Browser Isolation
One of the biggest security risks to organizations is direct internet access to the endpoint. Employees typically need access to the internet to do their jobs, but the proliferation of viruses, malware and phishing attacks pose a significant risk. A single mis-click and the organizations infrastructure can be exposed to viruses and ransomware.
Browser Isolation categorically removes this risk, by shifting the paradigm of how this internet is accessed. Users can still access the internet from their endpoint systems, but instead use a remote, containerized browser that is accessed directly from their native browser.
The Kasm Chrome container being accessed from Internet Explorer
Kasm Workspaces provides browser isolation by running a remote, containerized browser that is rendered inside the user’s local browser. This allows organizations to cut off direct internet access to the endpoint and tightly control what goes in and out of the network. This is the ultimate protection from viruses, ransomware, and other types of malware. It also enhances data loss prevention programs by allowing administrative control items uploaded , downloaded and copied to the Kasm.
Seamless Browsing
To make browser isolation feel more seamless to the end users, Kasm Workspaces provides additional interfaces that make regular tasks feel the same. For example, when the user attempts to navigate to a website using their local browser, the request is intercepted, A Kasm remote browser is shown, and the remote browser navigates to original website requested.
In similar fashion if a user clicks a link in local document or email, the local browser is launched, loads the Kasm remote browser, and navigates to the link that was in the document.
/go URL
Kasm Workspaces exposes a /go url that is used to launch or resume as Default Kasm for a user. kasm_url can also be passed as a query argument to this URL and exposed as a variable when defining Docker Exec Config to launch a new browser tab.
https://<kasm-server>/#/go?kasm_url=<destination-url>
https://kasm.company.local/#/go?kasm_url=wikipedia.com
Note
The Default Kasm can be configured as a Group Setting or as a User Setting
Auto Login
Kasm offers a group and user setting to automatically launch users into a Kasm after login. The user will have the default Kasm that is configured on either a group or user setting. This is similar to the Go URL but it does not require the user to explicitly go to the /go URL. It pushes them directly after login. This is useful when users want to be abstracted from the image creation and dashboard interface.
The User attribute will override the group setting therefore if some users want to still be pushed to the user dashboard after login they may set the auto login to false.
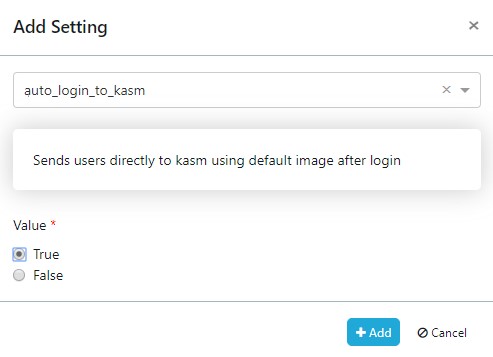
Use the group setting auto_login_to_kasm
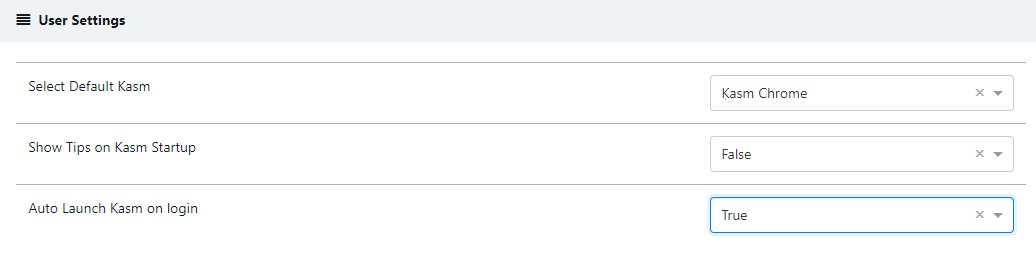
Or Use the User setting on an individual basis
Workflow
Seamless browsing works by intercepting the user’s original request and sending the client a redirect to Kasm Workspaces with the original request URL encoded in the kasm_url parameter. The client’s browser then navigates to Kasm Workspaces and the isolated browser running inside the Kasm sandbox then navigates to the originally requested URL.
