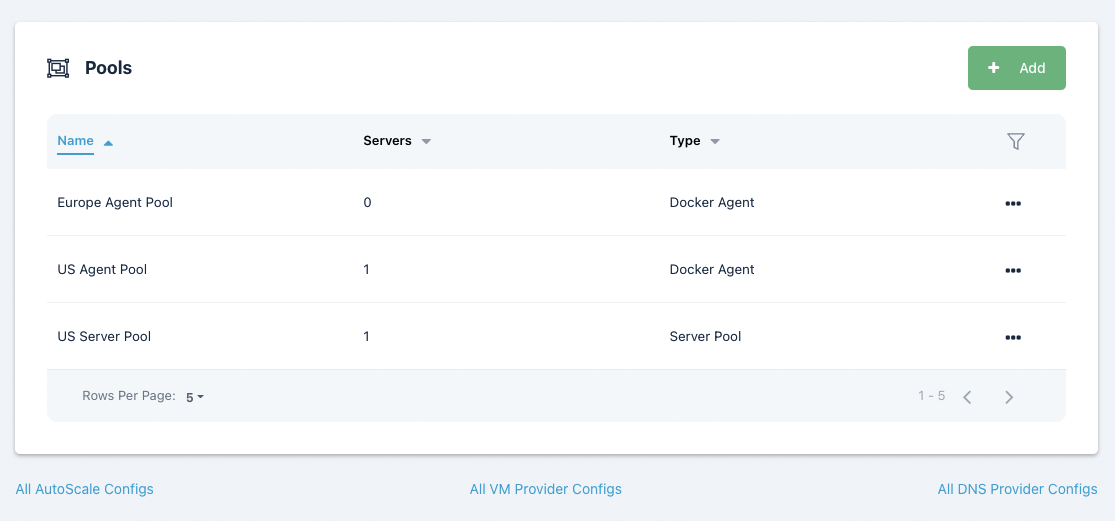
Pools
Pools can be used to group a set of similar fixed systems together, so they can be treated as a single Workspace for user access. Users will see a single Workspace icon on their dashboard, but their session will get distributed to an available server in the pool. Each server in the pool can be set to support 1 or more concurrent sessions. Kasm automatically distributes the sessions evenly over the servers.
Pools can also be used to auto scale servers using a supported VM provider. Auto scaling can be used to automatically provision Servers or Docker Agents.
Note
If your license includes auto-scale configs, you will have 3 links underneath the table for All AutoScale Configs, All VM Provider Configs and All DNS Provider Configs. These allow you to see all of the configs available and make changes, but the recommended approach is to use the Edit option on a specific pool.
Create Pool
Click the Compute item in the navigation menu.
Select the Pools option in the dropdown menu.
Select Add from the top right of the Pools table.
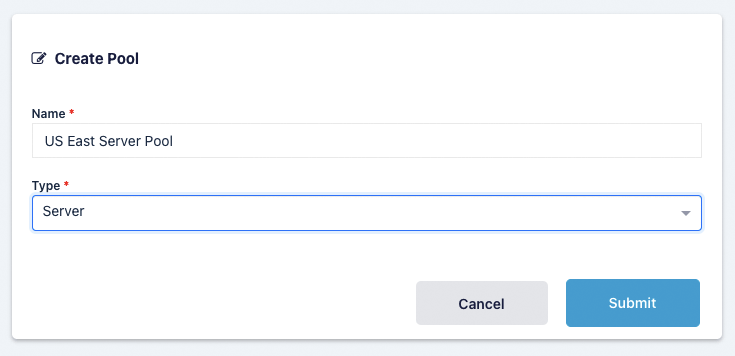
Provide a name for your server pool. The type can either by Docker Agent or Server.
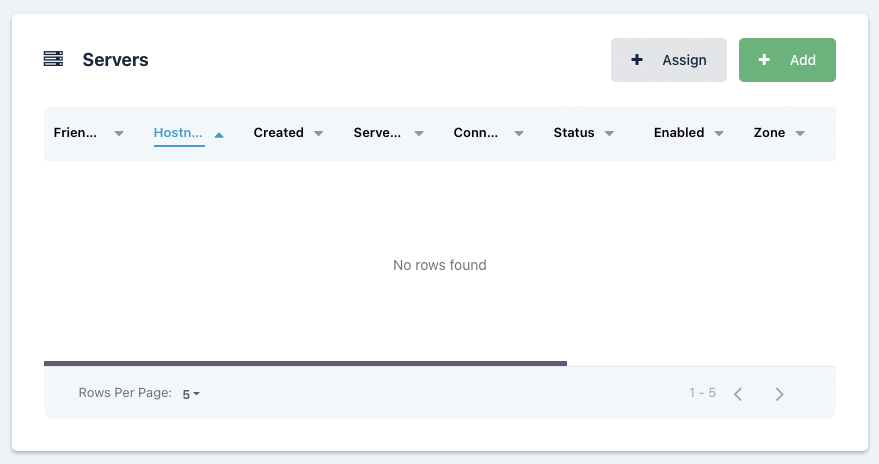
Servers List
This list is only shown for Pools of type Server
This list is almost identical to the Servers list with the exception that only servers that are assigned to this pool are shown. Use the assign button to assign existing servers to this pool.
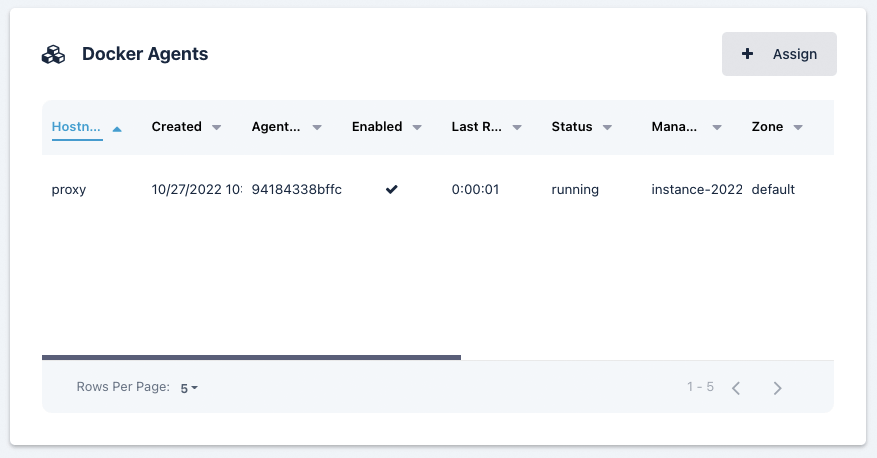
Docker Agents List
This list is only shown for Pools of type Docker Agent
This list is almost identical to the Agents list with the exception that only servers that are assigned to this pool. Use the assign button to assign existing agents to this pool.
AutoScale Configurations
Note
This feature requires an Enterprise license. Please contact your Kasm Technologies representative for details.
Kasm has the ability to automatically provision and destroy Servers and Docker Agents based on user demand. The auto scale configuration differs slightly between Servers and Agents.
