Running Kasm with Tailscale
This guide will cover setting up a single server Kasm instance with a basic Tailscale configuration. If you are looking to run a Tailscale as a sidecar container to access other Tailscale devices only from stock Workspaces containers please see VPN Sidecar Containers.
Table of Contents
Network architecture overview
For our setup we had three nodes.
An Ubuntu 20.04 LTS graphical desktop running chromium to access the Kasm UI.
An Ubuntu 20.04 LTS server that we will perform a single server install of Kasm on.
An Ubuntu 20.04 LTS server that we configured as a Tailscale exit node. (This is only used in Configuring Kasm with a Tailscale exit node )
Tailscale
This guide uses Tailscale version 1.18.2. This guide assumes you already have a Tailscale account and are familiar with using Tailscale.
Kasm with Tailscale without an exit node
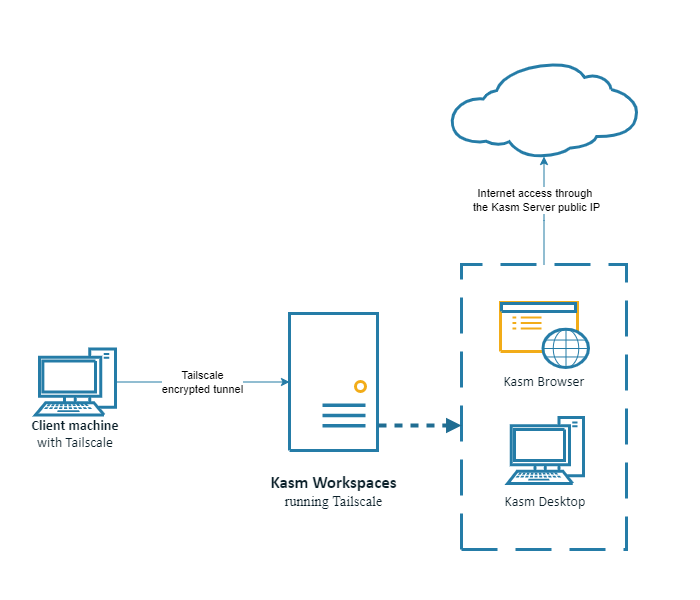
Setup a single server Kasm instance as described in the single server installation guide. Verify that you can access the Kasm web app running on port 443 at https://<WEBAPP_SERVER> Install Tailscale on the Kasm node following the instructions at Tailscale Ubuntu 20.04 LTS install Take note of the Tailscale ip address for the Kasm server.
sudo tailscale ip --4
Verify you can access the Kasm web app at the Tailscale ip address from a Tailscale client.
In order for clients to properly make connections to Kasm sessions when using a reverse proxy, the Upstream Auth Address setting for each Deployment Zone must be updated. Update the Upstream Auth Address with the public (non-tailscale) IP or FQDN of the Kasm Workspaces server. See Update Zones for more information.
Kasm workspaces is now working with Tailscale. Outbound Kasm session traffic will go out the normal pubic ip, if the desire is to route traffic from Kasm sessions through a Tailscale exit node continue with Configuring Kasm with a Tailscale exit node.
Configuring Kasm with a Tailscale exit node
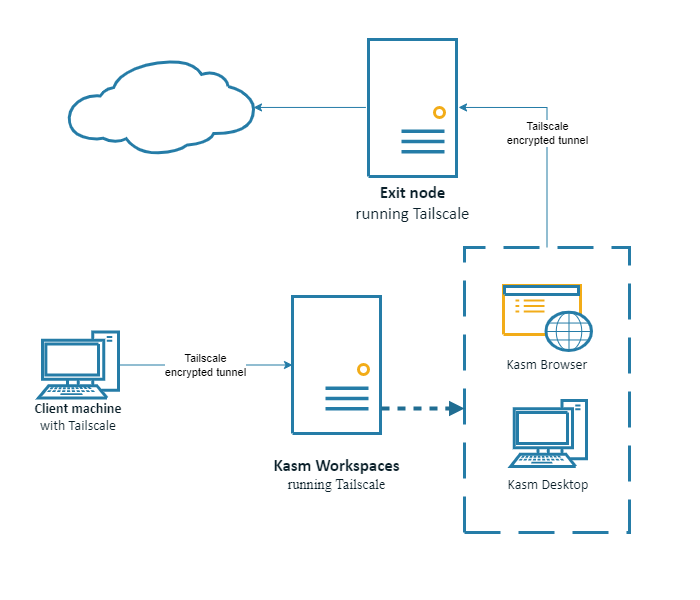
Perform the setup in Kasm with Tailscale without an exit node. Once that setup is complete ensure that you have a Tailscale exit node configured. Instructions are available at: Exit Nodes (route all traffic) Update the Tailscale configuration for the Kasm server with the new exit node.
sudo tailscale up --exit-node=<Tailscale ip of the exit node> --exit-node-allow-lan-access
Note
Adding the --exit-node-allow-lan-access parameter is required to be able to access the Kasm web app.
Next we will need the IP address of the Kasm proxy server to update the Upstream Auth Address in the zone configuration.
sudo docker exec -it kasm_proxy ip a
Use the non loopback address and update each Deployment Zone with the new Upstream Auth Address. See Update Zones for more information.
Note
Uploading files to the Kasm session does not work with a Tailscale exit node configured.
Troubleshooting
During our configuration of Tailscale we ran into issues with DNS. We were able to solve our issue by adding a public DNS server to the Tailscale administration page under DNS (This step may not apply to all configurations of Tailscale)