled, log messages will be sent from client browser to the Kasm Workspaces server. |
expose_user_environment_vars |
Expose KASM_USER and KASM_USER_ID environment variables inside the Kasm. |
idle_disconnect |
Disconnect the Kasm connection if idle for this long. Time specified in minutes. |
inject_ssh_keys |
When enabled the system will inject the user’s SSH public and private keys into new sessions automatically. Users can update their keys via the Profile. |
kasm_audio_default_on |
Default to audio enabled on Kasm start |
kasm_ime_mode_default_on |
Default to IME enabled on Kasm start |
keepalive_expiration |
The number of seconds a Kasm will stay alive unless a keeplive request is sent from the client. |
keepalive_expiration_action |
The action the system should take when a session expires according to the keepalive_expiration.
Valid options are |
keepalive_interval |
The number of seconds in between keepalive requests from the client when the user is actively in a session. |
lock_sharing_video_mode |
Locks video quality to static resolution of 720p when sharing is enabled. Recommended for best performance. |
max_kasms_per_user |
The maximum number of simultaneous sessions a users is allowed to provision. |
max_user_storage_mappings |
The maximum number of Storage Mappings a user is allowed to have registered to their account. |
read_only_user_storage_mappings |
When enabled, any storage mappings configured on the user account will be forced to read-only. |
require_2fa |
Enables two factor authentication for group. Users will be prompted to set Key on next log on. |
run_config |
Specify arbitrary docker run params. The settings for run_config on a group will override the run_config settings on an image. See Docker Run Config for more details |
session_time_limit |
The amount of time (in seconds) a session will automatically expire. A countdown timer will be displayed to the user. |
staged_session_language_and _timezone_preference_override |
When launching a workspace Kasm will by default try to match the user language and timezone to a staged session. If a staged session does not exist that has the matching language and timezone then Kasm will create a new session with the specified language and timezone. If the override is set to true then Kasm will use a staged session for the selected workspace even if the language and timezone do not match. This overrides the user setting in the user profile. |
usage_limit |
Limits the total number of hours a user or group can have running sessions. See the usage_limit documentation below for more details.
|
volume_mapping |
Map a local server directory to Kasm. Details available in the Volume Mapping Guide |
web_filter_policy |
Enabled web filtering and sets the Web Filter Policy to be used. Policies can also be set or force disabled on Workspaces. Policies assigned to Workspaces take priority over those defined via Group Settings. |
Session Time Limits
There are a multiple settings in the table above that control Kasm session lifetime. We will go into more detail about them and their relationship to each other below:
keepalive_expiration
This can also be described as the session timeout. This value determines how long Kasm will wait before destroying, stopping or pausing a session if no keepalive is received from the client. Keepalives are sent whenever a user is connected to a Kasm session even if the user is not actively using the Kasm Session.
This value should be at least twice the keepalive_interval. This setting is 1 hour by default in the “All Users Group”. The action taken is determined by the
keepalive_expiration_action Group Setting.
keepalive_expiration_action
Administrators can decide what happens to sessions once they expire. Valid options are:
delete- The session is destroyed.pause- The session is paused, preserving the disk, process and memory state. Paused sessions will still consume resources in physical memory and/or swap. Sessions resumed from a paused state will still have the previous programs launched and active. This action is valid for container-based sessions only. All other types will utilize thedeleteaction.stop- The session is stopped, preserving the disk state. Sessions resumed from a stopped state will have the previous files intact, but previously running programs will need to be restarted. This action is valid for container-based sessions only. All other types will utilize thedeleteaction.
Note
When sessions are stopped or paused, the CPU/RAM resources on the Agent become available for other requests to create new sessions.
This may lead to a user not being able to resume a paused/stopped session if the Agent’s resources become consumed by other running sessions.
When using Cloud Autoscaling, the system will not destroy Agents that have stopped/paused sessions and will similarly allow other sessions to be provisioned on the Agent.