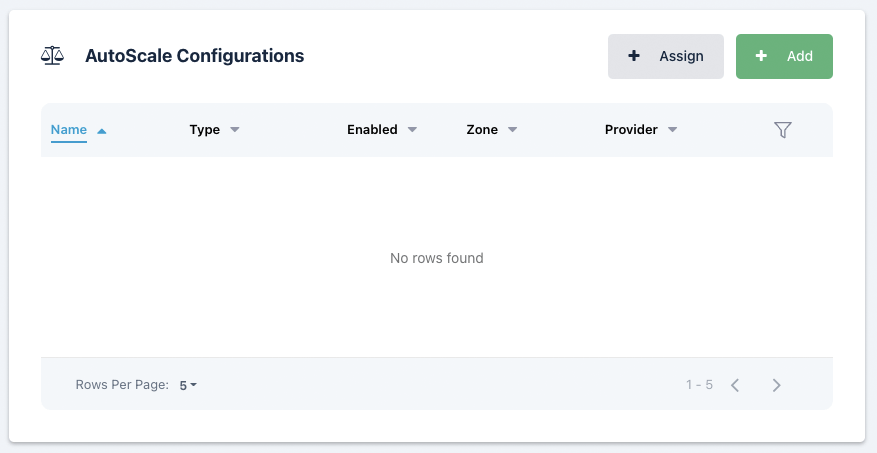
In this section you can Assign or Add AutoScale configurations, if you add an AutoScale configuration it will automatically be assigned to this pool with the AutoScale Type and Pool both set and prevented from being changed.
Clicking Add button on the Auto Scale Configuration table will walk you through a Wizard. The first step is the auto scale configuration, which is slightly different between a Server pool and a Docker Agent pool.
AutoScale Config (Server Pool)
This section covers the auto scale configuration step of the Wizard for Pools of type Server.
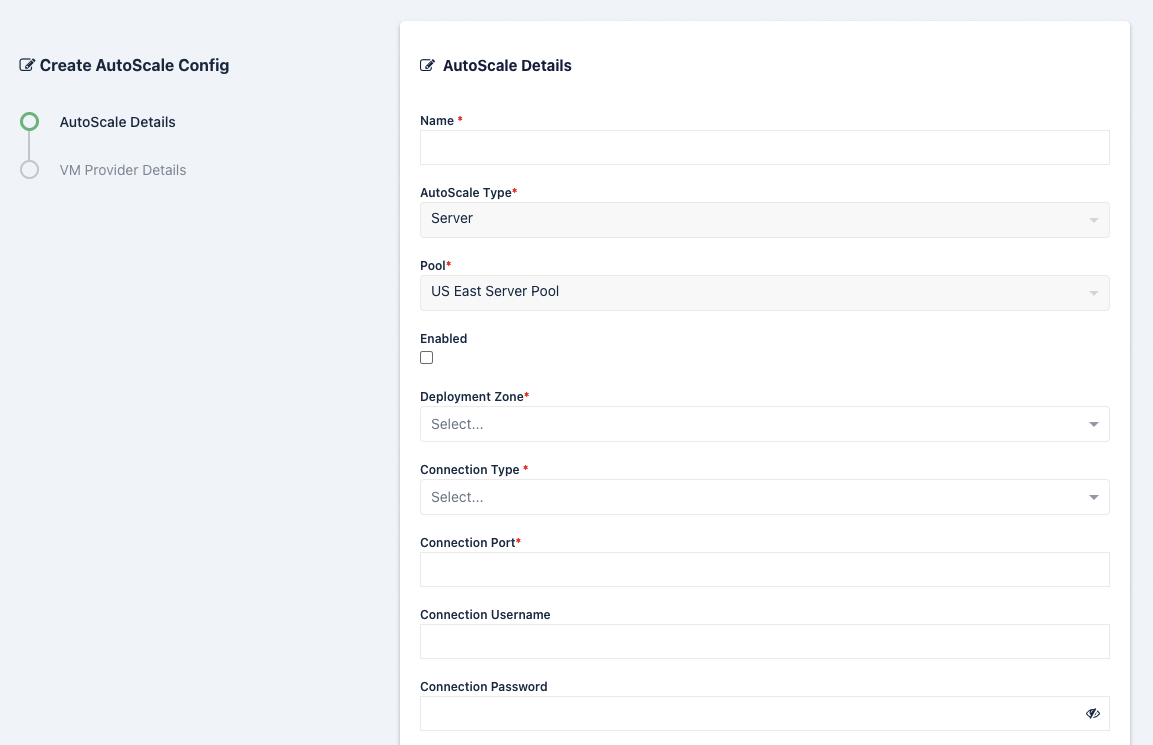
Name |
Description |
|---|---|
Name |
Name for the AutoScale config . |
AutoScale Type |
The type of AutoScale confog this is, either a Docker Agent or a Server. |
Pool |
Which pool this AutoScale config is attached to. |
Enabled |
Whether to enable this config or not. |
Deployment Zone |
Which zone this AutoScale config applies to. |
Connection Type |
Whether to use KasmVNC or RDP. |
Connection Port |
Which port to connect on. |
Connection Username |
Which username to connect to the server with. |
Connection Password |
Which password to connect to the server with. |
Connection Info (JSON) |
Any extra connection info. |
Create Active Directory Computer Record |
Whether to create an active directory record or not. |
Reusable |
Whether the connection reusable. |
Minimum Available Sessions |
The minimum available sessions there are. |
Max Simultaneous Sessions Per Server |
Max sessions per server allowed |
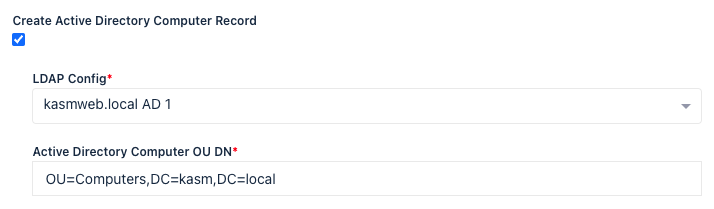
Create Active Directory Computer Record
As covered in the above table, the Auto Scaling configuration for a Server Pool allows you to automatically join new VMs to an active directory domain. If the checkbox for Create Active Directory Computer Record is checked two additional fields will be shown, LDAP Config and Active Directory Computer OU DN.
Kasm Workspaces creates the AD Computer record, but it does not join the computer to the domain, this needs to be done on the system itself. When Kasm creates the AD record, a temporary randomly generated password is created which can be used on the target VM to join it to Active Directory. Kasm can inject this password in a PowerShell script on the VM. That PowerShell script needs to be executed when the VM starts up, in order to complete the process of adding the VM to Active Directory. Below is an example PowerShell script, the special tags {ad_join_credential} and {domain} will be replaced by Kasm with the randomly generated password and domain name respectively. This script is placed in the VM Provider configuration in the Startup Script field.
$joinCred = New-Object pscredential -ArgumentList ([pscustomobject]@{{ UserName = $null; Password = (ConvertTo-SecureString -String '{ad_join_credential}' -AsPlainText -Force)[0] }})
Add-Computer -Domain "{domain}" -Options UnsecuredJoin,PasswordPass -Credential $joinCred -Force -Restart
Note
Some cloud providers will automatically execute this startup script when the VM boots, making it easy to get auto AD joining working end-to-end. Other cloud providers, such as Azure, do not automatically execute this script. See the details of each VM Config Provider.
LDAP Config The LDAP Config drop down allows you to select which LDAP configuration to use to add the computer record to Active Directory. The LDAP Configuration does not have to be enabled, this allows you to one LDAP configuration for Authentication and another for AD Computer record creation. If using LDAP for end-user authentication to Kasm Workspaces, the administrator can also configure single-sign on to the Windows systems.
Active Directory Computer OU DN This is the DN of the Active Directory Computer OU that you would like the computer records placed in.
Single Sign-On to Windows Systems via LDAP
When users login to Kasm via LDAP Authentication, they are able to create sessions to Windows systems that are joined to the same Active Directory domain and are configured for SSO credential pass-through. In the above table covering the Auto Scale configuration fields for Server Pools are the Connection Username and Connection Password fields. Place the value {sso_username} in the Connection Username field and place the value {sso_cred} in the field Connection Password in the Auto Scale configuration for the Server Pool. This requires that all users accessing servers in this Server Pool are authenticated to Kasm using LDAP authentication. See our Windows Deployment Guide video for a walk through of this topic and more.
