Keycloak SAML Setup¶
Create a new SAML configuration in Kasm¶
Log into the Kasm UI as an administrator.
Select Authentication -> SAML -> Create New Configuration
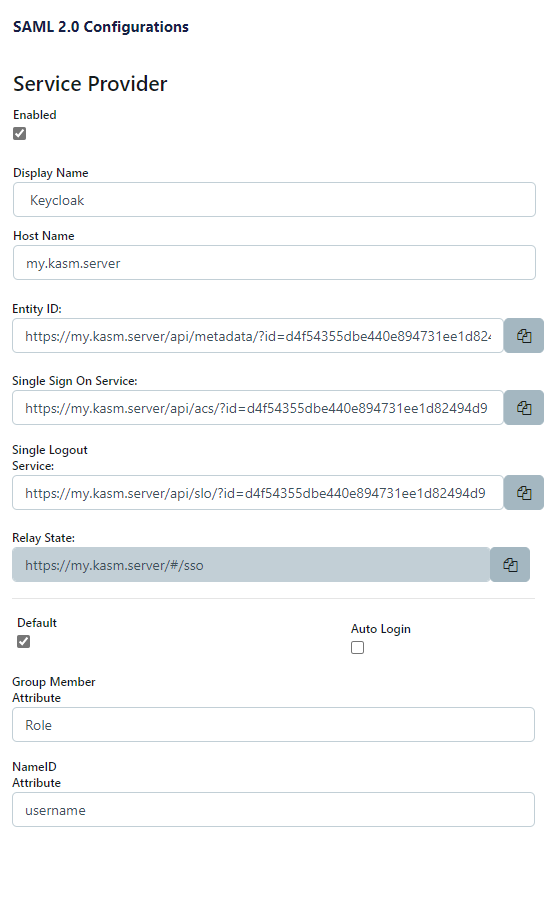
The SAML 2.0 Configuration page will auto-generate the Entity ID, Single Sign On Service, Single Logout Server, and Relay State values.
Check Enable and enter a Display Name. e.g (Keycloak)
Enter the Hostname for the workspaces deployment (e.g my.kasm.server).
Check Default.
Enter Role in Group Member Attribute.
Enter username in NameID Attribute.
Kasm SAML Configurations¶
Check Debug. Disable this setting after testing is complete.
Leave this page open and continue to the next steps.
Realm SAML Settings¶
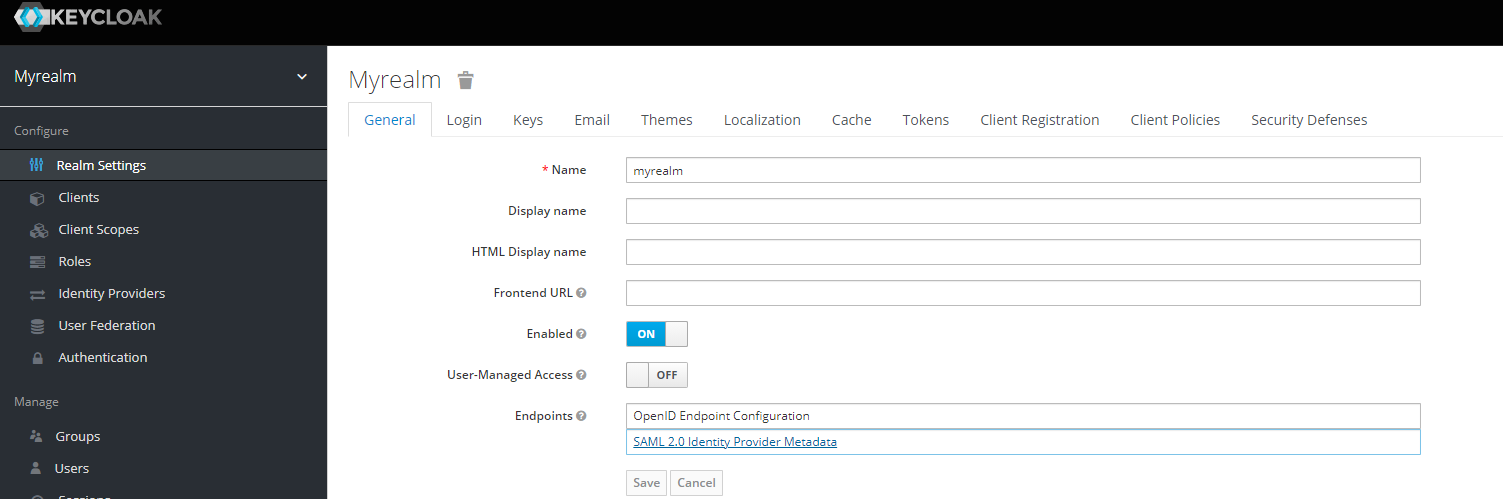
Navigate to the Keycloak Admin Portal. Select the desired Realm (e.g Myrealm) then select Realm Settings.
