Connection Proxy
The connection proxy is a new role in the Kasm Workspaces architecture as of version 1.12.0. The connection proxy role server is responsible for translating connection types that are not web native, into an HTML5 accessible connection. Support connection types include RDP (to include RDS), SSH, and VNC protocols. The underlying technology powering this role is a custom build of Apache guacd and a Kasm connection management service that is responsible for Kasm customized integration with guacd.
Notably, the Connection Proxy can achieve local load balancing by spawning multiple instances of the connection management service, each running on a separate core, all within the same container. The number of instances to spawn can be controlled by using the installation parameter “–guac-cluster-size N”, where N signifies the number of instances you wish to create. In the absence of this parameter, the system defaults to creating as many instances as there are cores on the system.
RDP Gateway
The RDP gateway is a set of additional functionality that was added to the Connection Proxy role in Kasm Workspaces 1.16.0. It provides a proxy capability allowing users to connect to Kasm Windows workspaces utilizing their client’s RDP thick client. This allows several features that are not possible with Kasm’s web native RDP access method. Namely smart card, usb, and webcam passthrough from the user’s client machine into the Kasm session while maintaining Kasm’s DLP protections.
This is suppoerted with Windows, Linux, ChromeOS and macOS clients though the instructions to get a seamless experience differ for each OS see Auto-Opening RDP Files for more details.
Users/Administrators can utilize whichever RDP connection software that is required by company policy or personal preference. Kasm Technologies has tested the Microsoft client on Windows and macOS and the XtraLogic client on ChromeOS. The client chosen must support the desired features for instance not all clients support smart card passthrough.
Architecture
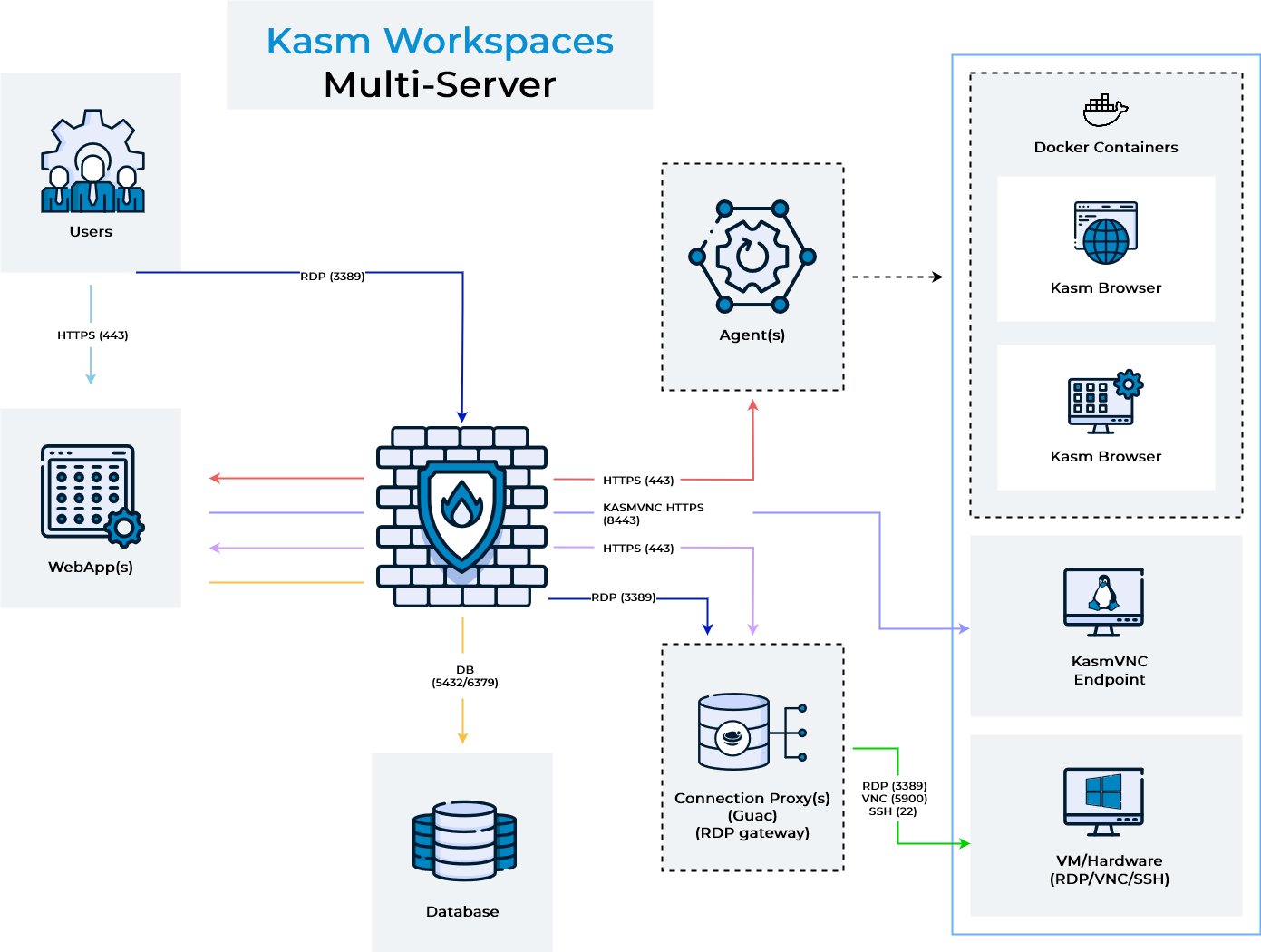
Architecture
The above diagram shows the architecture and user flow of traffic. For Kasm guac sessions, when a user connects to a remote session comes in, shown in light blue, the request can optionally be load balanced between multiple web app servers. The Web App server queries the database for a list of potential connection proxy servers that are responsible for the Kasm Deployment Zone that the requested server is in. The Web App service goes down the list of connection proxies in random order and performs a health check. The user’s HTTPS connection is then proxied to the first connection proxy server (light purple line), in the request zone, that responds to the health check. This sequence of events ensures resiliency in the event of networking or server issues with a single connection proxy. For Kasm RDP gateway sessions, when a user connects to a remote session comes in, shown in light blue, the request can optionally be load balanced between multiple web app servers. The Web App server queries the database for a list of potential RDP gateway connection proxy servers that are responsible for the Kasm Deployment Zone that the requested server is in. The Web App service goes down the list of RDP gateway connection proxies in random order and performs a health check. When a healthy server is found the Web App server builds an RDP file targeting the selected RDP gateway server and presents it to the user’s browser for download. The user’s RDP client then makes a connection over 3389 to the Kasm RDP gateway service (dark blue line), which is then proxied to the RDP target. This sequence of events ensures resiliency in the event of networking or server issues with a single RDP gateway connection proxy.
When the connection from the user enters either the RDP gateway or guac connection proxy, it performs an authentication request up to the Web App Role server (light purple line) to authenticate the user, authorize that the user has access to the requested server, and to download connection details for the server. The connection proxy then performs an RDP connection to the remove server (green line).
Single server deployments have all roles installed on a single server. For multi-server deployments, you should consider deploying at least 2 connection proxy servers per Kasm deployment zone. Kasm will automatically load balance users and provide automatic fail-over should one stop responding.