AutoScale Config (Docker Agent Pool)
This section covers the auto scale configuration step of the Wizard for Pools of type Docker Agent.
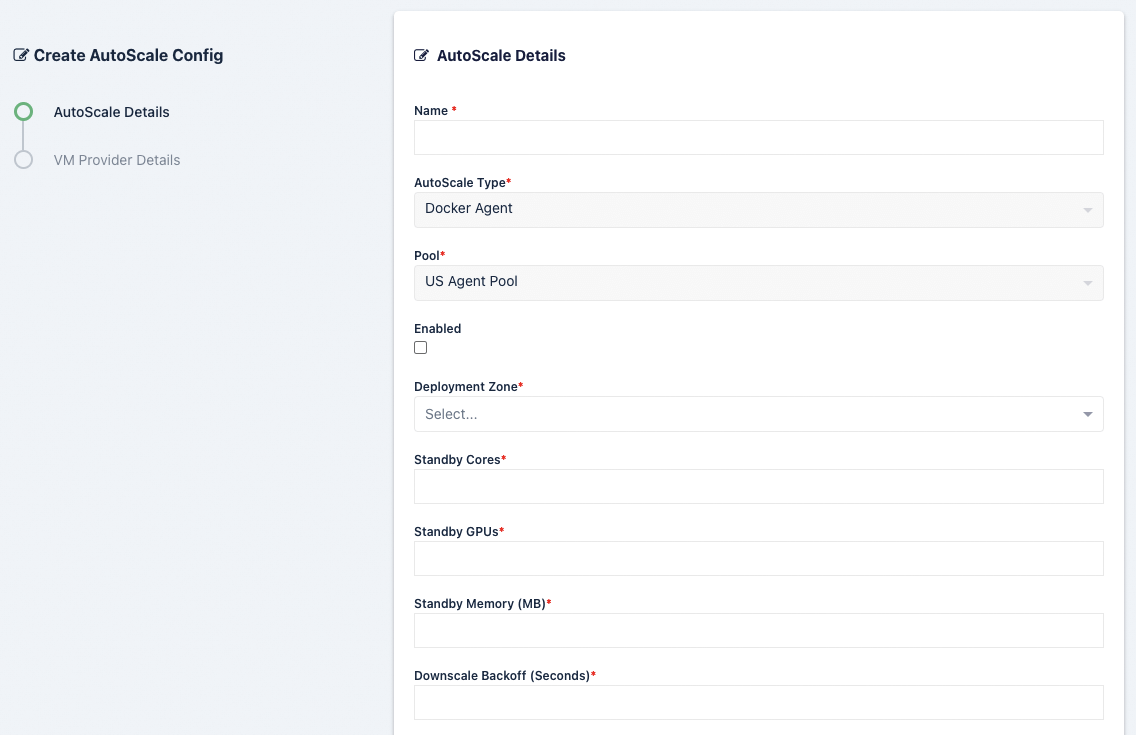
Name |
Description |
|---|---|
Name |
Name for the AutoScale config . |
AutoScale Type |
The type of AutoScale confog this is, either a Docker Agent or a Server. |
Pool |
Which pool this AutoScale config is attached to. |
Enabled |
Whether to enable this config or not. |
Deployment Zone |
Which zone this AutoScale config applies to. |
Standby Cores |
The number of standby cores that the system should try to keep “always available” at any given time in addition to any that is needed to satisfy the Staging Config requirements. If the number of available cores falls below this number, more Agents are created. If the number of available cores rises above this number, Agents are deleted as long as it wont result in the number of available cores falling below this number. A value of 0 indicates no additional standby compute is created. The AutoScaler will only provision enough compute according to the Staging Config requirements. |
Standby GPUs |
The number of standby GPUs that the system should try to keep “always available” at any given time in addition to any that is needed to satisfy the Staging Config requirements. If the number of available GPUs falls below this number, more Agents are created. If the number of available GPUs rises above this number, Agents are deleted as long as it wont result in the number of available GPUs falling below this number. A value of 0 indicates no additional standby compute is created. The AutoScaler will only provision enough compute according to the Staging Config requirements. |
Standby Memory (MB) |
The amount of memory (in MB) that the system should try to keep “always available” at any given time in addition to any that is needed to satisfy the Staging Config requirements. If the amount of available memory falls below this number, more Agents are created. If the amount of available memory rises above this number, Agents are deleted as long as it wont result in available amount falling below this number. A value of 0 indicates no additional standby compute is created. The AutoScaler will only provision enough compute according to the Staging Config requirements. |
Downscale Backoff (Seconds) |
This setting prevents prevents the system from downscaling (deleting Agents) for this amount of time (in seconds) when needed. This is useful for preventing the system from thrashing up and down if the available resource hover around an interval that would typically trigger autoscaling. |
Agent Cores Override |
When an Agent is created, the compute resource (e.g AWS EC2 / Digital Ocean Droplet) will have a set amount of CPU and Ram as defined by the cloud provider’s instance type. This setting should typically be set to match the instance type but can be set to a preferred value. |
Agent GPUs Override |
When an Agent is created, the compute resource (e.g AWS EC2 / Digital Ocean Droplet) will have a set number of GPUs as defined by the cloud provider’s instance type. This setting should typically be set to match the instance type but can be set to a higher number to allow oversubscribing. |
Agent Memory Override (GB) |
When an Agent is created, the compute resource (e.g AWS EC2 / Digital Ocean Droplet) will have a set amount of CPU and Ram as defined by the cloud provider’s instance type. This setting should typically be set to match the instance type but can be set to a preferred value. |
NGINX Cert |
The PEM encoded SSL certificate to use for the kasm_proxy role on the created Agents. This cert should be a wildcard for the Base Domain Name (e.g *.agents.kasm.example.com) |
NGINX Key |
The PEM encoded SSL Key to use for the kasm_proxy role on the created Agents. |
Register DNS |
If enabled, the Agent’s IP will be registered in DNS. |
Base Domain Name |
Define a base name for the automatic DNS registration for the Agent. The system will create a full name using <ID>.<Base Domain Name>. If the Base Domain Name is “agents.kasm.example.com”, the full DNS name generated will be <ID>.agents.kasm.example.com (e.g 123abcd.agents.kasm.example.com). This Base Domain Name, must already be a registered DNS zone within the cloud provider’s DNS system. |
VM Provider Configs
Note
This feature requires a special license. Please contact your Kasm Technologies representative for details.
Name |
Description |
VM Provider Configs |
Select an existing config or create a new config. If you select an existing config and change any of the details, those details will be changed for anything using the same VM Provider config. |
Provider |
Select a provider from AWS, Azure, Digital Ocean, Google Cloud or Oracle Cloud. If you select an existing provider this will be selected automatically. |
AWS Settings
A number of settings are required to be defined to use this functionality.