If this is undesirable, the admin can ensure users are not given the allow_kasm_pause and allow_kasm_stop permissions.
keepalive_interval
The keepalive_interval is how often the client will send a keepalive request to Kasm when the user is actively using a session. This setting is 300 seconds by default for the “All Users Group”.
idle_disconnect
This setting is the number of minutes Kasm will wait when the user is idle before taking an action. This action will depend on the user context. If the user is in a Kasm session when the idle timeout expires the user is disconnected from the Kasm session and sent back to the dashboard. Any Kasm sessions that the user was connected to will be disconnected and those sessions will be subject to the keepalive_expiration. If the user is at the dashboard when the idle timeout expires the user is logged out of Kasm. This setting is set to 20 minutes by default in the “All Users Group”. This setting must be higher than the keepalive_interval setting to function properly.
usage_limit
The usage_limit setting is a highly flexible option allowing the administrator to configure a maximum usage number of hours either for each user in the group or for the entire group collectively to use over a set time period. This setting is a decimal value. When using the usage_limit setting all time that a Kasm session is running is counted against the total, this includes when the user is not actively connected to the session but the session is still running. This setting is for use cases where user workspace access should be metered. This setting is not enabled by default.
Note
Accounting for paused/stopped sessions are left as is. Users are “charged” for the full duration of the session, even if the session is paused or stopped.
The user can see how much time they have used/have remaining on the user dashboard:

Session Time Usage
Clicking on this icon will bring up a more detailed display.
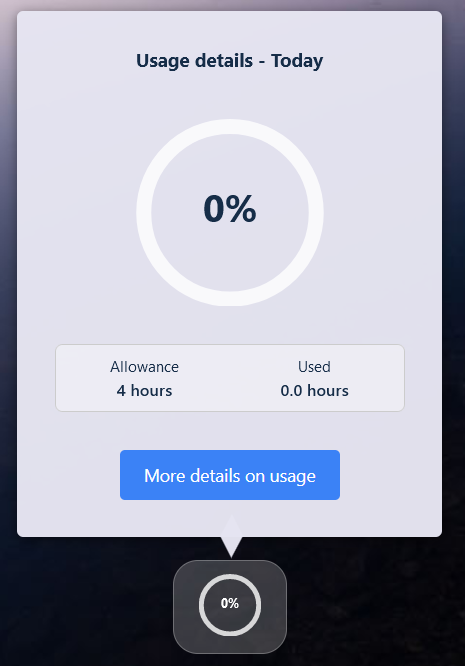
Detailed Session Time Usage
session_time_limit
The session_time_limit is a set amount of time that a workspace will be allowed to run once that workspace is created. This time limit is irrespective of whether the user is actively using the session or if the session is disconnected and running in the background. When session_time_limit is configured, the keepalive_expiration setting is not used. This setting is not enabled by default
Session Time Limit Countdown
Group Permissions
Groups have an optional list of permissions attached to them. When a user logs in, all permissions across all groups the user is a member of are aggregated
and determine what actions a user is authorized for. There are two built in groups, Administrators and All Users. The Administrators group has the Global
Admin permission while the built-in All Users group has the User permission. All users are automatically a member of the All Users group.
To configure group settings:
Log into the UI as an administrator.
Select Groups
Next to the desired group select Edit from the actions menu.

Edit Group
Select the Permissions tab to view and edit the permissions applied to the group.
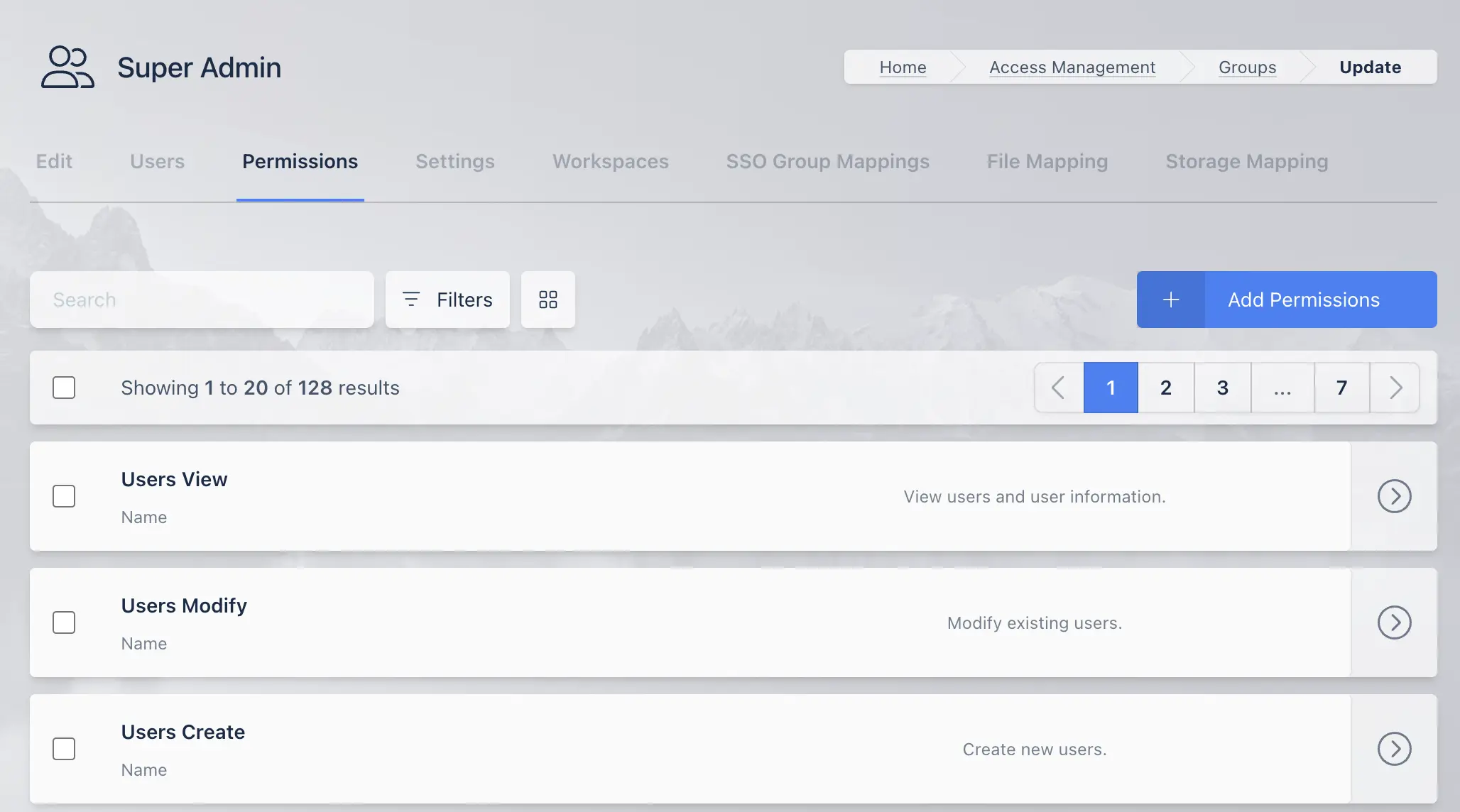
Group Settings
The following table lists the permissions and descriptions of each permission.
Name |
Description |
|---|---|
User |
Default level of permissions for normal users. |
Global Admin |
Global Administrator with all permissions. |
Users View |
View users and user information. |
Users Modify |
Modify existing users. |
Users Create |
Create new users. |
Users Delete |
Delete exiting users. |
Users Modify Admin |
Modify users with Global Admin permissions. |
Users Auth Session |
Login and logout on behalf of another user. |
Groups View |