Click on SAML 2.0 Identity Provider Metadata.
Realm Settings¶
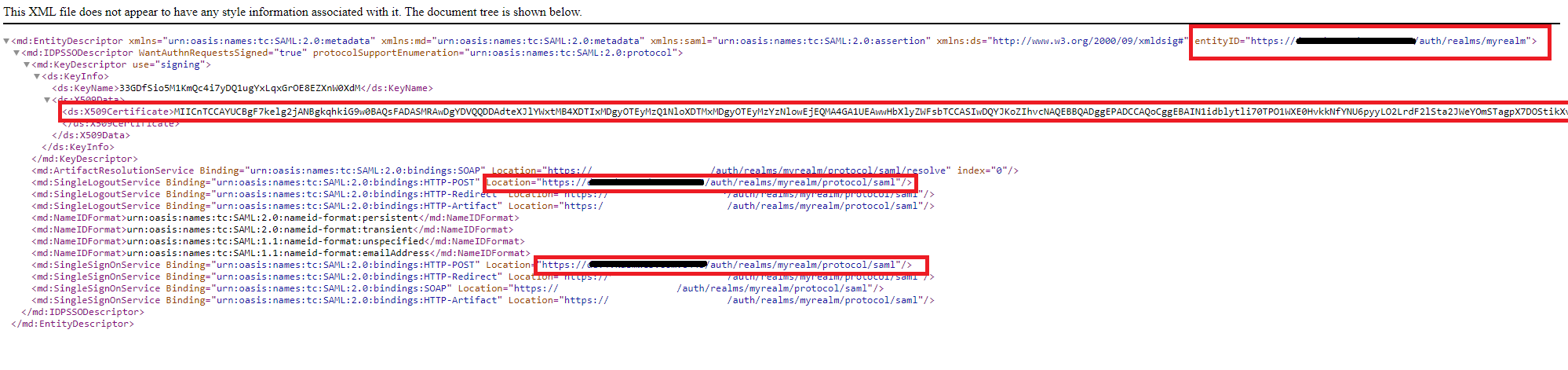
Copy the following items from the XML document to the Identity Provider section of the SAML configuration in Workspaces.
Keycloak Property |
Azure Property Name |
entityID |
Entity ID |
ds:X509Certificate |
X509 Certificate |
md:SingleLogoutService..HTTP-POST |
Single Logout Service/SLO Endpoint |
md:SingleSignOnService..HTTP-POST |
Single Sign On Service/SAML 2.0 Endpoint |
SAML XML¶
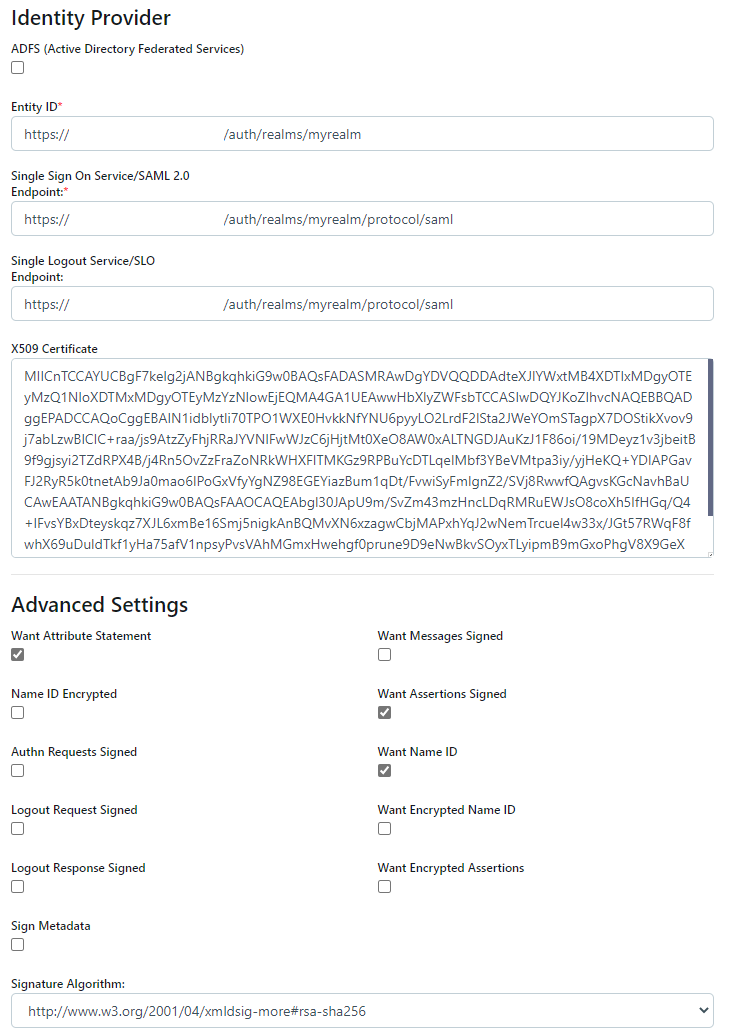
In the Advanced Settings of the Workspaces SAML configuration, check Want Assertions Signed.
In the Advanced Settings of the Workspaces SAML configuration, set Signature Algorithm to rsa-sha256.
Click Submit.
Identity Provider¶
Select Edit next to the new Saml config as these settings will need to be referenced in th following sections.