Name |
Description |
Name |
A name to use to identify the config. |
AWS Access Key ID |
The AWS Access Key used for the AWS API. |
AWS Secret Access Key |
The AWS Secret Access Key used for the AWS API. |
AWS: Region |
The AWS Region the EC2 Nodes should be provisioned in. e.g (us-east-1) |
AWS: EC2 AMI ID |
The AMI ID to use for the provisioned EC2 nodes. This should be an OS that is supported by the Kasm installer. |
AWS: EC2 Instance Type |
The EC2 Instance Type (e.g t3.micro). Note the Cores and Memory override settings don’t necessarily have to match the instance configurations. This is to allow for over provisioning. |
AWS: Max EC2 Nodes |
The maximum number of EC2 nodes to provision regardless of the need for available free slots |
AWS: EC2 Security Group IDs |
A Json list containg security group IDs to assign the EC2 nodes. e.g |
AWS: EC2 Subnet ID |
The subnet ID to place the EC2 nodes in. |
AWS: EC2 EBS Volume Size (GB) |
The size of the root EBS Volume for the EC2 nodes. |
AWS: EC2 EBS Volume Type |
The EBS Volume Type (e.g gp2) |
AWS: EC2 IAM |
The IAM to assign the EC2 Nodes. Administrators may want to assign CloudWatch IAM access. |
AWS: EC2 Custom Tags |