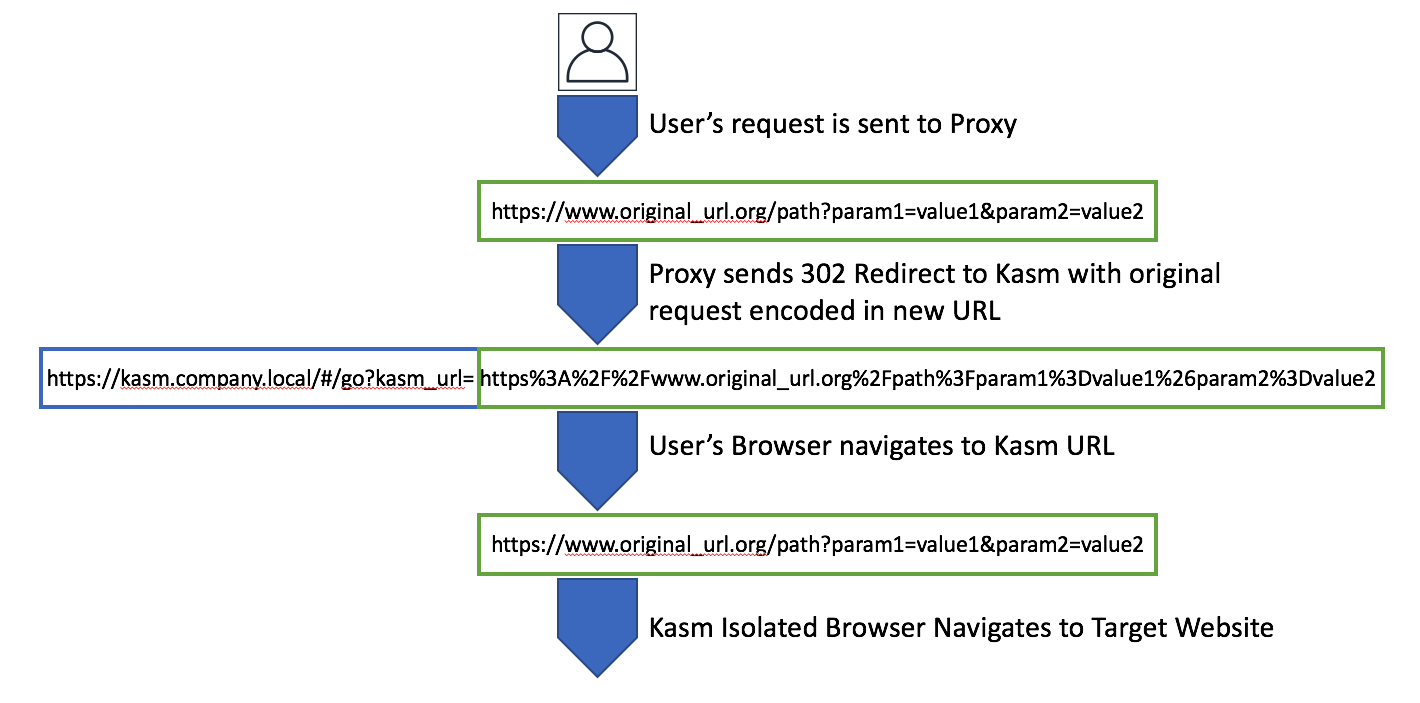
Proxy Redirection Workflow
In order to do this redirection an explicit or implicit forward proxy is needed. Most large organizations will have a forward poxy. In order to do redirection with URL encoding of the original request, the proxy must be capable of configuring custom rules. We have included configuration examples for F5 , BlueCoat and Palo Alto vendors.
Forward Proxy
An explicit forward proxy is one that is explicitly configured in the browser or operating system. Most enterprise forward proxies will allow you to create a policy that will properly redirect users request to Kasm. The system needs to redirect, using HTTPS status code 302, to https://kasm.company.local/#/go?kasm_url=ORIGINAL_URL where kasm.company.local is the hostname of your Kasm installation and ORIGINAL_URL is the user’s originally requested URL. This URL needs to be URL encoded. The following sections cover different forward proxy implementations. If your organization already has a compatible proxy in place, then creating a new policy to redirect is all that is needed. If a proxy is not already in place, clients will need the organizations root CA cert trusted by their browser and/or Operating system. If the proxy is an explicit proxy, the browser and/or operating system will need proxy settings configured.
