Reverse Proxy¶
Overview¶
Administrators may desire to run Kasm Server behind a reverse proxy such as Nginx or Caddy . A handful of configurations are required for communication to properly flow between the proxy and Kasm.
Important
Once Kasm is placed behind a reverse proxy, be sure to update the Zone configuration. See Update Zones.
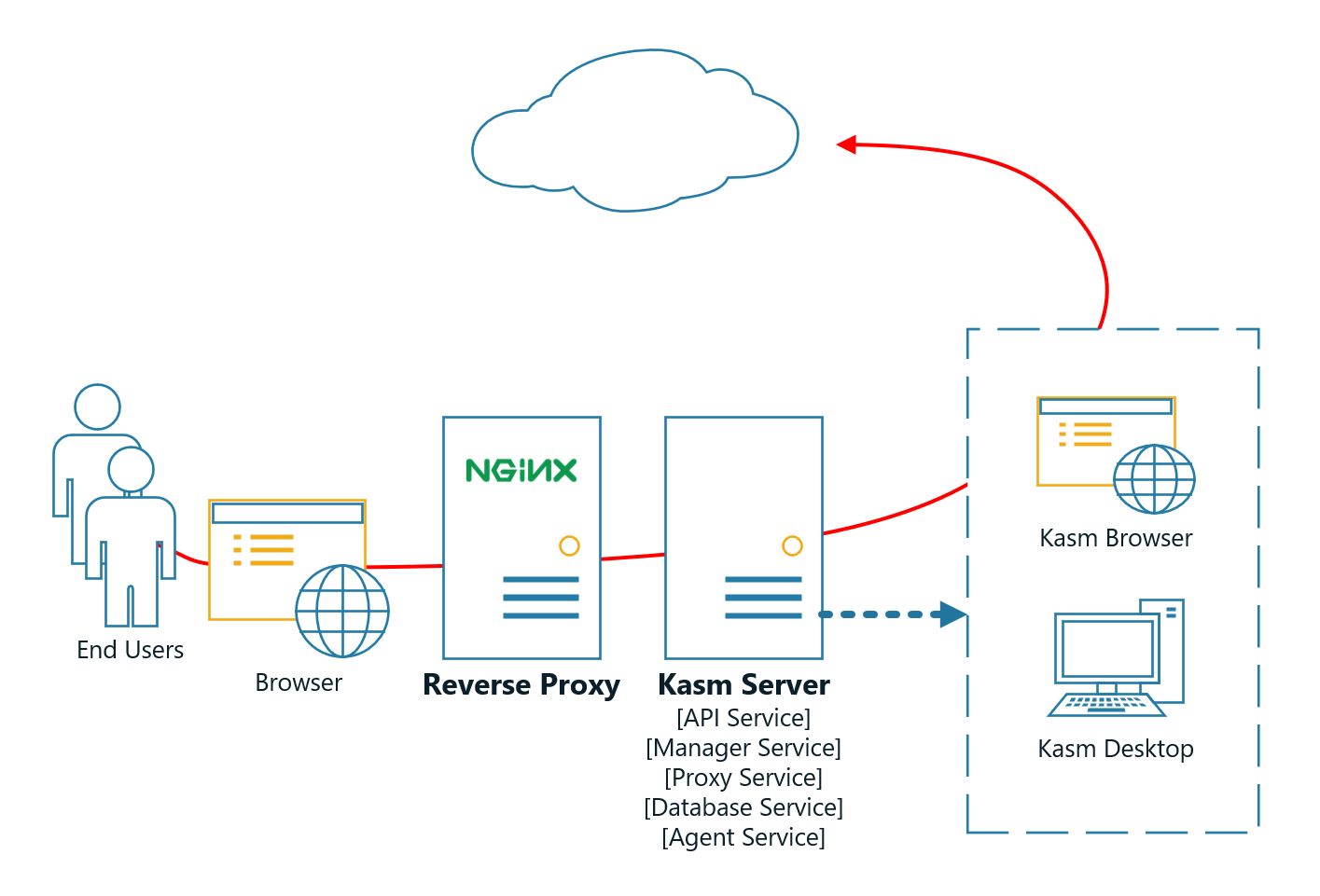
Kasm Server Behind a Reverse Proxy¶
Running Kasm Server on a Non-Standard Port¶
By default, Kasm Server will listen on port 443. Administrators may wish to run the application on another port so that the revere proxy can run on port 443.