Add a new client in Keycloak¶
Navigate to the Keycloak Admin Portal. Select the desired Realm (e.g Myrealm) then select Clients.

Keycloak Portal¶
In the Clients window select Create.
In the Client ID field the value found in the Entity ID from the Service Provider sections in the Workspaces SAML configuration form.
Select saml as the Client Protocol and click Save.
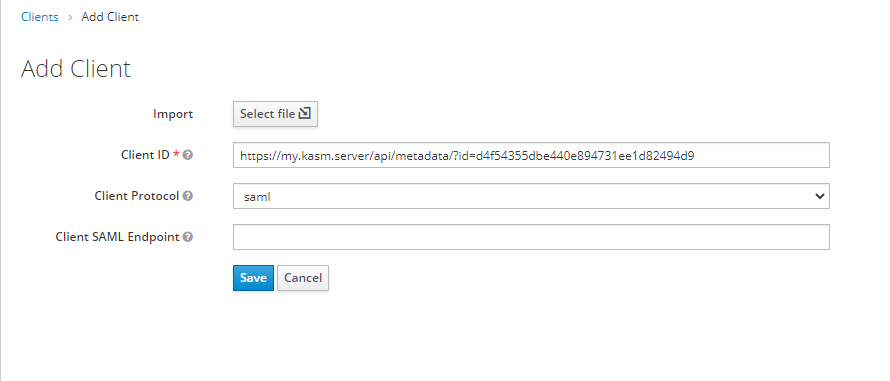
Add Client¶
Client Configurations¶
Enter a value for the Name field (e.g Kasm Workspaces).
Ensure Sign Assertions is set to On.
Ensure Client Signature Required is set to Off.
Ensure Force Name ID Format is set to On.
5. Update Valid Redirect URLs with a wildcard entry for the Workspaces deployment (e.g https://my.kasm.server/*
).
Update the Base URL with the URL of the Workspaces deployment (e.g
https://my.kasm.server).
