Microsoft (Public) OpenID Setup
Warning
Be mindful when configuring OpenID providers that are public. Any user that can successfully authenticate with the provider will have access to your deployment of Kasm Workspaces. While access to Kasm Workspace apps and desktops can be resitricted with Kasm group permissions, any user of the public authentication provider would still be able to login to your deployment of Kasm. It is recommended to use a private OpenID provider unless your intention is to allow authentictioned access to all users of the OpenID platform provider.
This guide walks through a basic setup allowing Microsoft users to authenticate with your Kasm deployment.
Reference Docs:
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-v2-protocols
Creating a Microsoft OAuth App
Login to the Microsoft Azure Portal: https://portal.azure.com/
Select Azure Active Directory.
Azure Active Directory
Select App Registrations.
App Registration
Select New Registration.
Give the app a Name (e.g
Kasm).In the Supported account types select Accounts in any organizational directory (Any Azure AD directory - Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox).
Warning
In this example, we walk through creating an integration where any Microsoft user can auth with the Kasm app. This is ideal for a public facing deployment. Other options are available for single-tenant and multi-tenant configurations.
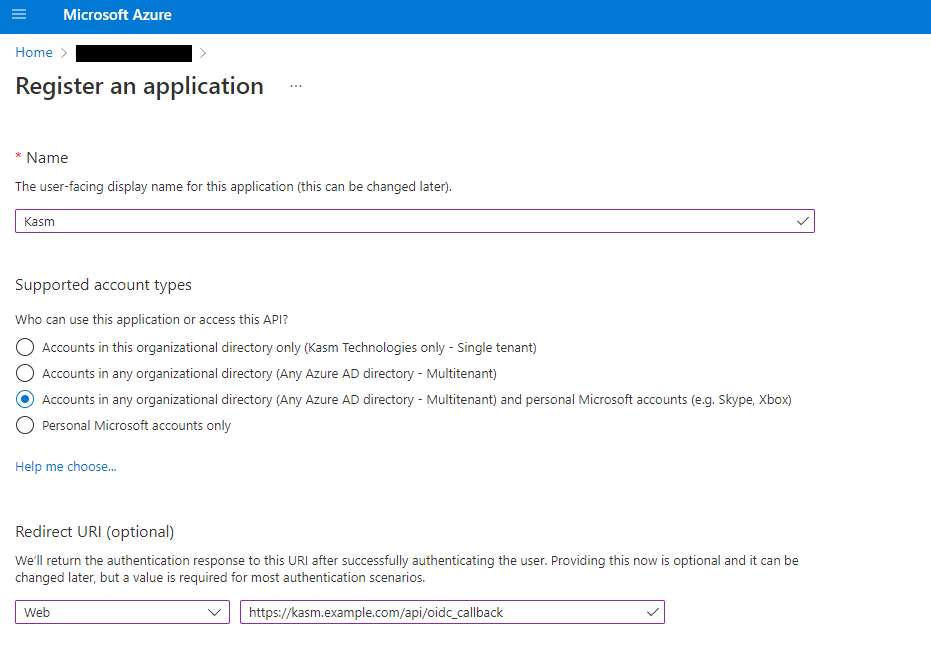
Register App
On the next page, the Application (client) ID is shown, save this value as the Client ID to be used in the next section.
Select Add a certificate or secret next to Client credentials.
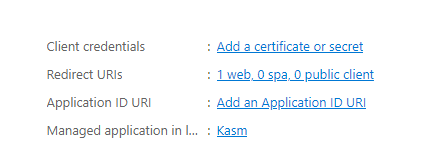
Client Credentials
Select the Client secrets tab, then slick New client secret.
Enter a description and expiration then click Add.
The credentials are shown, save the Value as the Client Secret to be used in the next section.