BlueCoat
The BlueCoat proxy can be configured to redirect users to Kasm and encode the orginal request so that Kasm can navigate the isolated browser to the original request. The following link provides a similar example, except this policy redirects users based on URLs that are not categorized. So the rule needs to be modifed to trigger for all URLs, whith the exception of ‘https://kasm.company.local’ (replace with your Kasm installation domain name). The return code needs to be 302 instead of 307, and the destination URL needs to be modified to ‘https://kasm.company.local/#/go?kasm_url=$(1)’.
F5
An F5 acting as a forward proxy for an enterprise network can redirect users to Kasm and block direct access to the interent. This is done using an iRule. In he following example, kasm.company.local is the domain name of the Kasm installation.
when HTTP_REQUEST {
if { ([HTTP::host] != "kasm.company.local") and ([TCP::local_port] == 80) } {
HTTP:redirect https://kasm.company.local/#/go?kasm_url=http://[HTTP::host][HTTP::uri]
}
if { ([HTTP::host] != "kasm.company.local") and ([TCP::local_port] == 443) } {
HTTP:redirect https://kasm.company.local/#/go?kasm_url=https://[HTTP::host][HTTP::uri]
}
}
Palo Alto
The Palo Alto Next Gen Firewall can be configured to redirect users to Kasm by utilizing custom Response Pages for URL Filtering block, override or continue actions. Administrators may desire to restrict users from accessing certain URLs or categories directly, and instead present users with a special Response Page with the option to visit the link in isolation via Kasm, or even automatically redirect them.
Please consult the following vendor documentation for configuration steps. https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/url-filtering/url-filtering-concepts/url-filtering-response-pages.html
Below are example block pages that may be used to redirect users.
<html>
<head>