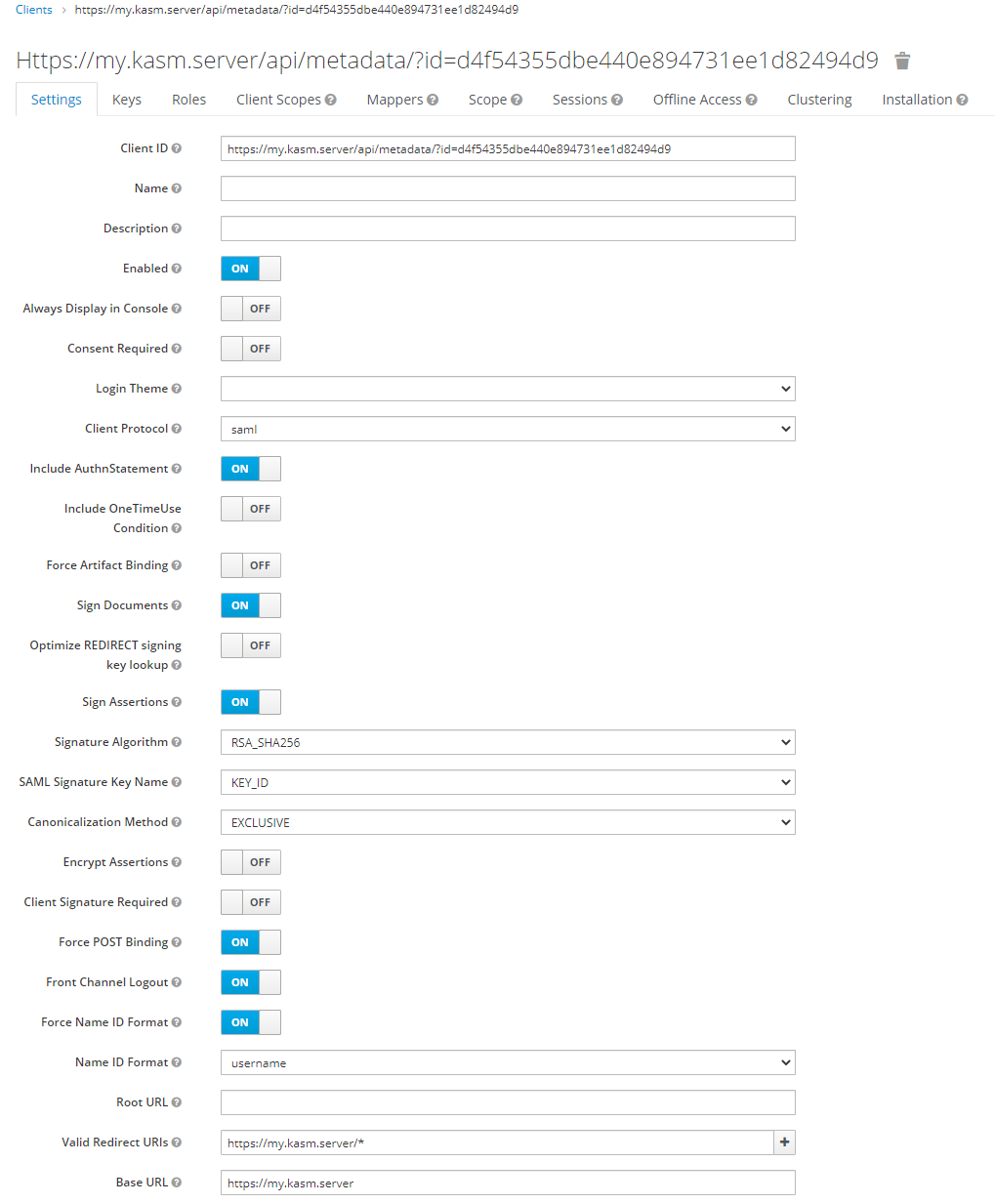
Client Configurations¶
Copy the Service Provider entries from the Kasm SAML Configurations started in the previous section into the Basic SAML configurations and click Save.