View groups, group members, and group settings. |
Groups Modify |
Modify group members and settings. |
Groups Create |
Create new groups. |
Groups Delete |
Delete existing groups. |
Groups View IfMember |
View groups you are a member of, excluding system groups. |
Groups Modify IfMember |
Modify groups you are a member of, excluding system groups. |
Groups View System |
View groups, group members and group settings of system defined groups. |
Groups Modify System |
Modify group members and settings of system groups. |
Groups Delete System |
Delete a system group. |
Agents View |
View agents and agent settings. |
Agents Modify |
Modify agent settings. |
Agents Create |
Create agents. |
Agents Delete |
Delete existing agents. |
Staging View |
View staging list and stage configuration settings. |
Staging Modify |
Modify existing staging settings. |
Staging Create |
Create new staging configurations. |
Staging Delete |
Delete existing staging configurations. |
Casting View |
View casting list and casting configuration settings. |
Casting Modify |
Modify existing casting settings. |
Casting Create |
Create new casting configurations. |
Casting Delete |
Delete existing casting configurations. |
Sessions View |
View all user sessions. |
Sessions Modify |
Perform modifications to a session of another user. |
Sessions Delete |
Delete the session of another user. |
Session Recordings View |
View user session recordings. |
Images View |
View images |
Images Modify |
Modify image configurations. |
Images Create |
Create new images. |
Images Delete |
Delete existing images. |
Images Modify Resources |
Modify image resource settings, such as CPU and Memory settings. |
DevAPI View |
View developer API list. |
DevAPI Modify |
Modify developer API configurations. |
DevAPI Create |
Create a new developer API key. |
DevAPI Delete |
Delete an existing developer API key. |
Webfilters View |
View webfilters |
Webfilters Modify |
Modify existing webfilters |
Webfilters Create |
Create a new webfilter. |
Webfilters Delete |
Delete an existing webfilter |
Brandings View |
View branding configurations. |
Brandings Modify |
Modify existing branding configurations. |
Brandings Create |
Create new branding configurations. |
Brandings Delete |
Delete existing branding configurations. |
Settings View |
View global settings. |
Settings Modify |
Modify global settings in all categories. |
Settings Modify Auth |
Modify global settings in the authentication category. |
Settings Modify Auth Captcha |
Modify global settings in the authentication captcha category. |
Settings Modify Cast |
Modify global settings in the casting category. |
Settings Modify Images |
Modify global settings in the images category. |
Settings Modify License |
Modify global settings in the license category. |
Settings Modify Logging |
Modify global settings in the logging category. |
Settings Modify Manager |
Modify global settings in the manager category. |
Settings Modify Scale |
Modify global settings in the scale category. |
Settings Modify Subscription |
Modify global settings in the subscription category. |
Settings Modify Filter |
Modify global settings in the filter category. |
Settings Modify Storage |
Modify global settings in the storage category. |
Settings Modify Connections |
Modify global settings in the connections category. |
Settings Modify Theme |
Modify global settings in the theme category. |
Auth View |
View LDAP/OIDC/SAML configurations. |
Auth Modify |
Modify LDAP/OIDC/SAML configurations. |
Auth Create |
Create LDAP/OIDC/SAML configurations. |
Auth Delete |
Delete LDAP/OIDC/SAML configurations. |
Licenses View |
View licenses. |
Licenses Create |
Add new licenses. |
Licenses Delete |
Delete licenses. |
System View |
