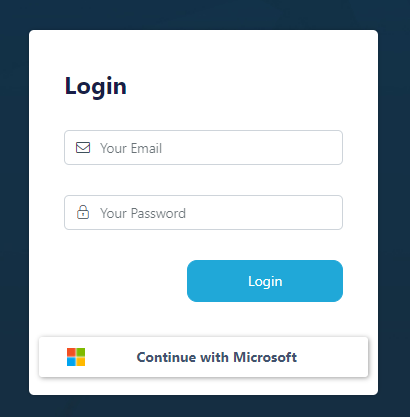
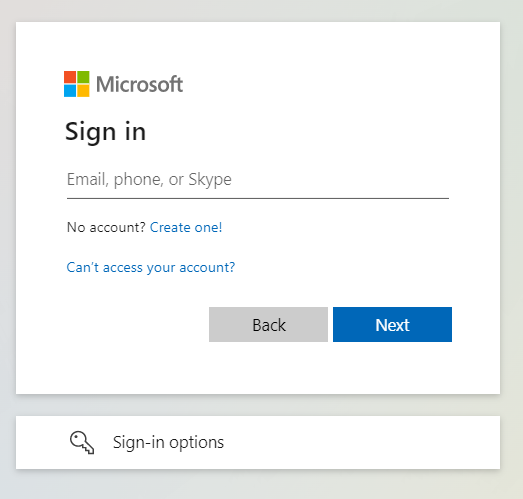
Microsoft (Internal) OpenID Setup
This guide walks through a basic setup allowing Microsoft users to authenticate with your Kasm deployment.
Reference Docs:
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-v2-protocols
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-fed-group-claims
Creating a Microsoft OAuth App
Login to the Microsoft Azure Portal: https://portal.azure.com/
Select Azure Active Directory.
Azure Active Directory
Select App Registrations.
App Registration
Select New Registration.
Give the app a Name (e.g
Kasm)In the Supported account types select Accounts in this organizational directory only….

Register App
On the next page, the Application (client) ID is shown, save this value as the Client ID to be used in the next section.
Select Endpoints. Note the OAuth 2.0 authorization endpoint (v2) and OAuth 2.0 token endpoint (v2) values to be used in the next section.
Select Add a certificate or secret next to Client credentials.
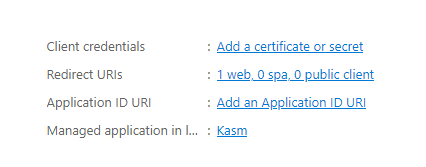
Client Credentials
Select the Client secrets tab, then slick New client secret.
Enter a description and expiration then click Add.
The credentials are shown, save the Value as the Client Secret to be used in the next section.
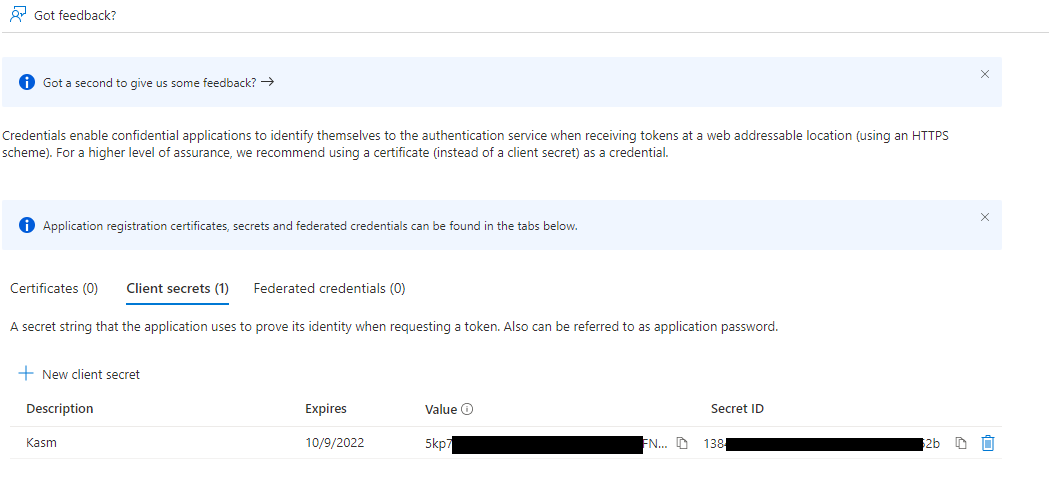
Client Secret
Select Token configuration.
Select Add group claims.
Check Security groups, then click Save.

Group Claims
Kasm OpenID Config
Log into the Kasm UI as an administrator.
Select Authentication -> OpenID -> Create New Configuration.
Update the form with the following entries, using the Client ID and Client Secret gathered in the previous section.
Property
Value
Display Name
Continue with Microsoft
Logo URL
https://www.microsoft.com/favicon.icoEnabled
Checked
Auto Login
Unchecked
Hostname
<Empty>
Default
Checked
Client ID
<Client ID From Microsoft OAuth App>
Client Secret
<Client Secret from Microsoft OAuth App>
Authorization URL
<OAuth 2.0 authorization endpoint (v2) value from Microsoft OAuth App>
Token URL
<OAuth 2.0 token endpoint (v2) value fom Microsoft OAuth App>
User Info URL
https://graph.microsoft.com/oidc/userinfoScope
openidemailprofileUsername Attribute
emailGroups Attribute
groupsDebug
Unchecked

Kasm OIDC Configurations
Click Submit to save the changes.
Microsoft Login Test
Group Mapping
The previous configurations will instruct the identity provider to send a list of Security Group ID the user belongs to during the OpenID auth workflow. We can configure Kasm Groups with the Security Group IDs from Azure AD so that users are automatically added/removed based on their Azure AD group Membership.
Log into the Kasm UI as an administrator.
Select Groups -> Add Group.
Name the Group Group Test, and define a priority.
Click Submit to create the group.

Add Group
On the groups screen, using the three dot menu select View on the group that was just created.
Scroll to the bottom of the screen and select Add SSO Mapping.
Select the OpenID IDP that was created above “OpenID - Continue with Microsoft” for the SSO Provider.
Then enter the Azure AD security group ID desired in the Group Attributes field.

Add SSO Group Mapping
Click Add
Logout, then login via the Microsoft Open ID login with a user that is a member of the specified group.
View the users group membership to ensure they are added to the newly created group.