A Json dictionary for custom tags to assigned on auto-scaled Agent EC2 Nodes. e.g |
AWS: EC2 Startup Script |
When the EC2 Nodes are provision this script is executed. The script is responsible for installing and configuring the Kasm Agent. |
SSH Keys |
The SSH Key pair to assign the EC2 node |
Azure Settings
A number of settings are required to be defined to use this functionality. The Azure settings appear in the Deployment Zone configuration when the feature is licensed.
Register Azure app
We must create an API key for Kasm to use to interface with Azure. Azure call these apps, and we will walk through registering one along with the required permissions.
Register an app by going to the Azure Active Directory service in your Azure portal.
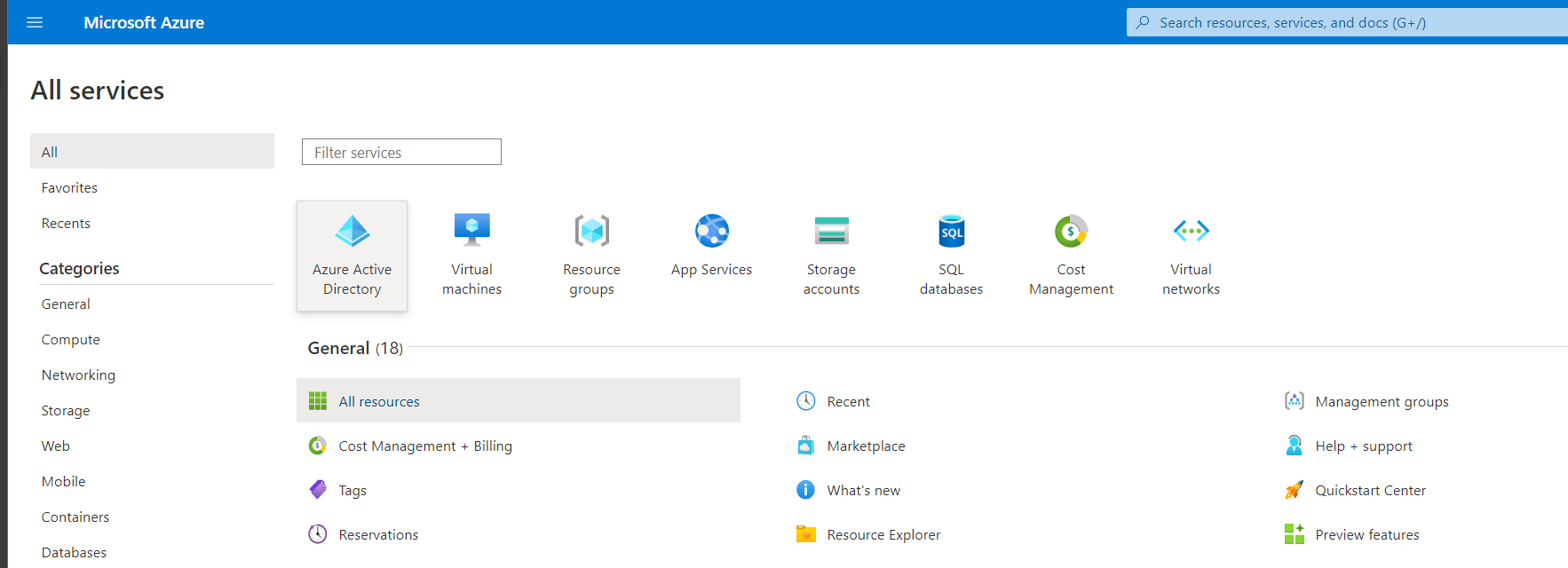
From the Add dropdown select App Registration
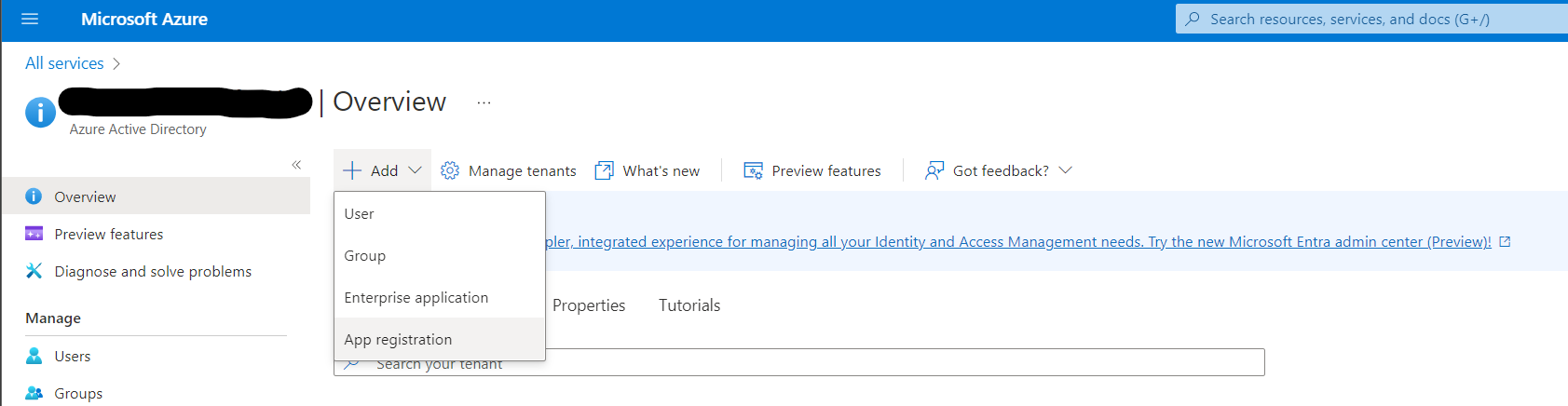
Give this app a human-readable name such as Kasm Workspaces
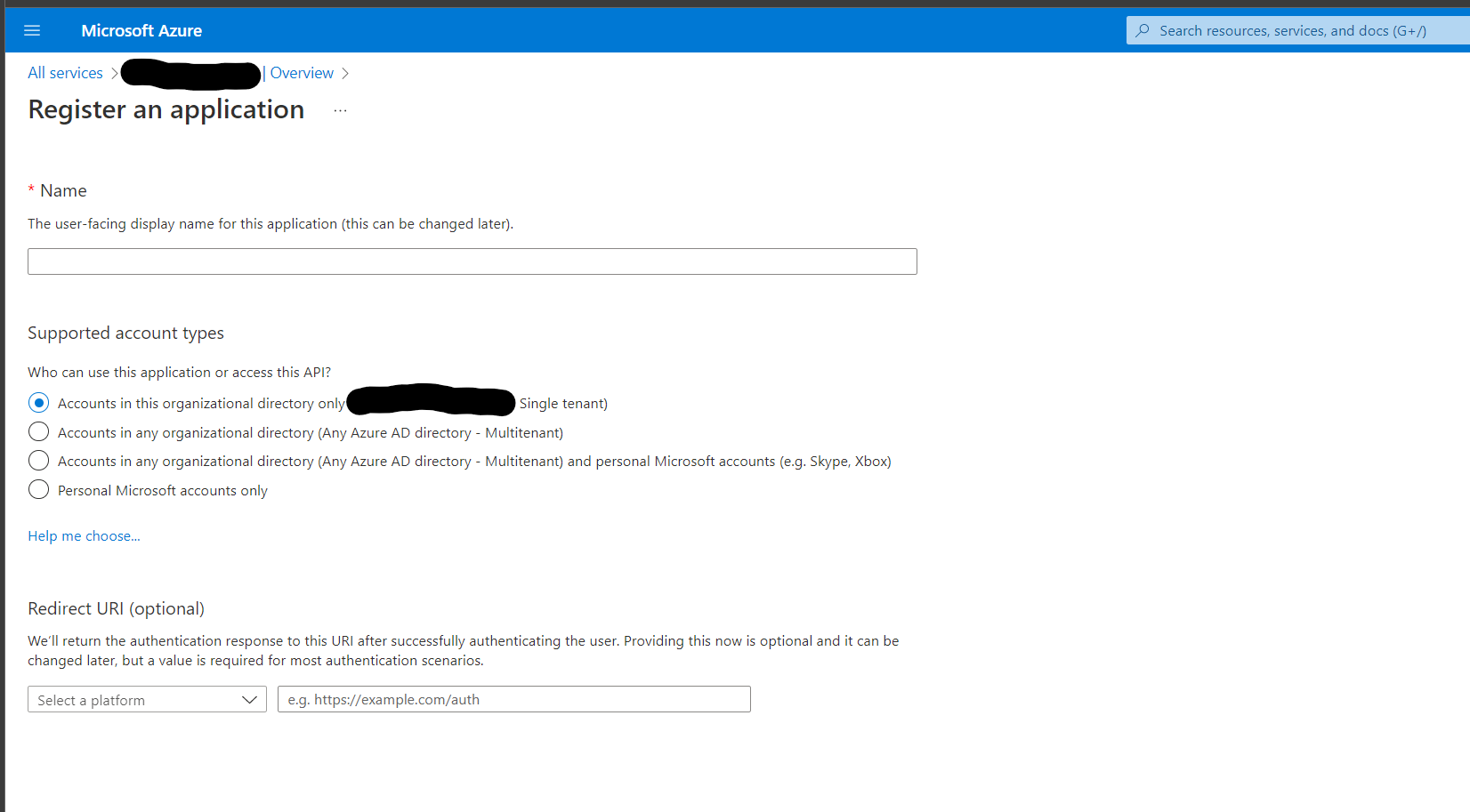
Go to Resource Groups and select the Resource Group that Kasm will autoscale in.
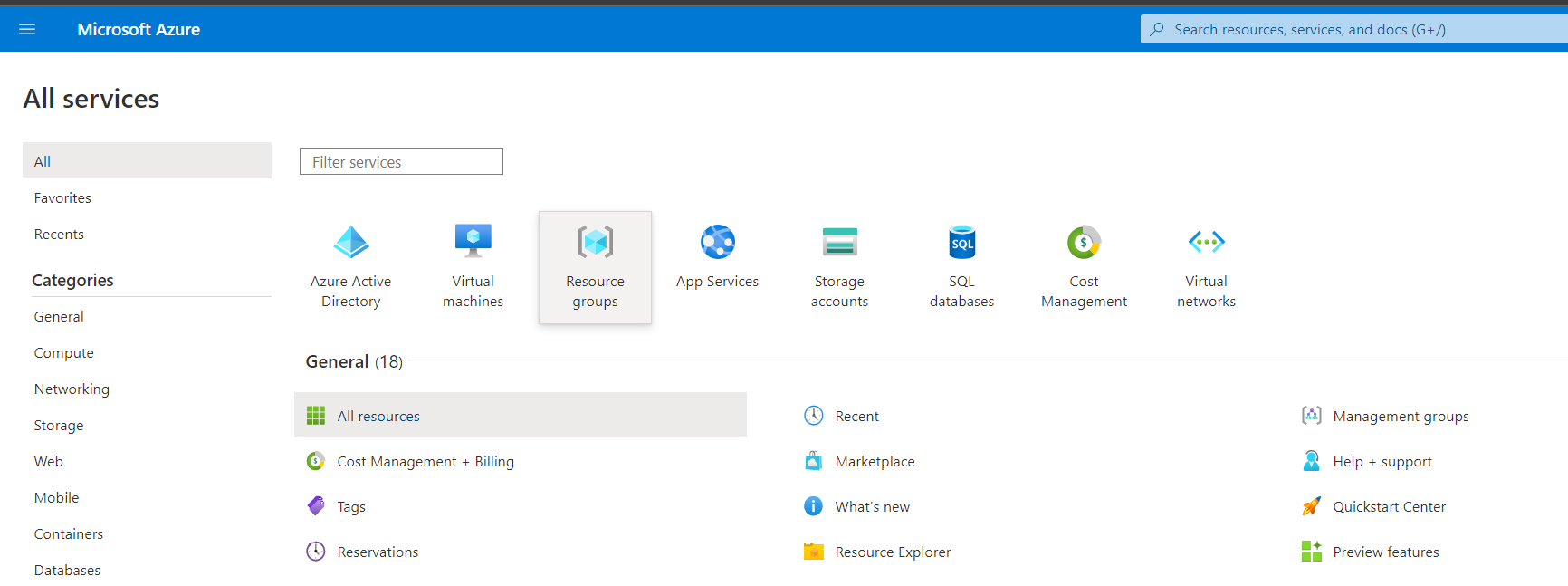
Select Access Control (IAM)
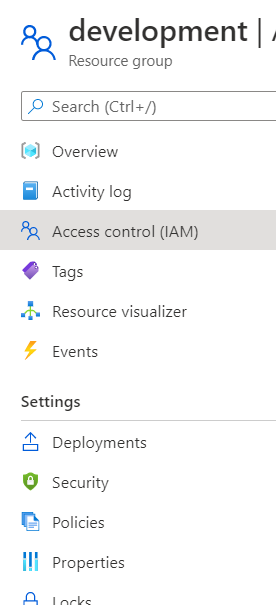