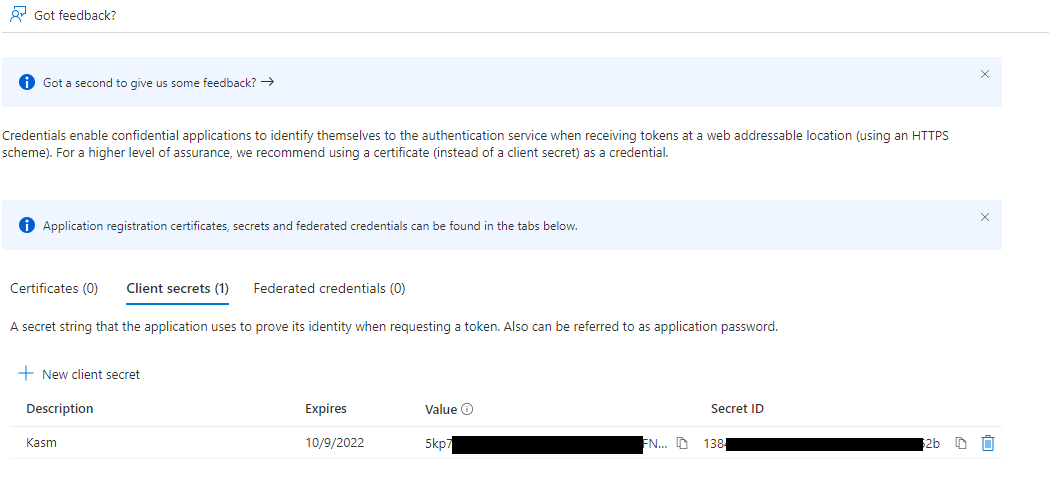
Client Secret
Select Token configuration.
Select Add Optional Claim
Under Token Type select ID, then check the box for sid. Click Add.
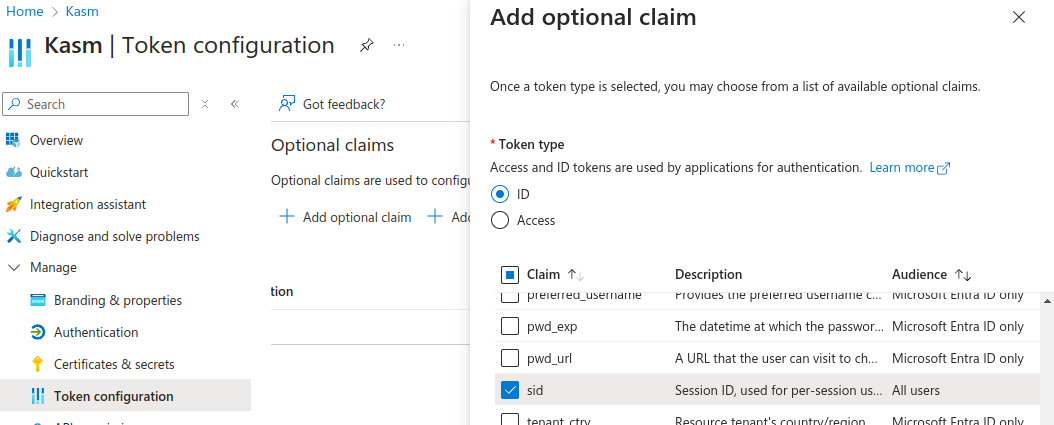
SID Claim
Select Authentication
In Front-channel Logout URL, provide the Kasm
/api/oidc_frontchannel_logoutendpoint as shown. Click Save.