<meta http-equiv="refresh" content="0; url=https://kasm.server/#/go?kasm_url=<url/>">
</head>
</html>
<html>
<head>
<title>Web Page Blocked</title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<META HTTP-EQUIV="PRAGMA" CONTENT="NO-CACHE">
<meta name="viewport" content="initial-scale=1.0">
<style>
#content {
border:3px solid#aaa;
background-color:#fff;
margin:1.2em;
padding:1.2em;
font-family:Tahoma,Helvetica,Arial,sans-serif;
font-size:1em;
}
h1 {
font-size:1.2em;
font-weight:bold;
color:#196390;
}
b {
font-weight:normal;
color:#196390;
}
form td, form input {
font-size: 1em;
font-weight: bold;
}
#formtable {
height: 100%;
width: 100%;
}
#formtd {
vertical-align: middle;
}
#formdiv {
margin-left: auto;
margin-right: auto;
}
</style>
<script type="text/javascript">
function pwdCheck() {
if(document.getElementById("pwd")) {
document.getElementById("continueText").innerHTML = "If you require access to this page, have an administrator enter the override password here:";
}
}
</script>
</head>
<body bgcolor="#e7e8e9">
<div id="content">
<h1>Web Page Blocked</h1>
<p>Access to the web page you were trying to visit has been blocked in accordance with company policy. Please contact your system administrator if you believe this is in error.</p>
<p><b>User:</b> <user/> </p>
<p><b>URL:</b> <url/> </p>
<p><b>Category:</b> <category/> </p>
<a href="https://kasm.server/#/go?kasm_url=<url/>">Open Site in Kasm</a>
<hr>
<p id="continueText">If you feel this page has been incorrectly blocked, you may click Continue to proceed to the page. However, this action will be logged.</p>
<div id="formdiv">
<pan_form/>
<style>
#dError {
background-color: #FFFF88;
color: #E10000;
margin-top: 10px;
padding-top: 10px;
padding-bottom: 10px;
margin-left: 10px;
margin-right: 10px;
padding-left: 10px;
padding-right: 10px;
border: 1px solid #999999;
font-weight: bold;
overflow: auto;
}
</style>
</div>
<a href="#" onclick="history.back();return false;">Return to previous page</a>