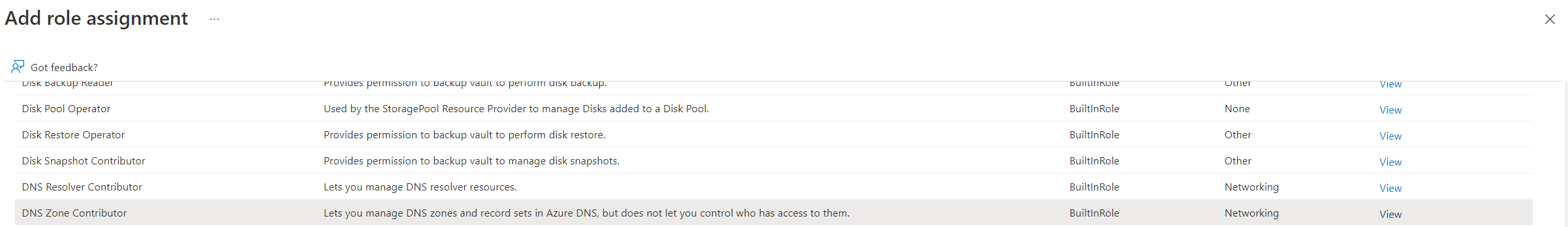
From the Add drop down select Add role assignment
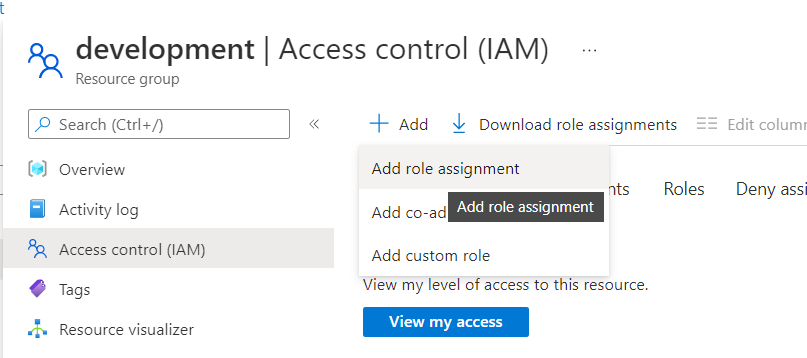
The app we created in Azure will need two roles, first select the Virtual Machine Contributor role, then on the next page select the app by typing in the name e.g. Kasm Workspaces
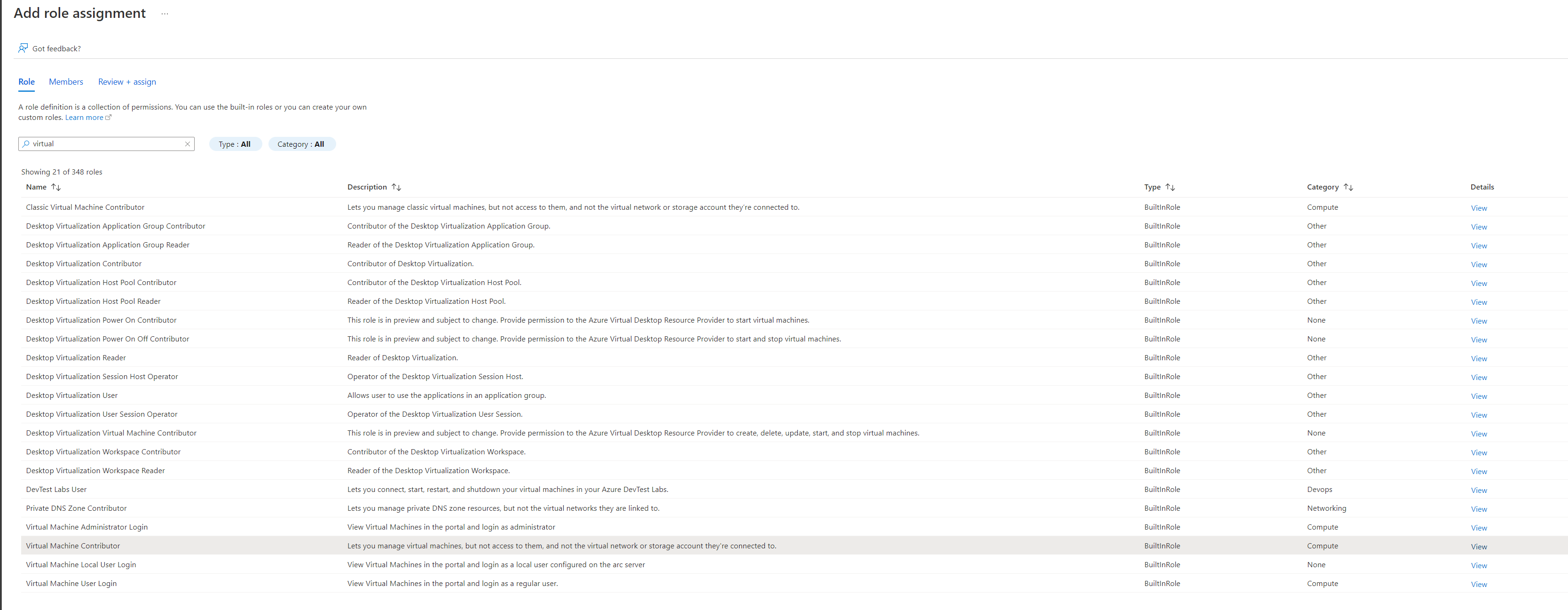
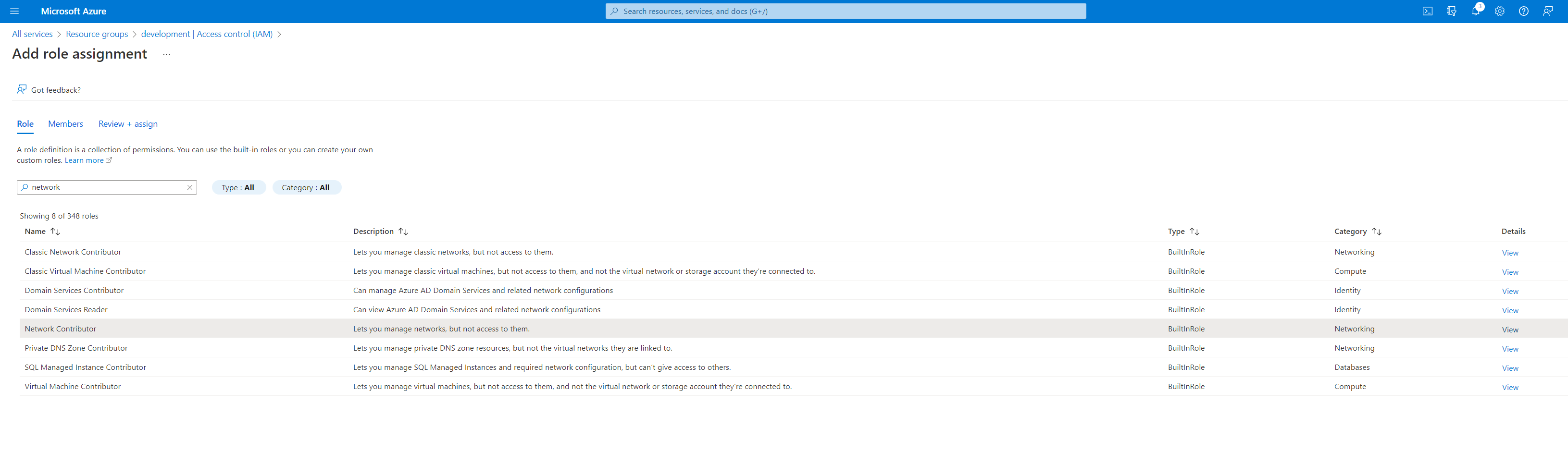
Go through this process again to add the Network Contributor and the DNS Zone Contributor roles
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Subscription ID |
The Subscription ID for the Azure Account.
This can be found in the Azure portal by searching for Subscriptions in the search bar in Azure home then selecting the subscription you want to use.
(e.g |
Resource Group |
The Resource Group the DNS Zone and/or Virtual Machines belong to (e.g |
Tenant ID |
The Tenant ID for the Azure Account.
This can be found in the Azure portal by going to Azure Active Directory using the search bar in Azure home.
(e.g |
Client ID |
The Client ID credential used to auth to the Azure Account.
Client ID can be obtained by registering an application within Azure Active Directory.