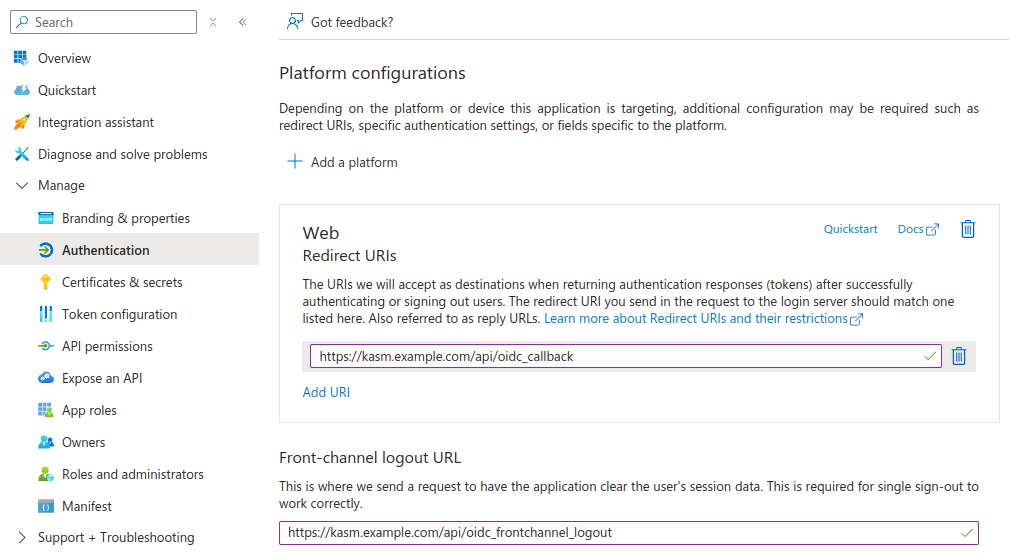
Front-channel Logout URL
Kasm OpenID Config
Log into the Kasm UI as an administrator.
Select Access Management -> Authentication -> OpenID -> Add Config.
Update the form with the following entries, using the Client ID and Client Secret gathered in the previous section.
Property |
Value |
Enabled |
Checked |
Display Name |
Continue with Microsoft |
Logo URL |
|
Auto Login |
Unchecked |
Hostname |
<Empty> |
Default |
Checked |
Client ID |
<Client ID From Microsoft OAuth App> |
Client Secret |
<Client Secret from Microsoft OAuth App> |
Authorization URL |
|
Token URL |
|
User Info URL |
|
Scope |
|