During the installation pass the -L flag to choose a different port.
e.g sudo bash kasm_release/install.sh -L 8443
Users will now access Kasm Server via the defined port https://kasm.server:8443
Example Nginx Config¶
Below is an example Nginx config with the appropriate settings for Kasm annotated. In this example, Nginx is listening on port 443 and Kasm Server is listening on port 8443
server {
listen 443 ssl;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
location / {
# The following configurations must be configured when proxying to Kasm Server
# WebSocket Support
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
# Host and X headers
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
# Connectivity Options
proxy_http_version 1.1;
proxy_read_timeout 1800s;
proxy_send_timeout 1800s;
proxy_connect_timeout 1800s;
proxy_buffering off;
# Allow large requests to support file uploads to Kasms
client_max_body_size 10M;
# Proxy to Kasm Server running locally on 8443 using ssl
proxy_pass https://127.0.0.1:8443 ;
}
}
Multiple Server Names¶
Kasm Server does not support being proxied to using alternate paths, (e.g https://example.com/kasm/). If
Administrators desire to run multiple applications behind Nginx, it is recommended to use a dedicated server_name
for traffic destined for Kasm. (e.g https://kasm.example.com/). See
Nginx Server Names documentation for more details.
server {
listen 443 ssl;
server_name app1.example.com;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
location / {
return 200 'App 1';
add_header Content-Type text/plain;
}
}
server {
listen 443 ssl;
server_name kasm.example.com;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
location / {
# The following configurations must be configured when proxying to Kasm Server
# WebSocket Support
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
# Host and X headers
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
# Connectivity Options
proxy_http_version 1.1;
proxy_read_timeout 1800s;
proxy_send_timeout 1800s;
proxy_connect_timeout 1800s;
proxy_buffering off;
# Allow large requests to support file uploads to Kasms
client_max_body_size 10M;
# Proxy to Kasm Server running locally on 8443 using ssl
proxy_pass https://127.0.0.1:8443 ;
}
}
Example Caddy Config¶
Below is an example Caddyfile with the appropriate settings for Kasm annotated. In this example Caddy is listening on port 443 and Kasm Server is listening on port 8443
192.168.117.130:443
tls self_signed
log stdout
# Proxy to Kasm running locally on port 8443
proxy / https://localhost:8443 {
# By default Kasm Server installs with self-signed certificates. If these are not replaced
# then Caddy must be instructed to skip verification of these certs.
insecure_skip_verify
# WebSocket Support
header_upstream Connection {>Connection}
header_upstream Upgrade {>Upgrade}
# Host and X headers
header_upstream Host {host}
header_upstream X-Real-IP {remote}
header_upstream X-Forwarded-For {remote}
header_upstream X-Forwarded-Port {server_port}
header_upstream X-Forwarded-Proto {scheme}
}
Update Zones¶
In order for clients to properly make connections to Kasm sessions when using a reverse proxy, the Upstream Auth Address and Proxy Port settings for each Deployment Zone must be updated. Update the Proxy Port setting with the port the Reverse Proxy is listening on. For example, if the reverse proxy is listening on 443 this setting must reflect that. Update the Upstream Auth Address with the IP or FQDN of the Kasm Server if using a single-server installation or if using a multi-server deployment , using the the IP or FQDN of the WebApp role for that Zone.
Log into the Kasm Server UI as an administrator
Select Zones.
Edit the default Zone.
Change the Upstream Auth Address setting to the IP or FQDN of the Kasm Server.
Change the Proxy Port setting to the port of the reverse proxy.
Repeat for each additional Zone.

Updating the default zone¶