(e.g |
Client Secret |
The Client Secret credential created with the registered applicaiton in Azure Active Directory. (e.g |
Azure Authority |
Which Azure authority to use, there are four, Azure Public Cloud, Azure Government, Azure China and Azure Germany. |
Region |
The Azure region where the Agents will be provisioned. (e.g |
Max Instances |
The maximum number of Azure VMs to provision regardless of the need for additional resources. |
VM Size |
The size configuration of the Azure VM to provision (e.g |
OS Disk Type |
The disk type to use for the Azure VM. (e.g |
OS Disk Size (GB) |
The size (in GB) of the boot volume to assign the compute instance. |
OS Image Reference (JSON) |
The OS Image Reference configuration for the Azure VMs (e.g
|
Image is Windows |
Is this a windows VM being created |
Network Security Group |
The network security group to attach to the VM (e.g |
Subnet |
The subnet to attach the VM to (e.g |
Assign Public IP |
If checked, the VM will be assigned a public IP. If no public ip IP is assigned the VM must ne attached to a standard load balancer of the subnet must have a NAT Gateway or user-defined route (UDR). If a public IP is used, the subnet must not also include a NAT Gateway. Reference |
Tags (JSON) |
A JSON dictionary of custom tags to assign to the VMs (e.g |
OS Username |
The login username to assign to the new VM (e.g |
OS Password |
The login password to assign to the new VM. Note: Password authentication is disabled for SSH by default |
SSH Public Key |
The SSH public key to install on the VM for the defined user: (e.g |
Agent Startup Script |
When instances are provisioned, this script is executed and is responsible for installing and configuring the Kasm Agent. |
Config Override (JSON) |
Custom configuration may be added to the provision request for advanced use cases. The emitted json structure is visible by clicking JSON View when inspecting the VM in the Azure console.
The keys in this configuration can be used to update top level keys within the emitted json config (e.g |
Digital Ocean Settings
A number of settings are required to be defined to use this functionality.
Warning
Please review Tag Does Not Exist Error for known issues and workarounds
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Token |
The token to use to connect to this VM |
Max Droplets |
The maximum number of Digital Ocean droplets to provision , regardless of whether more are needed to fulfill user demand. |
Region |
The Digital Ocean Region where droplets should be provisioned. (e.g nyc1) |
Image |
The Image to use when creating droplets. (e.g docker-18-04) |
Droplet Size |
The droplet size configuration (e.g c-2) |
Tags |
A tag to assign the droplet when it is created. This tag must already exist in the Digital Ocean Account |
SSH Key Name |
The SSH Key to assign to the newly created droplets. The SSH Key must already exist in the Digital Ocean Account. |
Firewall Name |
The name of the Firewall to apply to the newly created droplets. This Firewall must already exist in the Digital Ocean Account. |
Startup Script |
When droplets are provision this script is executed. The script is responsible for installing and configuring the Kasm Agent. |
Tag Does Not Exist Error
Upon first testing AutoScaling with Digital Ocean, you may be presented with the error similar to the follow:
Future generated an exception: tag zone:abc123 does not exist
traceback:
..
File "digitalocean/Firewall.py", line 225, in add_tags
File "digitalocean/baseapi.py", line 196, in get_data
digitalocean.DataReadError: tag zone:abc123 does not exist
process: manager_api_server
This error occurs when Kasm Workspaces tries to assign a unique tag based on the Zone Id to the Digital Ocean Firewall.
If that tag does not already exist in Digital Ocean, the operation will fail and present the error.
To workaround the issue, manually create a tag matching the one specified in the error (e.g zone:abc123) via
the Digital Ocean console. This can be done via API, or simply creating the tag on a temporary Droplet.
Google Cloud (GCP) Settings
A number of settings are required to be defined to use this functionality. The GCP settings appear in the Deployment Zone configuration when the feature is licensed.
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
GCP Credentials |
The JSON formatted credentials for the service account used to authenticate with GCP: Ref |
Max Instances |
The maximum number of GCP compute instances to provision regardless of the need for additional resources. |
Project ID |
The Google Cloud Project ID (e.g pensive-voice-547511) |
Region |
The region to provision the new compute instances. (e.g us-east4) |
Zone |
The zone the new compute instance will be provisioned in (e.g us-east4-b) |
Machine Type |
The Machine type for the GCP compute instances. (e.g e2-standard-2) |
Machine Image |
The Machine Image to use for the new compute instance. (e.g projects/ubuntu-os-cloud/global/images/ubuntu-2004-focal-v20211212) |
Boot Volume GB |
The size (in GB) of the boot volume to assign the compute instance. |
Disk Type |
The disk type for the new instance. (e.g pd-ssd) |
Customer Managed Encryption Key (CMEK) |
The optional path to the Customer Managaged Encryption Key (CMEK) (e.g projects/pensive-voice-547511/locations/global/keyRings/my-keyring/cryptoKeys/my-key |
Network |
The path of the Network to place the new instance. (e.g projects/pensive-voice-547511/global/networks/default) |
Sub Network |
The path of the Sub Network to place the new instance. (e.g projects/pensive-voice-547511/regions/us-east4/subnetworks/default) |
Public IP |
If checked, a public IP will be assigned to the new instances |
Network Tags (JSON) |
A JSON list of the Network Tags to assign the new instance. (e.g |
Custom Labels (JSON) |
A JSON dictionary of Custom Labels to assign the new instance (e.g |
Metadata (JSON) |
A JSON list of metadata objects to add to the instance.
(e.g |
Service Account (JSON) |
A JSON dictionary representing for a service account to attach to the instance.
(e.g |
Guest Accelerators (JSON) |
A JSON list representing the guest accelerators (e. GPUs) to attach to the instance.
(e.g |
GCP Config Override (JSON) |
A JSON dictionary that can be used to customize attributes of the VM request. The only attributes that cannot be overridden
are |
Startup Script |
When instances are provisioned, this script is executed and is responsible for installing and configuring the Kasm Agent. |
Oracle Cloud (OCI) Settings
A number of settings are required to be defined to use this functionality. The OCI settings appear in the Deployment Zone configuration when the feature is licensed.
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
User OCID |
The OCID of the user to authenticate with the OCI API. (e.g ocid1.user.oc1..xyz) |
Public Key Fingerprint |
The public key fingerprint of the authenticated API user. (e.g xx:yy:zz:11:22:33) |
Private Key |
The private key (PEM format) of the authenticated API user. |
Region |
The OCI Region name. (e.g us-ashburn-1) |
Tenancy OCID |
The Tenancy OCID for the OCI account. (e.g ocid1.tenancy.oc1..xyz) |
Compartment OCID |
The Compartment OCID where the auto-scaled agents will be placed. (ocid1.compartment.oc1..xyx) |
Max Instances |
The maximum number of OCI compute instances to provision regardless of the need for available free slots. |
Availability Domain |
The availability domain where the OCI compute instances will be placed. (e.g BEol:US-ASHBURN-AD-1) |
Image OCID |
The OCID of the Image to use when creating the compute instances. (e.g ocid1.image.oc1.iad.xyz) |
Shape |
The name of the shape used for the created compute instances. (e.g VM.Standard.E4.Flex) |
Flex CPUs |
The number of OCPUs to assign the compute instance. This is only applicable when a Flex shape is used. |
Flex Memory GB |
The amount of memory (in GB) to assign the compute instance. This is only applicable when a Flex shape is used. |
Boot Volume GB |
The size (in GB) of the boot volume to assign the compute instance. |
Custom Tags (JSON) |
A Json dictionary of custom freeform tags to assigned the auto-scaled instances. e.g |
Subnet OCID |
The OCID of the Subnet where the auto-scaled instances will be placed. (e.g ocid1.subnet.oc1.iad.xyz) |
SSH Public Key |
The SSH public key to insert into the compute instances. (e.g ssh-rsa XYABC) |
Startup Script |
When instances are provisioned, this script is executed and is responsible for installing and configuring the Kasm Agent. |
DNS Provider Configs
Note
This feature requires a special license. Please contact your Kasm Technologies representative for details.