Keycloak Property |
Azure Property Name |
Master SAML Processing URL |
Single Sign On Service |
Logout Service POST Binding URL |
Single Logout Service |
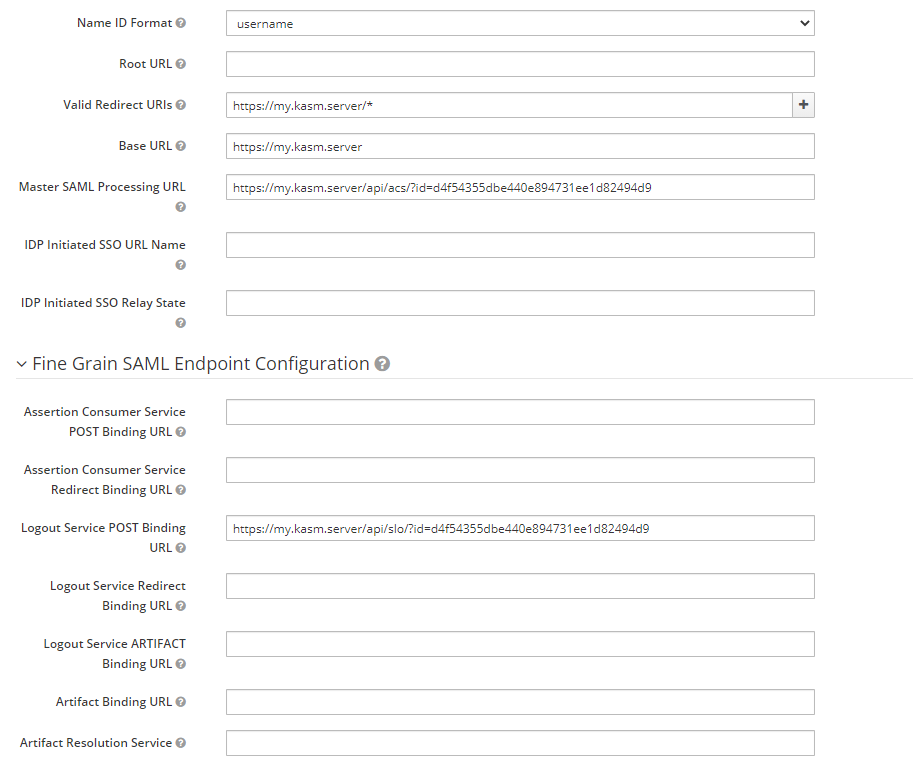
SAML URL Configurations¶
Adjust Single Role Attribute in Keycloak¶
Navigate to the Keycloak Admin Portal. Select the desired Realm (e.g Myrealm) then select Client Scopes.
Keycloak Portal¶
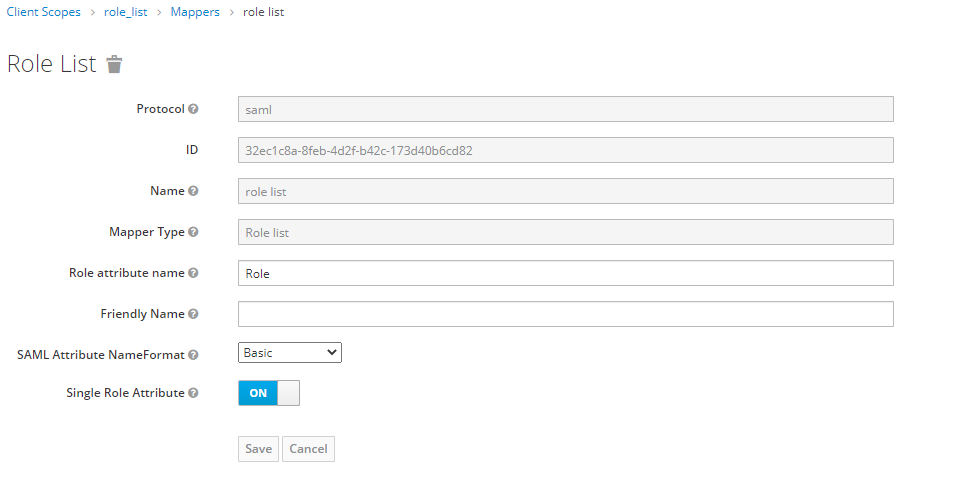
Select role_list (saml).
Select the Mappers tab.
Select role list.
Set Single Role Attribute to On, then click Save.
Role List¶
Testing Access¶
Log out of the Kasm UI if already logged in.
Navigate to the Kasm UI login page.

Kasm Login¶
Click Keycloak to initiate the SAML SSO process.
Keycloak Login¶
Mapping Roles¶
During the SAML authentication process , Keycloak will send a list of the user’s roles. These can be mapped to Kasm Groups.