View system information. |
System Export Schema |
Export system schema. |
System Import Data |
Import system data. |
System Export Data |
Export system data. |
Reports View |
View system reports and logging. Warning: Providing access to logs can provide a lot of potentially sensitive information. |
Managers View |
View the managers. |
Managers Modify |
Modify existing managers. |
Managers Create |
Create a new manager. |
Managers Delete |
Delete existing managers. |
Zones View |
View Zones and Zone settings. |
Zones Modify |
Modify Zone settings. |
Zones Create |
Create new Zones. |
Zones Delete |
Delete existing Zones. |
Companies View |
View companies. |
Companies Modify |
Modify existing company. |
Companies Create |
Create a new company. |
Companies Delete |
Delete an existing company. |
Connection Proxy View |
View connection proxies. |
Connection Proxy Modify |
Modify connection proxies. |
Connection Proxy Create |
Create a connection proxy. |
Connection Proxy Delete |
Delete an existing connection proxy. |
Physical Tokens View |
View physical 2FA tokens. |
Physical Tokens Modify |
Assign/Unassign physical 2FA tokens. |
Physical Tokens Create |
Import or create physical 2FA tokens. |
Physical Tokens Delete |
Delete a physical 2FA token. |
Servers View |
View servers. |
Servers Modify |
Modify existing servers. |
Servers Create |
Create new servers. |
Servers Delete |
Delete servers. |
Server Pools View |
View server pools. |
Server Pools Modify |
Modify server pools. |
Server Pools Create |
Create a new server pool. |
Server Pools Delete |
Delete a server pool. |
Autoscale View |
View auto scale configurations. |
Autoscale Modify |
Modify an existing auto scale configuration. |
Autoscale Create |
Create a new auto scale configuration. |
Autoscale Delete |
Delete auto scale configurations. |
VM Provider View |
View VM Provider configurations. |
VM Provider Modify |
Modify VM Provider configurations. |
VM Provider Create |
Create new VM Provider configurations. |
VM Provider Delete |
Delete VM Provider configurations. |
Autoscale Schedule View |
View an auto scale schedule. |
Autoscale Schedule Modify |
Modify an auto scale schedule. |
Autoscale Schedule Create |
Create an auto scale schedule. |
Autoscale Schedule Delete |
Delete an auto scale schedule. |
DNS Providers View |
View DNS provider configurations. |
DNS Providers Modify |
Modify DNS provider configurations. |
DNS Providers Create |
Create new DNS Provider configurations. |
DNS Providers Delete |
Delete DNS Provider configurations. |
Registries View |
View Workspace Registries. |
Registries Modify |
Modify existing Workspace Registries. |
Registries Create |
Add new Workspace Registries |
Registries Delete |
Delete a Workspace Registry |
Storage Providers View |
View Storage Providers. |
Storage Providers Modify |
Modify existing Storage Providers. |
Storage Providers Create |
Create new Storage Providers. |
Storage Providers Delete |
Delete an existing Storage Provider. |
Egress Providers View |
View Egress Providers. |
Egress Providers Modify |
Modify existing Egress Providers. |
Egress Providers Create |
Create new Egress Providers. |
Egress Providers Delete |
Delete an existing Egress Provider. |
Egress Gateways View |
View Egress Gateways. |
Egress Gateways Modify |
Modify existing Egress Gateways. |
Egress Gateways Create |
Create new Egress Gateways. |
Egress Gateways Delete |
Delete an existing Egress Gateway. |
Egress Credentials View |
View Egress Credentials. |
Egress Credentials Modify |
Modify existing Egress Credentials. |
Egress Credentials Create |
Create new Egress Credentials. |
Egress Credentials Delete |
Delete an existing Egress Credential. |
Banners View |
View banners. |
Banners Modify |