Name |
Description |
DNS Provider Configs |
Select an existing config or create a new config. If you select an existing config and change any of the details, those details will be changed for anything using the same DNS Provider config. |
Provider |
Select a provider from AWS, Azure, Digital Ocean, Google Cloud or Oracle Cloud. If you select an existing provider this will be selected automatically. |
AWS DNS Provider Settings
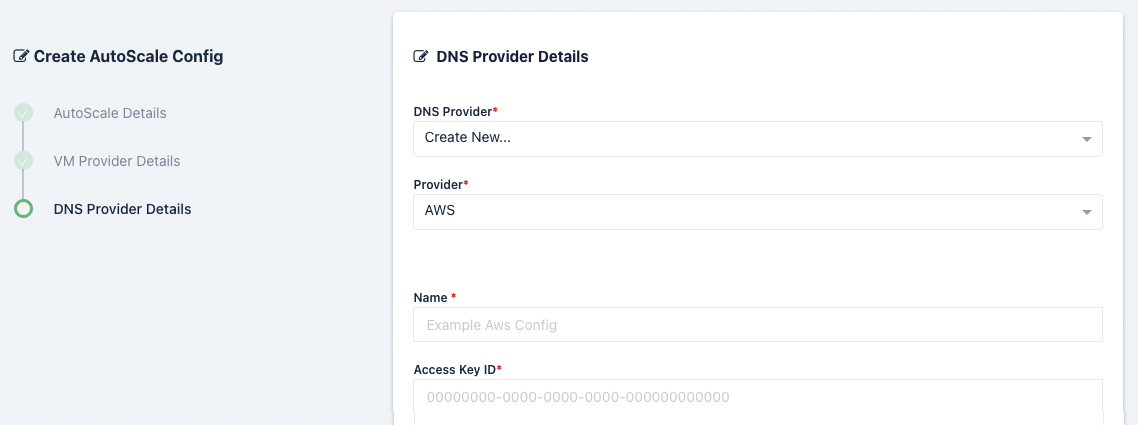
Name |
Description |
Name |
A name to use to identify the config. |
Access Key ID |
The AWS Access Key used for the AWS API. |
Access Key Secret |
The AWS Secret Access Key used for the AWS API. |
Azure DNS Provider Settings
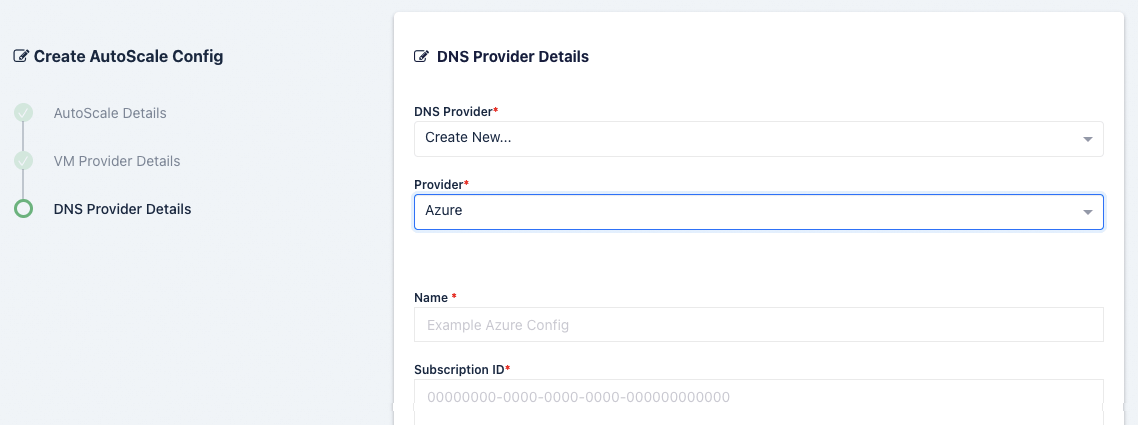
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Subscription ID |
The Subscription ID for the Azure Account.
This can be found in the Azure portal by searching for Subscriptions in the search bar in Azure home then selecting the subscription you want to use.
(e.g |
Resource Group |
The Resource Group the DNS Zone and/or Virtual Machines belong to (e.g |
Tenant ID |
The Tenant ID for the Azure Account.
This can be found in the Azure portal by going to Azure Active Directory using the search bar in Azure home.
(e.g |
Client ID |
The Client ID credential used to auth to the Azure Account.
Client ID can be obtained by registering an application within Azure Active Directory.
(e.g |
Client Secret |
The Client Secret credential created with the registered applicaiton in Azure Active Directory. (e.g |
Azure Authority |
Which Azure authority to use, there are four, Azure Public Cloud, Azure Government, Azure China and Azure Germany. |
Region |
The Azure region where the Agents will be provisioned. (e.g |
Digital Ocean DNS Provider Settings
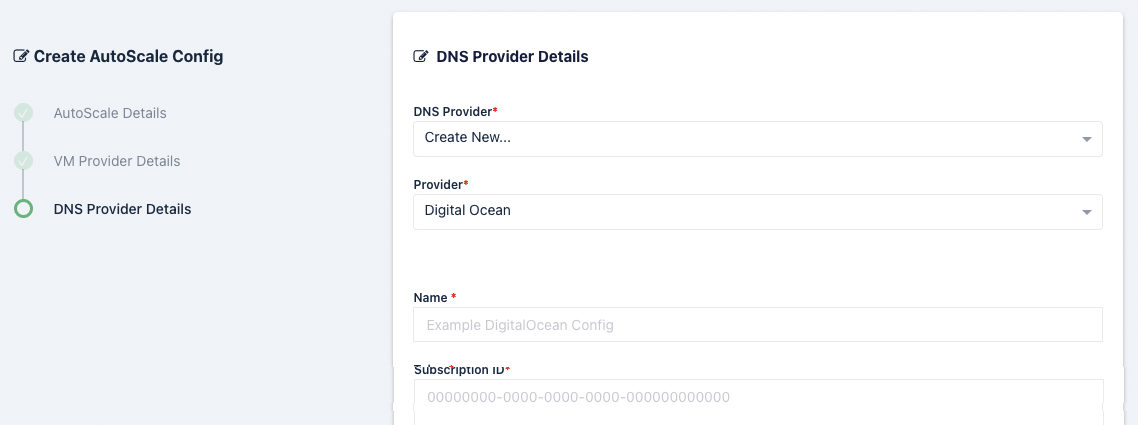
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Token |
The token to use to connect to this VM |
Google Cloud (GCP) DNS Provider Settings
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Project |
The Google Cloud Project ID (e.g pensive-voice-547511) |
Credentials |
The JSON formatted credentials for the service account used to authenticate with GCP: Ref |
Oracle Cloud (OCI) DNS Provider Settings
Name |
Description |
|---|---|
Name |
A name to use to identify the config. |
Fingerprint |
The public key fingerprint of the authenticated API user. (e.g xx:yy:zz:11:22:33) |
Tenancy OCID |
The Tenancy OCID for the OCI account. (e.g ocid1.tenancy.oc1..xyz) |
Region |
The OCI Region name. (e.g us-ashburn-1) |
Compartment OCID |
The Compartment OCID where the auto-scaled agents will be placed. (ocid1.compartment.oc1..xyx) |
User OCID |
The OCID of the user to authenticate with the OCI API. (e.g ocid1.user.oc1..xyz) |
Private Key |
The private key (PEM format) of the authenticated API user. |