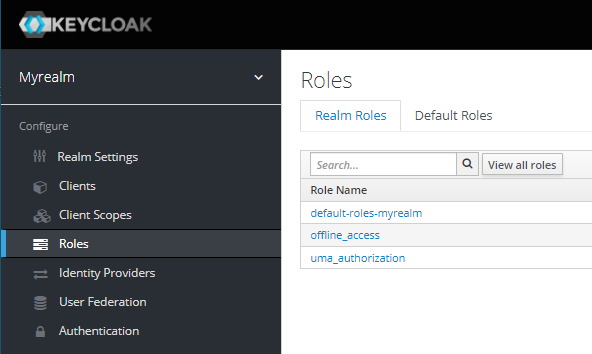
Navigate to the Keycloak Admin Portal. Select the desired Realm (e.g Myrealm) then select Roles.
Keycloak Portal¶
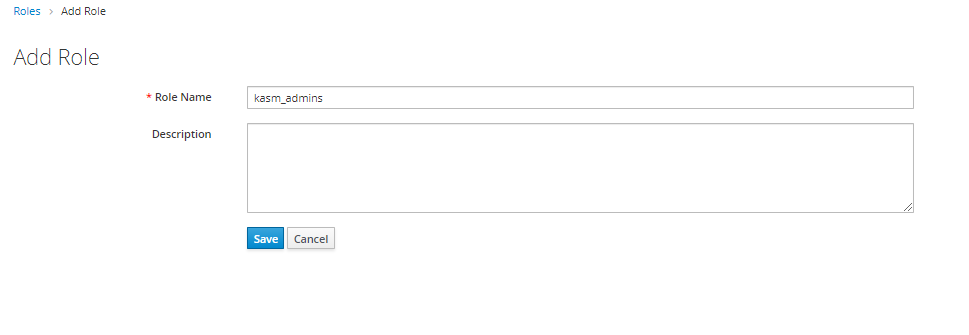
Select Add Role.
Name the role kasm_admins then click Save.
Create Role¶
Select Users from the Keycloak menu, then click the ID next to the desired user.
User Selection¶
Select the Role Mappings tab.
Select kasm_admins from the Available Roles then click Add selected.
Log into the Kasm UI as an administrator.
Select Groups, then click Add Group.
Name the Group Keycloak Kasm Admins and give it a priority (e.g 10).
Check SAML Group.
Enter kasm_admins as the SAML Group Name then click Submit.
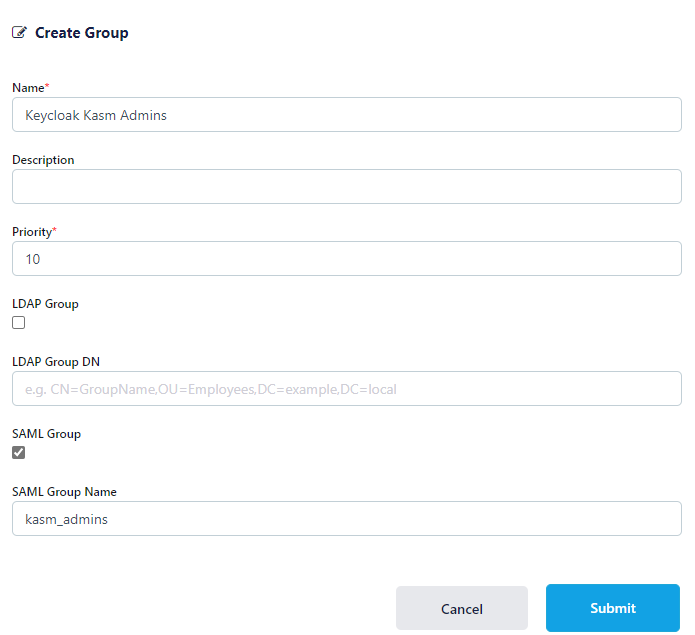
Create Group¶
Select View next to the Keycloak Kasm Admins Group.
Click Add Settings in the Group Settings section.
Select administrator from the dropdown , select True, then Add.
Log out of Kasm, and back in via SAML as the previously assigned user. The user should now be mapped to the Keycloak Kasm Admins a group.