Modify existing banners. |
Banners Create |
Create new banners. |
Banners Delete |
Delete an existing banner. |
AD User Management View |
View AD User Management Configurations. |
AD User Management Modify |
Modify existing AD User Management Configurations. |
AD User Management Create |
Create new AD User Management Configurations. |
AD User Management Delete |
Delete an existing AD User Management Configuration. |
Permission Changes
A user’s permissions are embedded in their session token, which is generated on login. A user’s token lifetime is controlled by the Session Lifetime global setting. The UI will get a new session token every 5 minutes. The fastest way to get new permissions to apply, is to have the user log out and log back in, otherwise, the change will apply generally within 5 minutes.
Permission Dependencies
While most permissions can stand alone, there are dependencies between some permissions. Generally,
a Modify, Create, and/or Delete permission will need the corresponding View permission. The
following are additional permission dependencies, which means you will need to grant multiple
permissions to have the desired effect.
Licenses ViewrequiresSystem ViewPermissions ViewrequiresGroups ViewRegistries ViewrequiresImages View,System View, andAgents ViewAutoscale ViewrequiresServer Pools ViewAutoscale Schedule ViewrequiresServer Pools ViewDNS Providers ViewrequiresServer Pools ViewVM Providers ViewrequiresServer Pools ViewandAutoscale ViewUsers DeleterequiresSessions Deleteif the target user has running sessions andUsers ModifyUsers DeleterequiresUsers Modify Adminto delete a user that has theGlobal AdminpermissionEgress Gateways Create,Egress Gateways Modify,Egress Gateways Delete,Egress Credentials Create,Egress Credentials ModifyandEgress Credentials DeleterequireEgress Providers Modify.
There are many cases where multiple permissions are not required, however, certain UI elements will
be hidden if the user does not have the permissions to view them. For example, a user may have
permissions to View Images, however, they may not have permissions to View Servers. If the user
goes to view an individual Workspace Image that targets a Server, they will not see the drop
down to view or edit the server the image is targeting.
Special Permissions
There are more available permissions around groups, beyond the basic View, Create, Modify, and Delete.
The Groups View IfMember and Groups Modify IfMember allow a user to view or modify a group if they
are a member of that group. This does not extend to built-in system groups (All Users and Administrator).
To edit or view System groups, they will also need the Groups View/Modify System permission.
There is an additional permission that protects modification of users with the Global Admin permission.
In order to modify a Global Admin, the user requesting the modification must themselves be a
Global Admin or have the User Modify Admin permission.
There are two permissions that allow modifications to Workspace Images, Images Modify and Images Modify Resources.
The Images Modify allows modification of all Image settings except those that would modify the
physical/virtual compute resources. The following settings require the Images Modify Resources permission
to edit:
GPU Count
Cores
Memory
CPU Allocation Method
Uncompressed Image Size
Docker Registry
Docker Registry Username
Docker Registry Password
Hash
Volume Mappings
Docker Run Config Override
Docker Exec Config
Group Workspaces
Administrators can define which Workspaces are available to each group. By default newly created workspaces are automatically assigned to the All Users group. This behavior can be changed by modifying the Add Images To Default Group global Settings.