Username Attribute |
|
Groups Attribute |
Unchecked |
Debug |
Unchecked |
Redirect URL |
|
OpenID Connect Issuer |
|
Logout with OIDC Provider |
Checked |
Enable OIDC SLO Frontchannel Endpoint |
Checked |
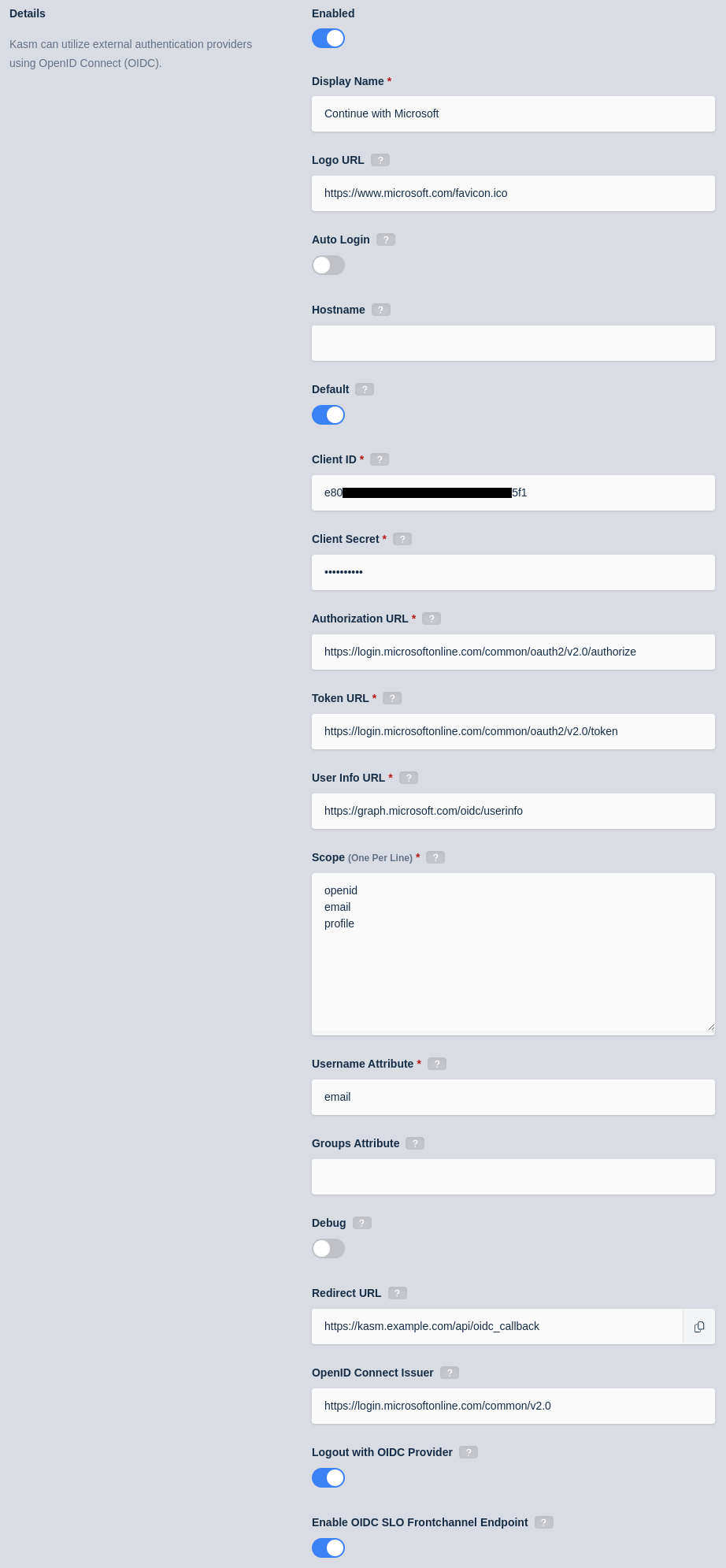
Kasm OIDC Configurations
Click Save to save the changes.
Microsoft Login Test
Logout of the Kasm to display the login screen. The OpenID configuration should be shown.
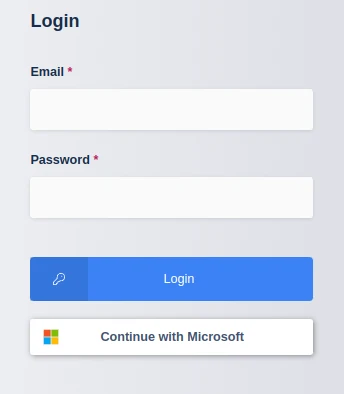
Login Screen
Click Continue with Microsoft
The user is redirected to Microsoft for auth.
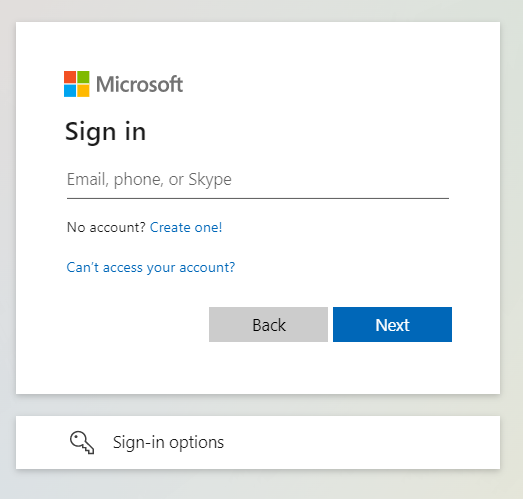
Microsoft Auth
Upon completion, the user is logged into the Kasm app.