</div>
</body>
</html>
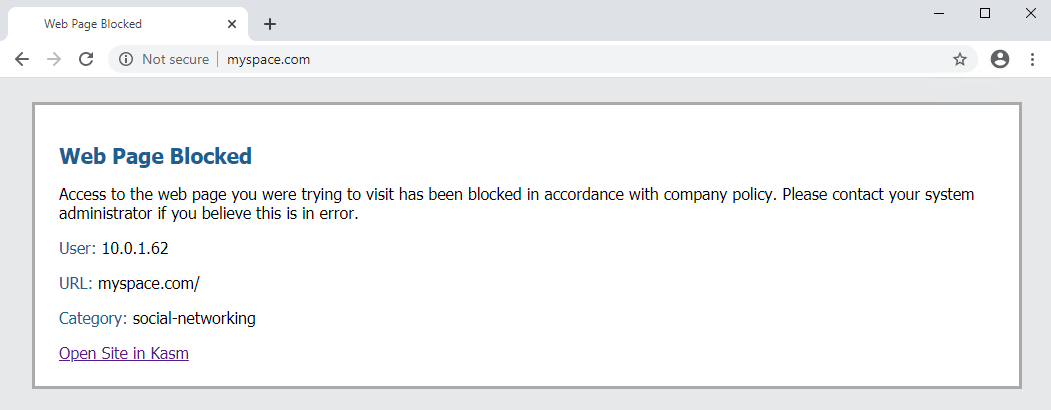
Custom Response Page with Link to Kasm
Kasm Squid
Squid is an open source forward proxy. We have developed a containerized version of Squid for proxy redirection. This project is open source and located at https://bitbucket.org/kasmtech/kasm_squid/src/master/
Installation
Clone the repository at https://bitbucket.org/kasmtech/kasm_squid/src/master/
Run the install redirector script with the Kasm Workspaces url after the -k argument
sudo ./install_redirector.sh -k https://kasm.company.internal
Download myCA.der from /srv/kasm_squid/ssl_cert/myCA.der
For most browsers, windows settings can be used for the proxy settings.
Setup Root CA Trust
Use the windows key + r shortcut to open the run prompt
Type in secpol.msc and click OK
Select public Key Policies from the Security Settings
Open the Certificate Path Validation Settings window
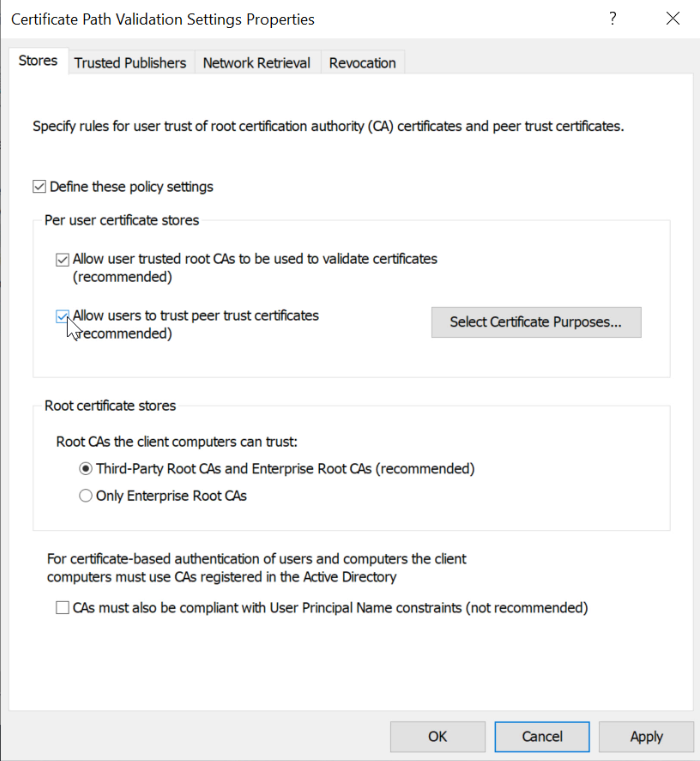
Check Define these policy settings
Make sure to select all of these
Allow user trusted root CAs to be used to validate certificates
Allow users to trust peer trust certificates
Third-Party Root CAs and Enterprise Root CAs
Select apply
Use the windows key + r shortcut to pen the run prompt
Type in certmgr.msc and click OK
Expand Trusted Root Certification Authorities
Right click certificates -> all tasks -> import
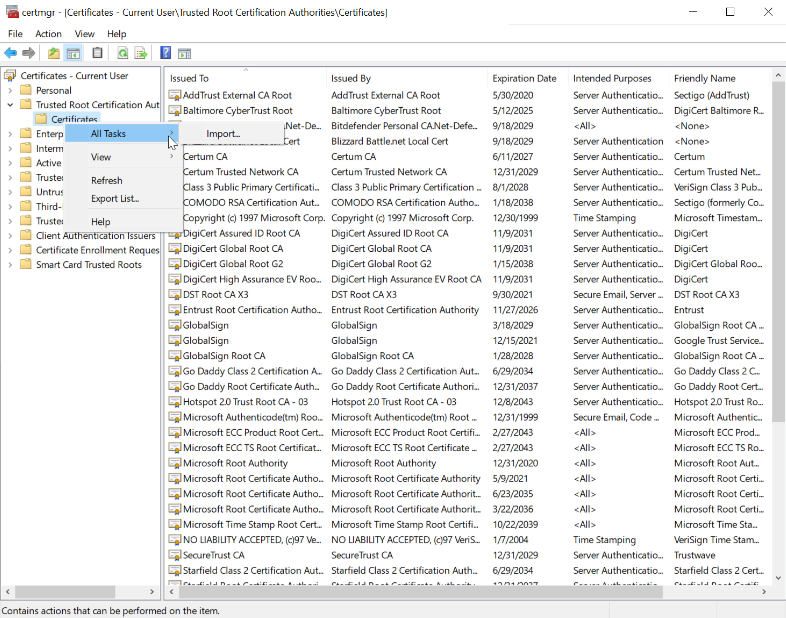
Browse to the certificate and select open
Click next, next and finish
Setup proxy in windows settings
Open Windows settings and select Network and Internet
Select proxy at the bottom left
Under manual proxy setup select Use a proxy server
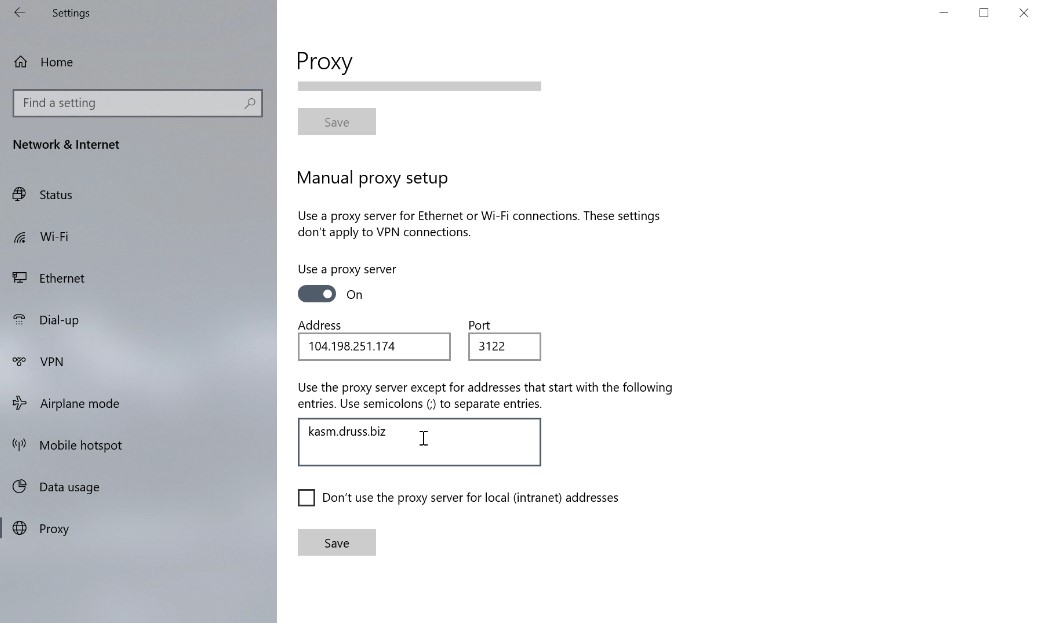
Enter the Kasm proxy server address and port 3122
Enter the Kasm domain into the excluded proxy addresses
Select save
For browsers like Edge, Chrome and Internet Explorer the proxy should be up and working. Firefox will need to be configured separately.