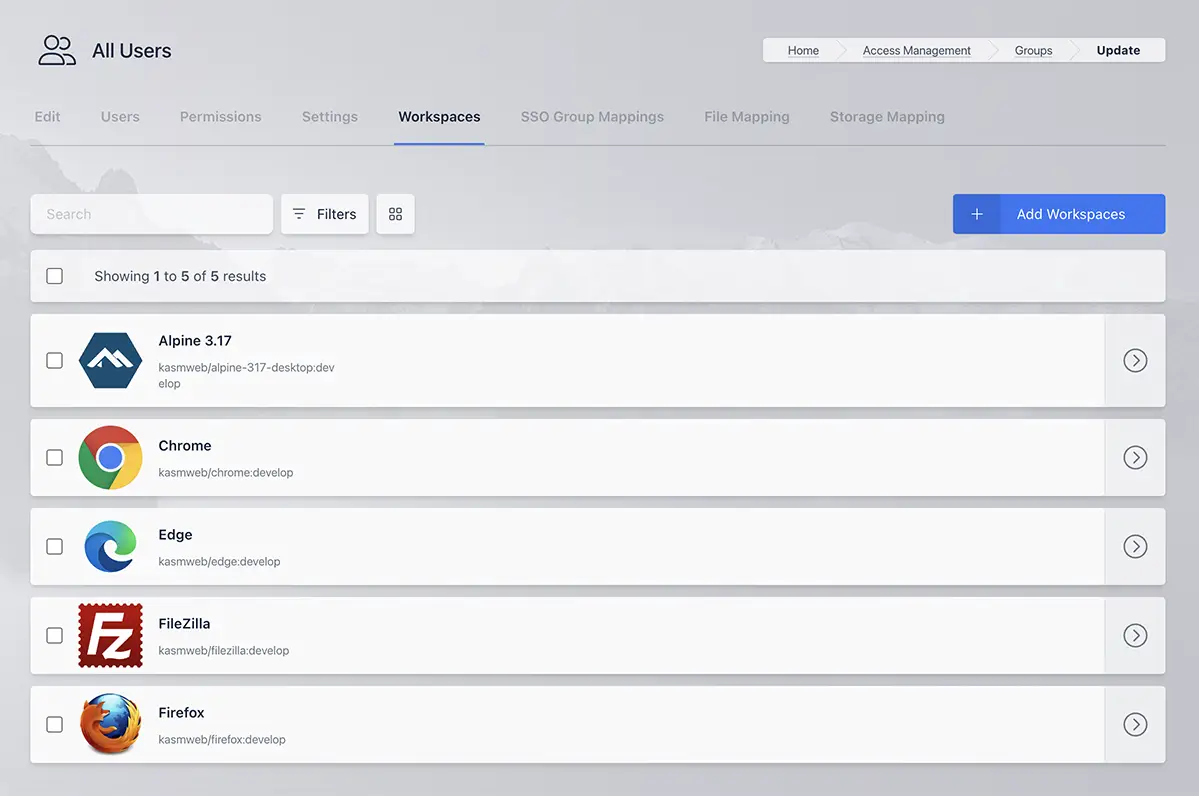
Group Workspaces
SSO Group Mappings
Administrators can configure the system to automatically map users that authenticate with an SSO provider (e.g SAML, OpenID, LDAP) into Kasm Groups.
If Assign All Users is selected, any user that authenticates with the defined SSO provider will be added to the Kasm group. Otherwise, only users that have the defined Group Attributes passed in by the SSO provider will be added to the group.
These group mappings are evaluated and updated at each user login. If a mapping is defined and a user does not have the group attributes listed, the user will be removed from the group.
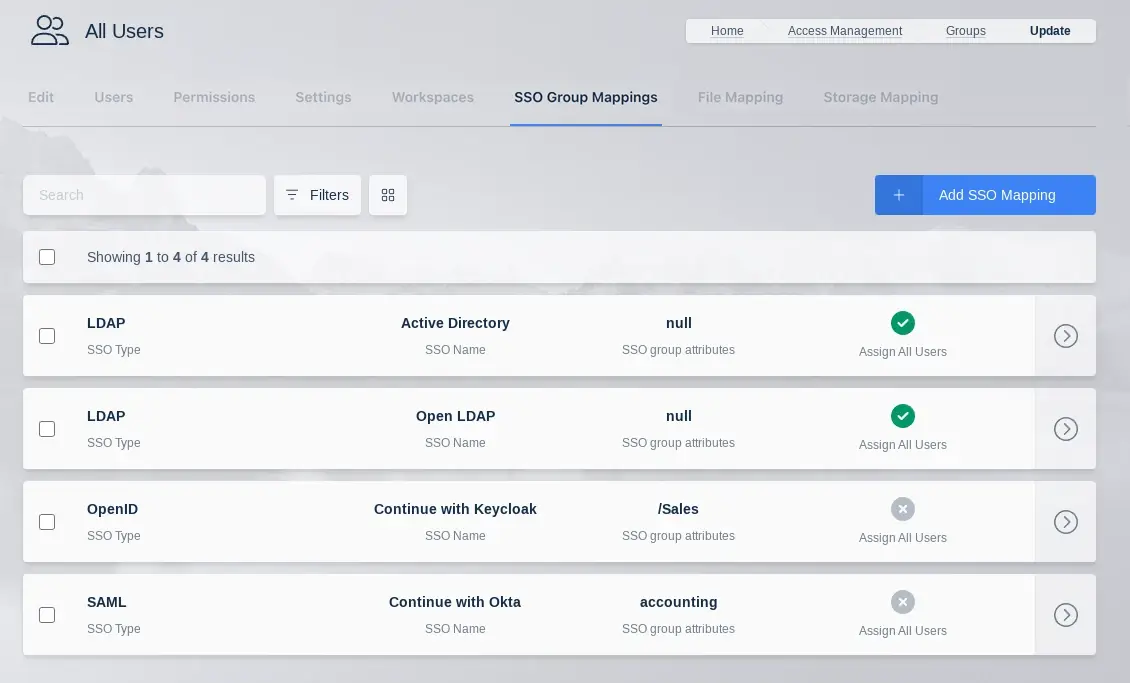