Setup Firefox
In the Firefox options select privacy and security
Scroll to the bottom and click View Certificates
Import myCA.der from the Kasm Proxy
Check all boxes and click OK
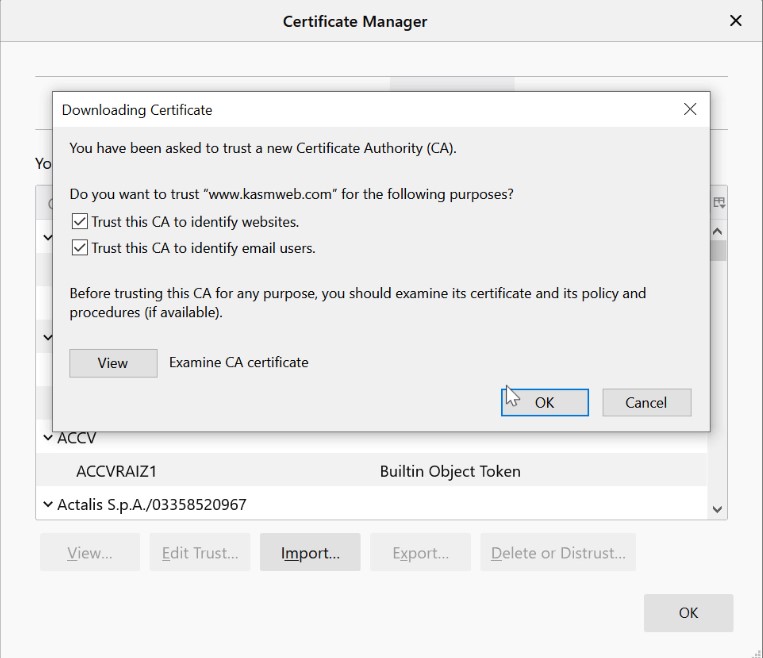
Navigate to the General tab
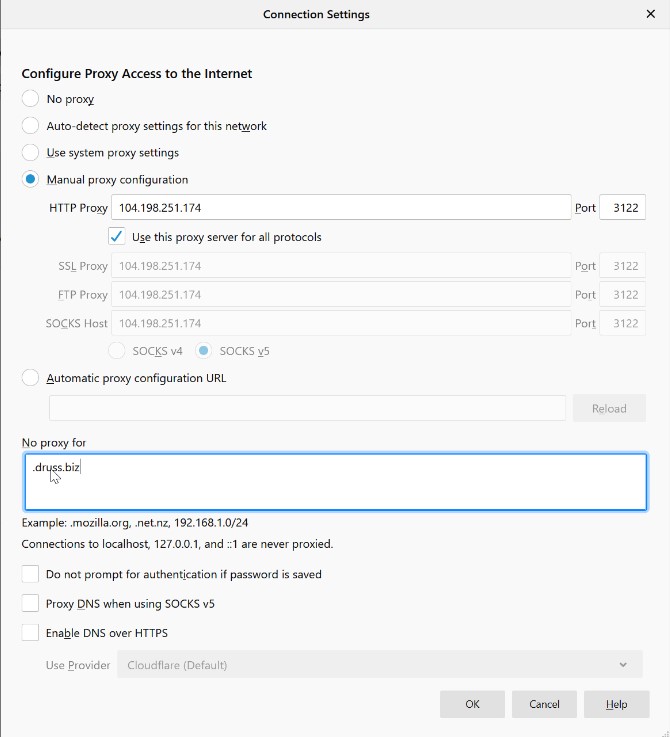
Scroll to the bottom for Network Settings
Select Manual proxy configuration
Input the IP address of the squid server and port 3122
Select Use proxy for all protocols
Add in the Kasm Workspaces domain name under no proxy for
Select OK
Firefox will now redirect all traffic through the secure Kasm.
Troubleshooting
If the browser is not connecting to the proxy make sure to open port 3122 on the proxy server.
If the Kasm seems to be reconnecting make sure the browser is configured to not use the proxy settings for the Kasm Workspaces server as Squid does not handle websockets.
If HTTPS or security warning errors are occurring, ensure the root certificate is installed on the browser.
Ensure that the proxy was installed using the domain name for the actual Kasm Workspaces server.