SSO Group Mappings
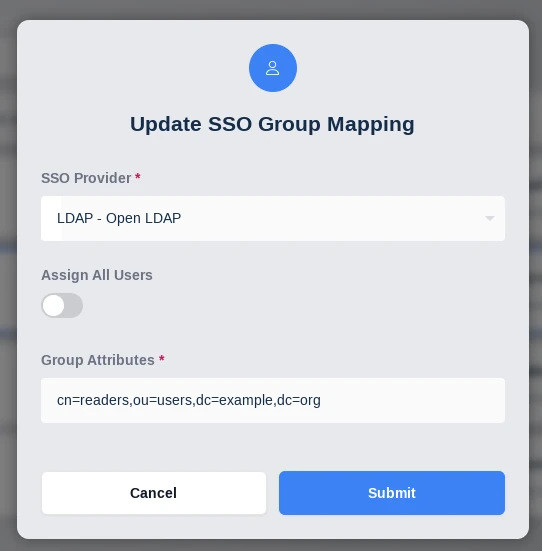
SSO Group Mappings Config
Group File Mappings
File Mappings allow the administrator to manage files to be mapped to the inside of a user’s container based Workspace session. File Mappings can be defined on a User, Group, and/or Workspace. See the primary documentation on File mappings for more details.
Note
When a user belongs to multiple Groups that define a File Mapping with the same destination, the group with the lowest priority value gets mapped into the user’s container.
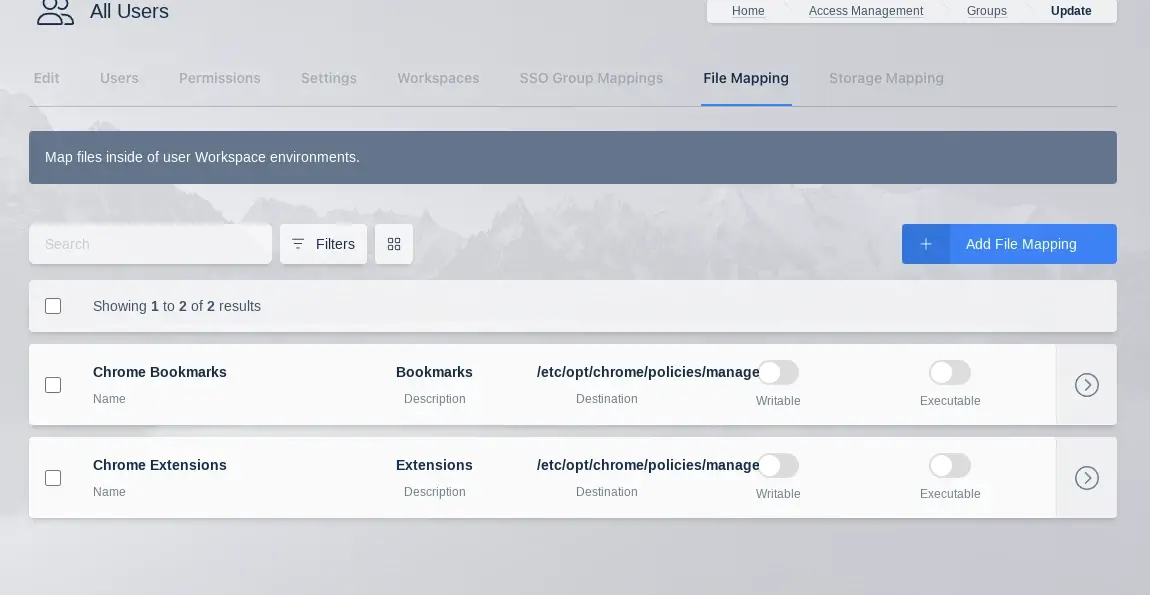
File Mappings Table
The following is an example File Mapping of a Chrome Managed Policy to define bookmarks in Chrome.
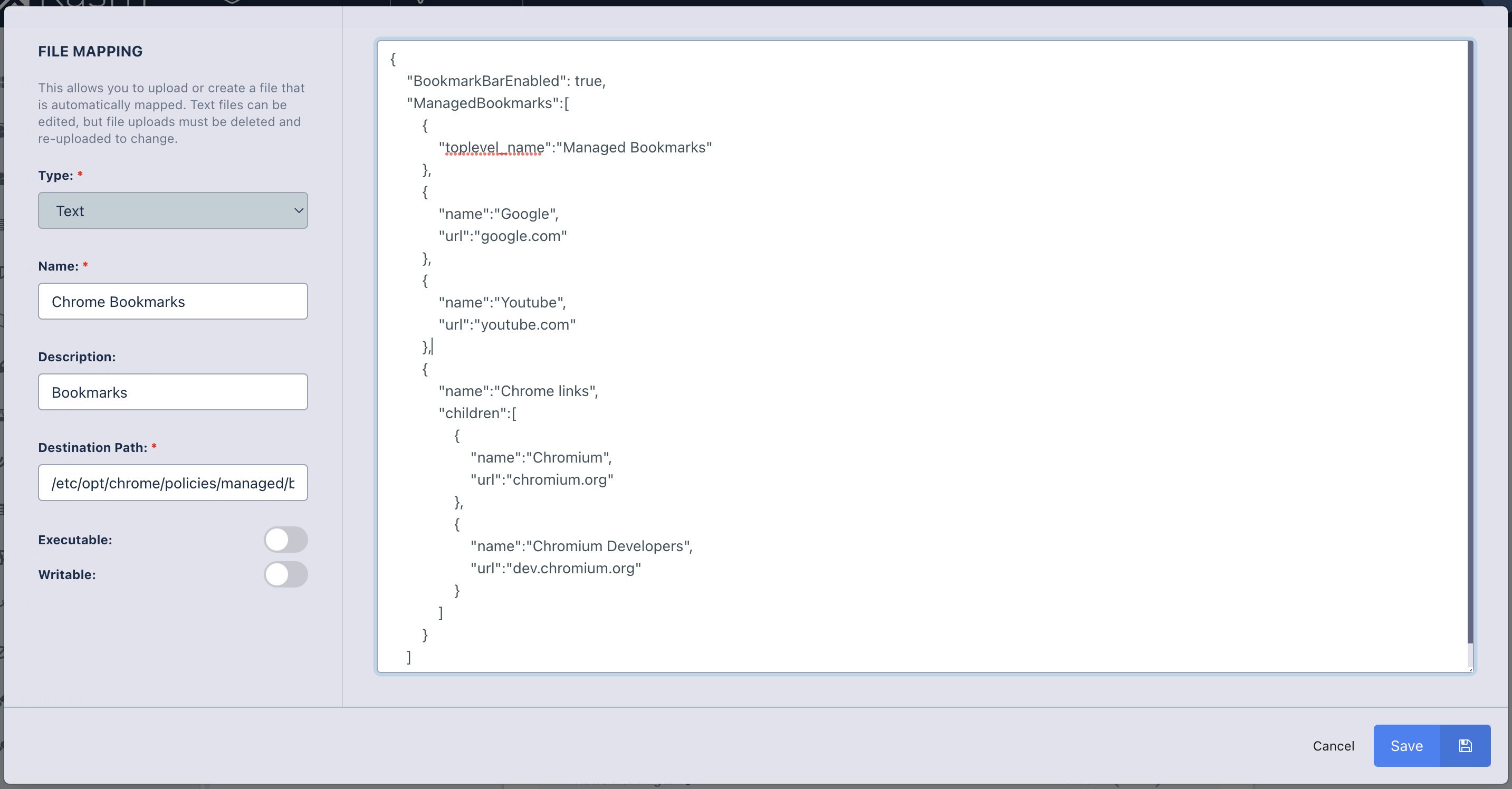
File Mapping Definition